Depending on how you use it, ChatGPT can be safe. However, to protect yourself and your data, you should be aware of some security risks. These
Updated on November 28, 2023.
A VPN, or a virtual private network, is a service that protects your internet connection and online privacy. It works by encrypting your internet connection, masking your IP address and allowing you to use public WiFi hotspots safely. A VPN creates a private, encrypted network within the public network providing an extra layer of security and privacy. It can help prevent cybercriminals from collecting your data to sell on the dark web or using it for targeted cyber attacks against you.
Continue reading to learn more about how a VPN works, the different types of VPNs, the benefits of using one and how it improves your cybersecurity posture.
How Does a VPN Work?
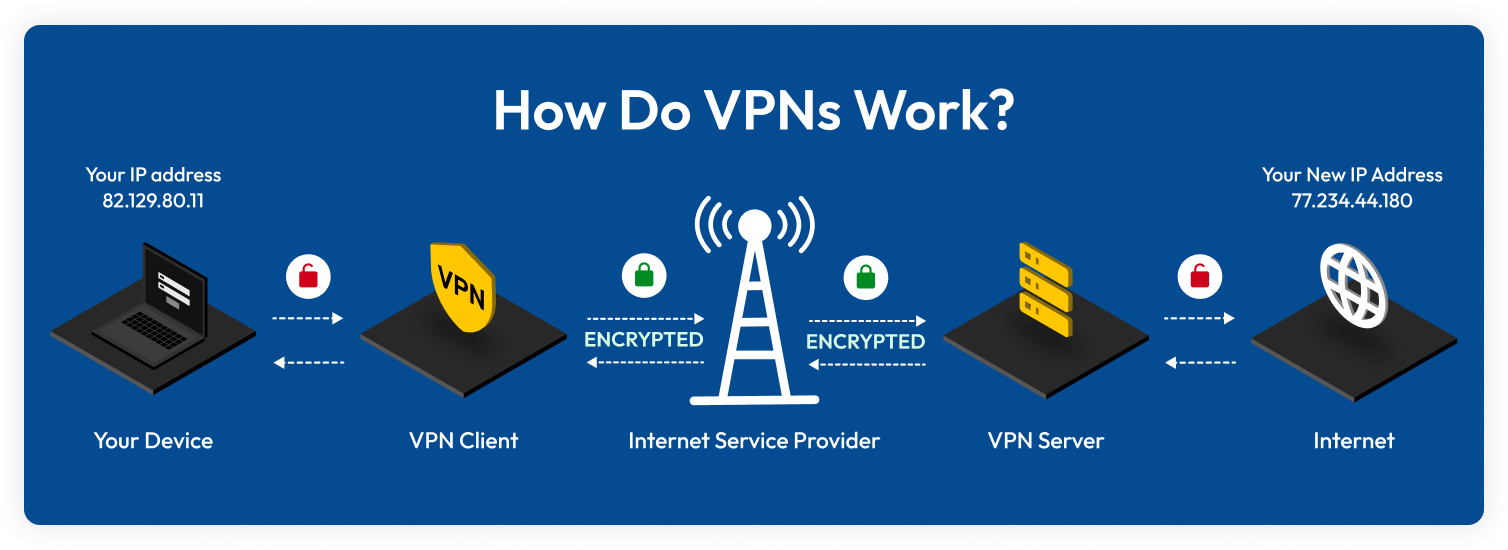
A VPN works by securely and anonymously connecting the user to a server. Without a VPN, a user connects straight to the internet through the Internet Service Provider (ISP) without any protection. However, with a VPN, the user connects to a VPN client, which then routes their internet traffic to the VPN server through an encrypted connection known as a tunnel. Then, the VPN server transmits the user’s internet traffic to the internet under the VPN server’s IP address.
Routing internet traffic through a VPN server creates an encrypted tunnel that allows users to securely connect to the VPN server. It prevents the ISP and any other third parties from seeing your data since the internet traffic is encrypted and only the user and the VPN server have the decryption key.
A VPN also masks the user’s IP address because the IP address of the VPN server is used to access the internet instead of the user’s actual IP address.
What Are the Types of VPNs?
Different types of VPN services link you to a VPN server. A server stands between your device and your desired web service.
Personal VPN
A personal VPN, also known as a “consumer” or “commercial” VPN, refers to services meant for personal use. Reputable personal VPNs encrypt your connection and hide your online identity. They allow you to change your geographical location, ensuring your security isn’t compromised.
Remote access VPN
A remote access VPN, also called a client-based VPN or client-to-server VPN, enables you to connect your device to a private network outside your organization’s office. VPN encryption is used to protect and secure data as it travels to and from the private network.
Site-to-site VPN
A site-to-site VPN connects multiple networks in different locations. For example, if a company has two office locations, a site-to-site VPN could be used to connect them to the central office location. This type of VPN is often used by organizations with several locations in different parts of a country or the world.
Mobile VPN
A mobile VPN may be the best option if you don’t have a stable connection on the same network for the duration of your session. With a mobile VPN, the connection is maintained even if you change WiFi or cellular networks, lose your connection or turn off your device.
What Are the Benefits of Using a VPN?
A VPN allows you to safely use the internet by creating an encrypted connection for your data, making your online activity untraceable. Here are the benefits of using a VPN.
Secure connection
If your data is transmitted through an unsecured network such as public WiFi, cybercriminals can access your data. Cybercriminals can use your data to send targeted phishing attacks and attempt to steal your personal information. Commonly, they use Man-in-the-Middle (MITM) attacks that rely on unsecured or fabricated networks to intercept communications and steal sensitive data.
A VPN creates a secure internet connection that is encrypted, making the transmitted data unreadable to anyone trying to spy on you. This allows you to securely access sensitive data such as your financial information or login credentials without any unauthorized access. A VPN will protect you from some types of MITM attacks since your internet connection is encrypted and the data you send can’t be seen by cybercriminals.
Remain anonymous online
Websites and applications can track your online activity without your knowledge. Third parties try to collect your data and gather information about you. Cybercriminals use this collected data to either sell on the dark web or send targeted phishing attacks.
A VPN will keep your online activity anonymous by masking your IP address. With a VPN, the VPN server’s IP address is used instead of the user’s IP address. This makes the user’s online activity untraceable and not able to be collected by adware or cybercriminals.
Avoid bandwidth throttling
Bandwidth throttling happens when your internet speed is intentionally slowed down by your ISP or someone else who has control over how your WiFi network performs, such as a network administrator. Bandwidth throttling typically occurs with data-intensive activities like gaming, streaming and downloading large files online. Throttling can also happen when you reach your data usage limit.
Because bandwidth throttling is sometimes triggered by the sites you visit or the type of activity you engage in, if your ISP cannot see the data flowing to and from your device, they cannot throttle it. A VPN will help prevent bandwidth-throttling since it hides your traffic from your ISP.
Will a VPN Keep Me Safe Online?
Although VPNs will protect your online activity from unauthorized users, you shouldn’t rely on them exclusively to stay safe online. VPNs only provide limited protection against cybercriminals. While VPNs protect you against some types of MITM attacks, they don’t protect against all of them. VPNs will not protect you from other cyber threats like malware and social engineering. You need to exercise cybersecurity best practices and use additional cybersecurity solutions to remain safe online.
Use strong and unique passwords
You need to use strong and unique passwords to protect your online accounts. A VPN can encrypt your data, but it won’t protect your online accounts from password-related attacks. A VPN protected by a weak password can be susceptible to password-related attacks such as brute force attacks. Brute force attacks are a type of cyber attack that uses trial and error to guess a user’s login credentials.
You need to use strong and unique passwords to make it difficult for cybercriminals to crack your passwords, especially the password for your VPN. A strong password is a unique combination of uppercase and lowercase letters, numbers and special characters that is at least 16 characters long. It omits any personal information, sequential numbers or letters and commonly used dictionary words.
With so many online accounts, it can be difficult to remember all of your strong and unique passwords. That’s why you need a password manager. A password manager is a tool that securely stores and manages your personal information inside an encrypted vault. It helps you strengthen your passwords by identifying any weak passwords. It also helps you create strong passwords using a built-in password generator. You can easily and securely log into your online accounts with a password manager.
Install antivirus software
Although a VPN creates a secure connection and hides your data, it won’t protect you from malware infecting your device. Malware can be delivered from malicious attachments or websites. These malicious attachments and websites install malware on your device when a user clicks on them. You need to have antivirus software to protect yourself from malware attacks. Antivirus software prevents, detects and removes known viruses and malware from your device before they infect it.
Enable MFA
Multi-Factor Authentication (MFA) is a security measure that requires you to verify your identity by providing additional forms of authentication. Before you can gain access to your account, you need to provide your login credentials and proof of your identity such as biometric authentication or a one-time code.
MFA provides an extra layer of security to your online accounts and prevents cybercriminals who have compromised your login credentials from gaining access to your accounts. You should enable MFA on all your online accounts to protect them from cybercriminals, especially on your VPN.
Recognize phishing attempts
A VPN will not protect you from phishing attacks and other similar types of scams. A phishing attack is a type of cyber attack that tries to trick users into revealing their personal information. Cybercriminals send messages with a malicious link or attachment with the intent for you to click on it. Once you click on the malicious link, you are taken to a spoofed website that either installs malware or tricks you into revealing your personal information.
You need to learn how to recognize phishing attempts to protect your personal information. Some of the signs of phishing attempts to look out for are suspicious senders, unsolicited links or attachments, urgent requests for sensitive information, and spelling or grammatical errors.
A VPN Alone Is Not a Cybersecurity Solution
You should use a VPN to create a secure connection and make your online activity untraceable to others. However, you should not rely on a VPN alone to keep you safe online. A VPN can only protect your internet traffic from unauthorized access. A VPN will not protect you from cyber attacks such as malware or phishing attacks. You need to implement cybersecurity best practices and invest in cybersecurity solutions such as a password manager.
A password manager will help protect your personal information such as your login credentials, credit card numbers and other sensitive information from cybercriminals. It will help protect your personal information from falling into the wrong hands. Together, a VPN and a password manager can protect your online data from cybercriminals and help you prevent security breaches.
Keeper® Password Manager offers a secure password management solution that protects your personal information using zero-trust and zero-knowledge encryption. This ensures that only you have access to your personal information. Sign up for a free trial to start protecting your online data.
 Cybersecurity
Cybersecurity 
