Eliminate secrets sprawl and protect Non-Human Identities (NHIs) with Keeper Secrets Manager
Zero-trust, zero-knowledge secrets management with unmatched ease of deployment and control.
Zero-trust, zero-knowledge secrets management with unmatched ease of deployment and control.
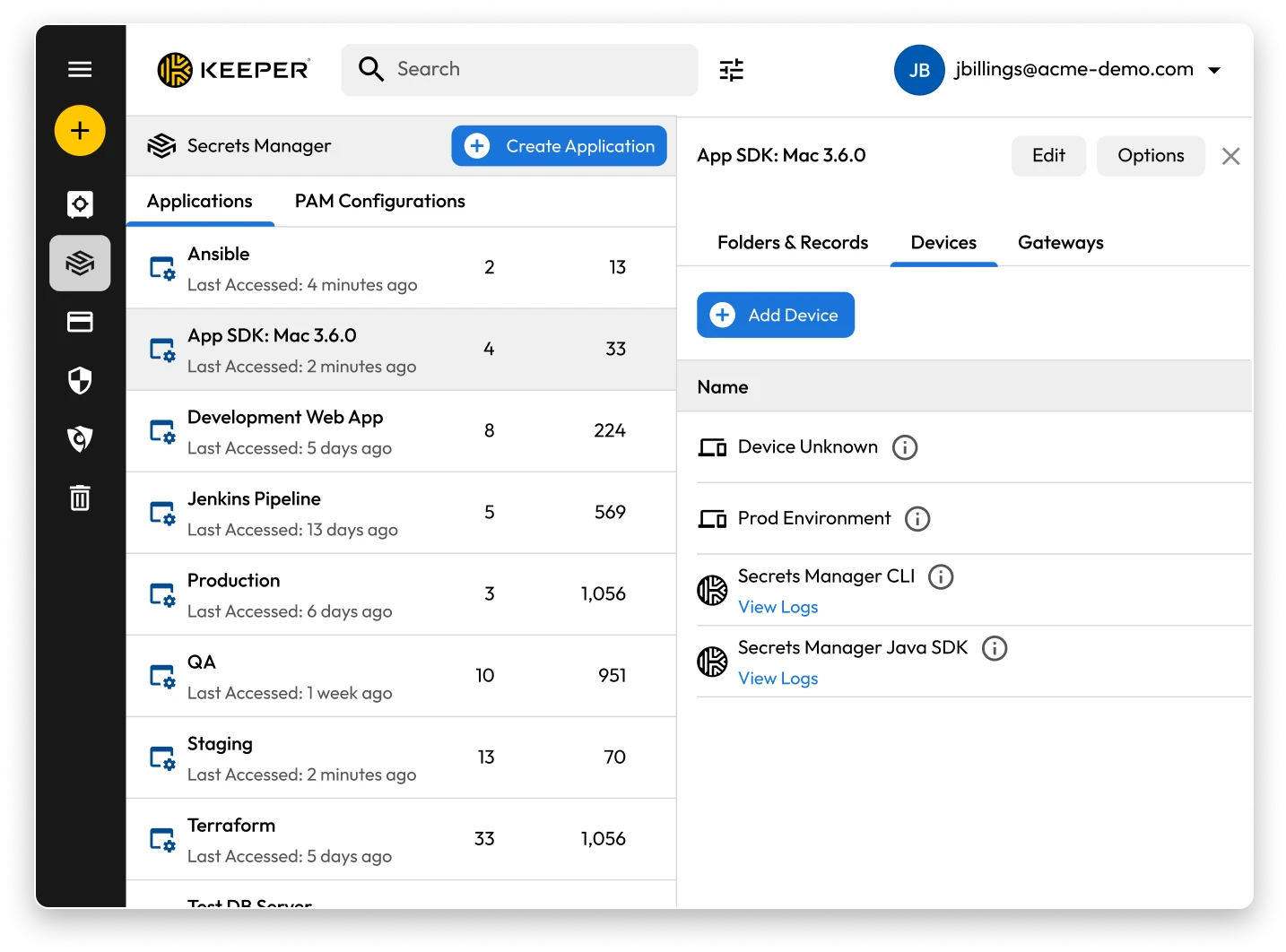
Keeper Secrets Manager is a fully managed, cloud-based secrets management solution that eliminates secrets sprawl and helps DevOps teams protect sensitive credentials in CI/CD pipelines, containers, automation scripts and cloud infrastructure.
The Admin Console centralizes Role-Based Access Controls (RBAC), provisioning, reporting, auditing and user management in a single, secure interface. Administrators can easily configure Keeper Secrets Manager, enforce policies and maintain full visibility across the organization.
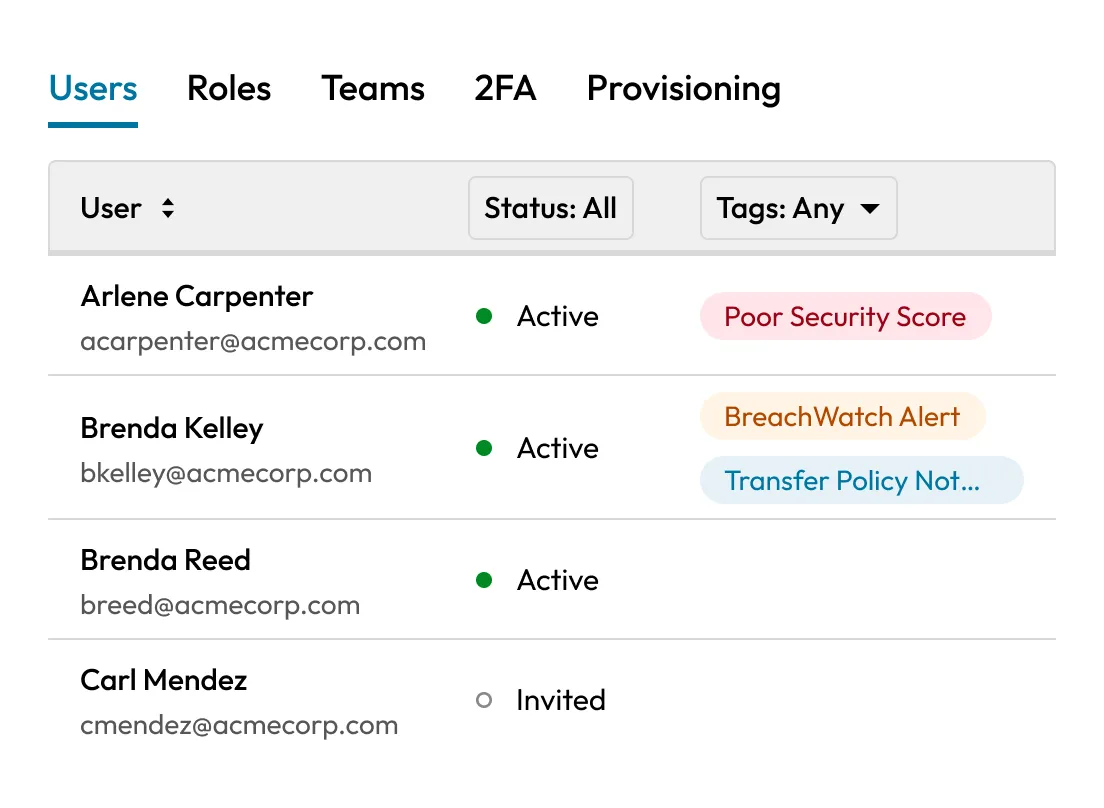

Apply role-based access policies, enforce least privilege and monitor every secret access event in real time. Keeper integrates with Security Information and Event Management (SIEM) platforms for centralized visibility and compliance reporting.
Reduce risk from exposed or stale credentials with automated rotation for SSH keys, service accounts, API tokens and database passwords. Keeper supports time-based and event-driven rotation across cloud and on-prem environments.
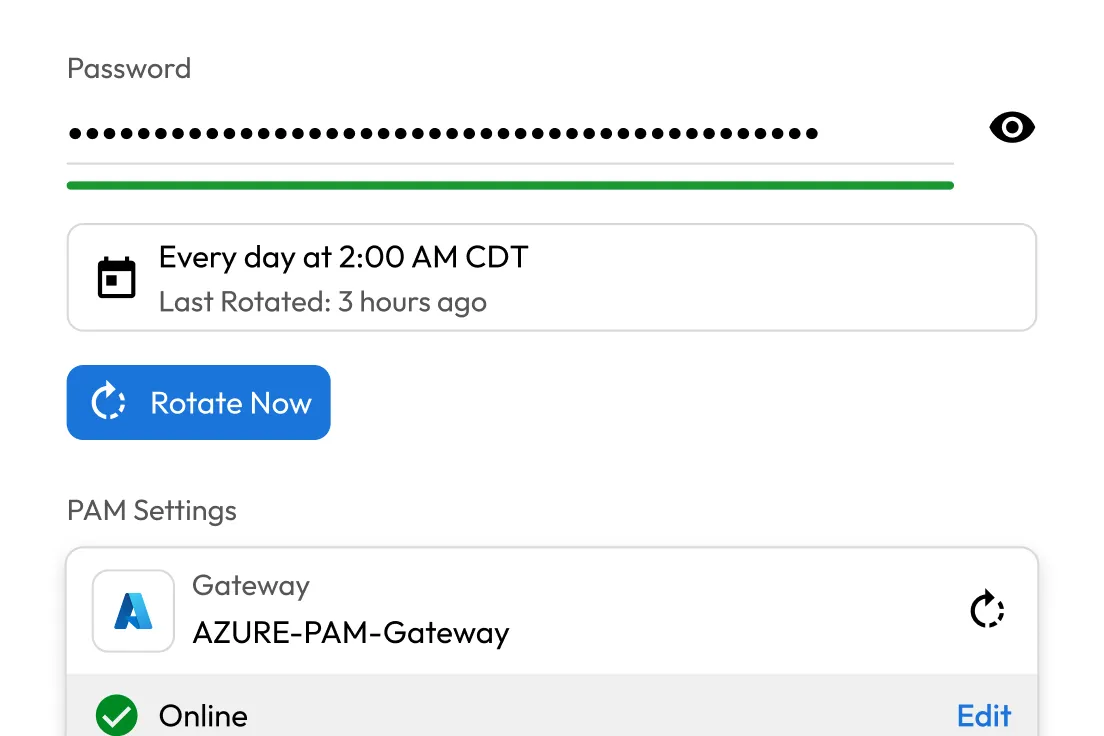
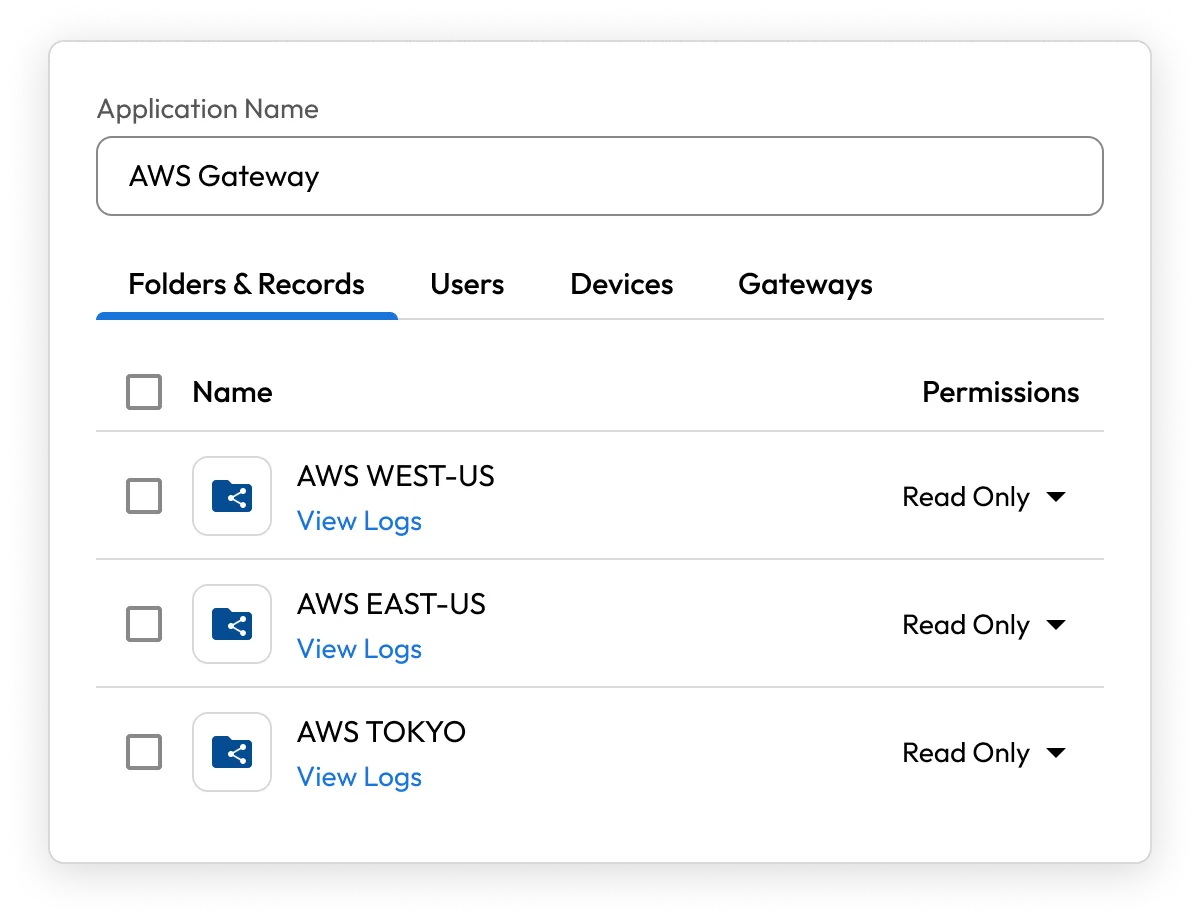
Enable teams to work faster by securely sharing records and IT configurations across users, roles and environments. From database connection strings to API keys and server logins, sharing is instant, permissions-based and fully auditable.
Keeper is a fully managed, cloud-based secrets manager built for simplicity and security. There's no hosted software to maintain, no complex VPC peering to configure and no additional infrastructure to deploy.
With millions of users and thousands of enterprise customers, Keeper is available on any device, anywhere.
Keeper provides a superior zero-knowledge encryption model designed to ensure that only you can access your vault. Secrets can be decrypted only on the designated devices that you manage.
Keeper integrates natively with popular DevOps tools like GitHub Actions, Jenkins, Terraform, Kubernetes, Docker and more. Access secrets securely via SDKs, RESTful API or Keeper Commander CLI, no hard-coded credentials required.
Secure secrets used by scripts, applications and microservices — without exposing credentials in configuration files or containers. Keeper manages machine-to-machine authentication with the same rigor as human access.
Deploy Keeper across AWS, Azure, Google Cloud and hybrid environments with full support for multi-region availability, global compliance and distributed teams. Secrets remain secure and accessible wherever your workloads run.
Eliminate hard-coded credentials, secure your infrastructure and automate secrets management — all within a zero-trust, zero-knowledge platform.
Secrets as a Service, also known as secrets management, is a software platform that manages secrets separately from the applications they provide access to. Rather than hardcoding secrets or saving them in config files, secrets are stored in and retrieved from a secrets management platform.
Secret management tools are software platforms that allow companies to store, transmit and manage digital authentication credentials, like passwords, SSH keys, API keys, TLS/SSL certificates, tokens, encryption keys, privileged credentials and other secrets.
Secrets management tools provide centralized visibility, oversight and management of a business's credentials, keys and secrets across the organizational data environment, reducing the risks of secrets misuse or compromise.
Secrets management is extremely important in DevOps environments, where common CI/CD pipeline tools such as Jenkins, Ansible, Github Actions, and Entra ID (Azure) DevOps use secrets to access databases, SSH servers, HTTPS services, and other sensitive systems. These secrets are either stored in a config file for the deployment system or in one of a dozen different storage vaults, all of which provide wildly different capabilities depending on the product. In a scenario where admins aren’t storing credentials in config files or systems, they’re likely being stored in their DevOps environments, and admins may or may not have any auditability or alerting on usage of these secrets.
You must accept cookies to use Live Chat.