Ransomware
Ransomware encrypts files and locks users out of their devices, demanding a ransom in exchange for restored access. These attacks can disrupt operations and may result in permanent data loss if backups or decryption keys are unavailable.
Cyber Threat: Malware
Malware, short for malicious software, is any program or code created to gain unauthorized access to devices, networks or sensitive data. Cybercriminals use malware to steal credentials, spy on users, encrypt files for ransom or remotely control systems without detection.

Ransomware encrypts files and locks users out of their devices, demanding a ransom in exchange for restored access. These attacks can disrupt operations and may result in permanent data loss if backups or decryption keys are unavailable.

Trojan horses are disguised as legitimate software to trick users into installing them. Once inside, Trojans can exploit security vulnerabilities, steal sensitive data or download additional malware without the user's knowledge.

Spyware secretly monitors user activity to gather sensitive information, such as passwords and financial details. It silently sends stolen data to cybercriminals in the background, making it challenging to detect.
Viruses are malware that latch onto legitimate files and spread when those files are opened or shared. They can corrupt data and spread across devices and networks, causing further damage.
Phishing emails or messages appear to come from trusted sources, deceiving users into clicking malicious links or opening infected attachments.

Spoofed websites are made to look like legitimate sites, often using similar URLs or branding to trick users into entering login credentials or downloading malware.
Once an infected file or app is downloaded and opened, malware can install itself and start stealing data or damaging systems.
A sudden slowdown in performance is one of the earliest signs of malware. Malware consumes resources while running in the background, causing apps to lag, freeze or crash more frequently than normal.

Malware often runs hidden processes that strain a device's CPU, leading to loud fan activity, overheating and unusually fast battery drain.
An increase in pop-up ads or random browser redirects may indicate a malware infection. Pop-ups often appear outside of normal browsing activity and may lead users to spoofed websites.
Phishing emails and messages are the most common ways malware is delivered. Watch for suspicious senders, urgent language and unsolicited requests for personal information to avoid opening malicious links or attachments.
Outdated software typically contains security vulnerabilities that cybercriminals exploit using malware. Regularly installing updates and patches helps close these gaps and reduce the risk of infection.
Malicious links and attachments can install malware as soon as they're opened. Never download files or click links from unknown sources, especially messages that urge you to act quickly.
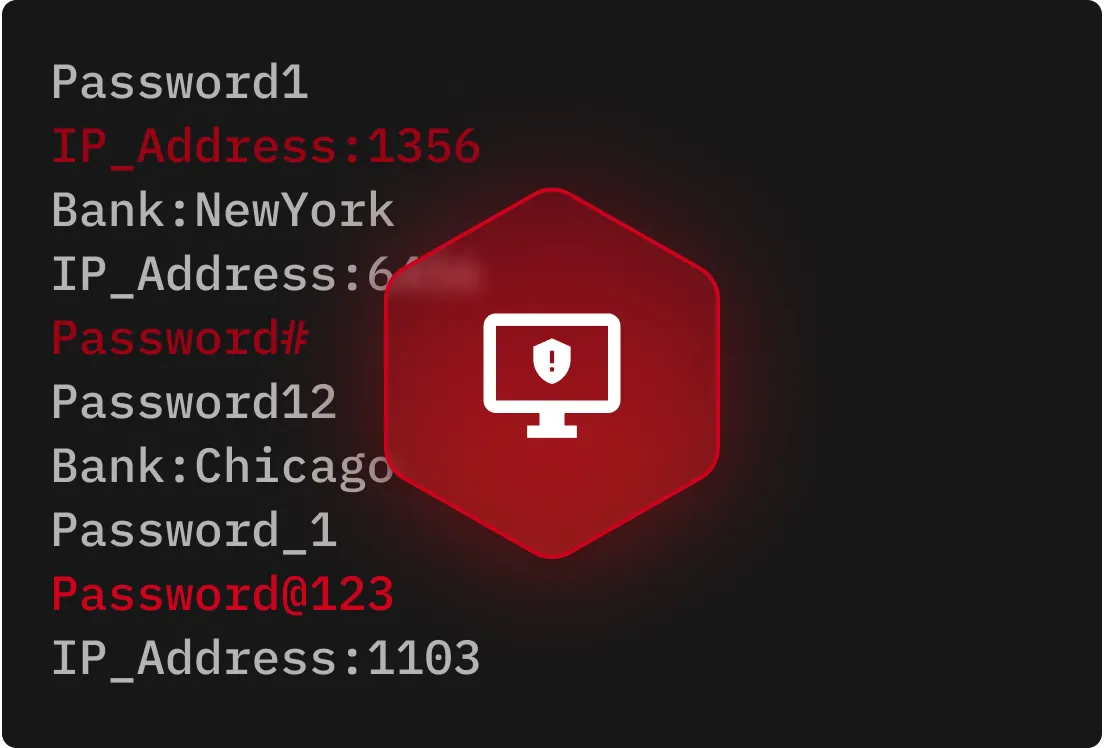
Weak or reused passwords make it easy for malware to steal credentials. Using a secure password manager like Keeper® helps protect login credentials with strong encryption.
Businesses can use Keeper's Endpoint Privilege Manager to enforce least-privilege access, helping to prevent users from installing or running malware. By controlling privilege elevation, organizations reduce the risk of malware gaining access to critical systems.
You must accept cookies to use Live Chat.