Get Credential Governance with Role-Based Access Control
Protect your Passwords with Role-Based Access Controls and Zero-Trust Security.
Request a DemoThe Principle of Least Privilege
Organizations are often faced with the challenge of providing their employees with the credentials and access required to perform their jobs efficiently, while excluding access to other unnecessary confidential information.
The principle of least privilege (PoLP) is when an admin restricts the levels of access and permissions to the minimum required to carry out job functions. This principle ensures that employees only have access to what is necessary to them – not complete access to the organization's entire network.
PoLP reduces the attack surface by eliminating unnecessary privileges that could be exploited by either a malicious insider or an outside threat actor who is able to compromise an employee’s credentials. If proper credential governance and security mechanisms aren’t in place, your organization's security is at risk.
Control Organization Access Levels with Nodes, Roles and Teams
The ability to provide least-privilege access to all users is a critical component of enterprise password management. Keeper allows administrators to fine-tune their organization's access levels to sensitive data and credentials, from teams and groups down to the individual user level.
This key feature works seamlessly with Keeper’s superior architecture, composed of Nodes, Roles and Teams.
Nodes
Nodes are a way to organize users into distinct groupings, similar to organizational units in Active Directory, and are at the core of Keeper’s architecture. The administrator can create nodes based on location, department, division or any other structure. By default, the top-level node – or root node – is set to the organization name and all other nodes can be created under the root node.
One advantage of defining multiple nodes is to help support the concept of delegated administration. A delegated administrator can be granted some or all of the administrative permissions, but only over their respective node or sub nodes.This delegated administration allows different people in the organization to manage controls over subsets of teams, users, roles and shared folders.
Roles
Roles define permissions, control which features and security settings apply to which users, and manage administrative capabilities. Users are provisioned under their respective nodes, with their roles configured to match the specific needs of the business.
Roles are made up of enforcement policies and control how users are able to access the Keeper Vault on their devices. Any number of role policies can be created and applied to one or more users.
Teams
Teams are used for sharing privileged accounts and shared folders among groups of users within the Keeper Vault. Teams can also be used to easily assign roles to entire groups of users to ensure the consistency of enforcement policies.
Since Keeper's security model is based on least-privilege access, we implement least-privilege policies, so when a user is a member of multiple roles, their default policy is the most restrictive.
Meet the Needs of Your Internal Controls with Role-Based Enforcement Policies
Keeper gives your organization fine-grained control and visibility over what information users are capable of accessing and managing from within the platform, using customizable role-based access controls (RBAC). By providing a flexible role policy engine, you can lock down restrictions and access based on the risk profile of an individual user.
For example, you may want your IT Admins to be restricted from accessing their vault outside of the office network. Or you may want administrative assistants to have the ability to onboard new users, manage teams and run reports. The entire process is fully customizable through a user-friendly interface.
From the console, administrators have access to a robust collection of Enforcement Policies that control how users access and interact with the vault and which features they can use.
Features include:
- Password Complexity Rules and Biometrics
- Multi-Factor Authentication, Token Expiration and Device Restriction
- Offline Access Restrictions
- Allow IP Listing, Sharing and Data Export Restrictions
- Account Transfers (employee offboarding and break-glass scenarios)
- Administrative Permissions
Keeper's Node Architecture Scales to Any Size Organization
Fully appreciating the power and flexibility of Keeper's role-based access controls requires an understanding of the organizational structure that is implemented when deploying Keeper in your organization.
The business security landscape is constantly evolving, requiring ease of use and flexible internal safeguards. Keeper is designed to scale to any size organization. Features such as role-based permissions, team sharing, departmental auditing and delegated administration support your business as it grows and changes. When employees take on new job responsibilities or change positions, Keeper updates their roles through Active Directory, ensuring they always have the correct permissions.
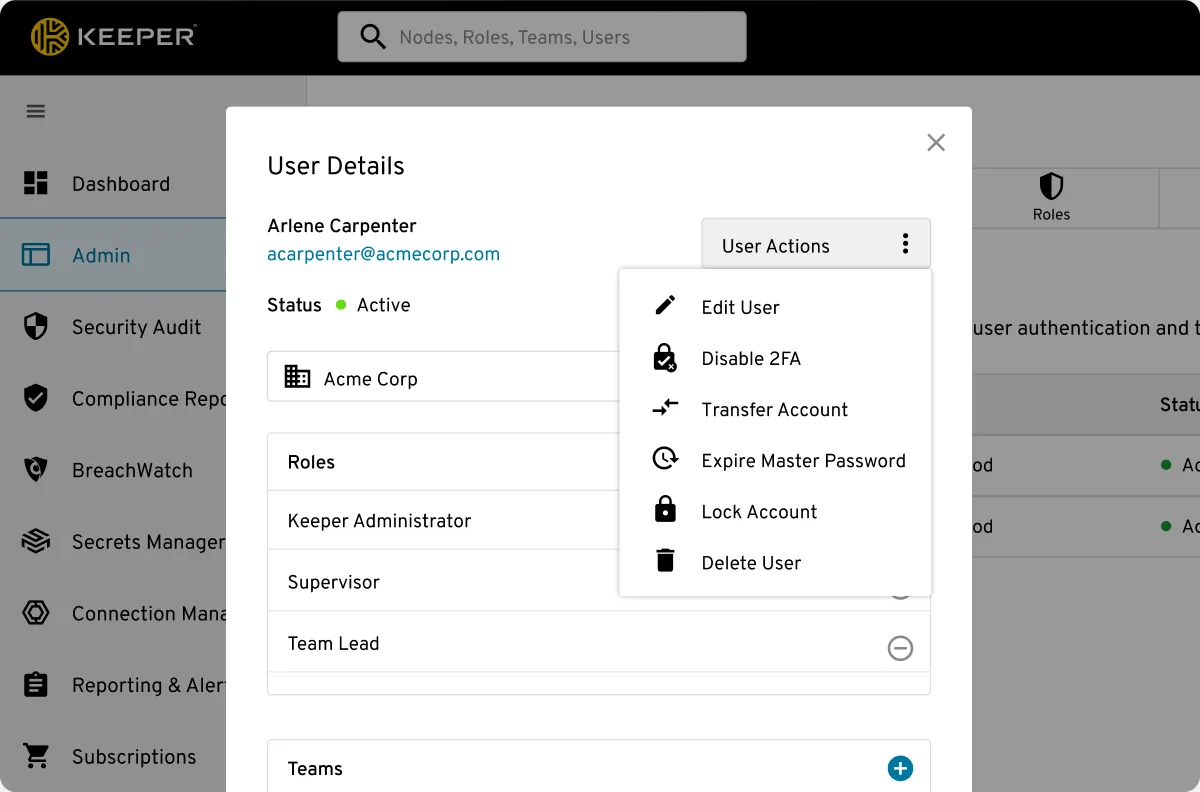
Eliminate the Risk of Critical Data Loss When Employees Leave the Organization
Keeper's zero-knowledge account transfer capabilities provide enterprise customers with peace of mind that an employee will never walk away with critical data when they leave the organization.
Through the use of Keeper’s secure "Account Transfer" feature, a user's vault can be locked, then transferred to another user within the organization. The process of account transfer remains fully zero knowledge, and the responsibility of performing account transfers can be limited based on the roles created.
For example, IT administrators can ensure that only the engineering manager can transfer the vault of an engineer, or the marketing manager can only transfer the vault of a marketing coordinator.
Resources
Frequently asked questions
What is RBAC (role-based access control)?
Role-based access control, also known as role-based security, is an access control model where a user’s role within an organization determines which network resources they have access to. The goal of RBAC is to ensure that users cannot access systems and data that are unrelated to their job functions, enhancing compliance, preventing data leakage and in the event that a user’s credentials are compromised, hampering the ability of a threat actor to move laterally within the network.
What is privileged access management?
Privileged access management (PAM) refers to the tools and technology organizations use to secure, control and monitor access to their most critical information and resources, such as local and domain administrative accounts. PAM helps organizations protect themselves from cyber attacks as it prevents unauthorized privileged access to accounts.
RBAC vs ABAC
The main difference between role-based access control (RBAC) and attribute-based access control (ABAC) is how each method provides network access. RBAC enables you to grant role-based access. ABAC allows you to grant access through user characteristics such as action types, location, device and more.