Enhance and Extend Your SSO Solution With Keeper SSO Connect*
*Included with Keeper Enterprise
*Included with Keeper Enterprise
Keeper SSO Connect® integrates with all popular SSO IdP platforms, including Office365, Entra ID (formerly Azure AD), ADFS, Okta, Ping, JumpCloud, Centrify, OneLogin, F5 BIG-IP APM, Google Workspace, Duo and any other SAML 2.0 identity provider.



Keeper SSO Connect unlocks a simplified login experience for your users and one-click provisioning for administrators.
Enhance your SSO deployment with secure, streamlined access to every work application.
With Keeper SSO Connect, users enjoy a simplified login experience that uses their identity provider (IdP) for federated login and to authenticate into their Keeper Vault.
Keeper SSO Connect is compatible with Conditional Access Policies (CAP) enforced by the IdP and accelerates time to value for admins by mapping over existing groups from your IdP.
Combining Keeper's robust password and passkey management with your IdP's capabilities enhances security by ensuring that every website, application and service is easy to access and securely managed. Keeper auto-fills passwords and passkeys on any website or application not connected to your SSO for end-to-end encrypted access.
Unlock one-click provisioning and deprovisioning with SCIM to ensure users have the appropriate least privilege access based on their roles and responsibilities. By streamlining onboarding and offboarding with the IdP, administrative overhead is reduced and efficiency is improved.

Keeper SSO Connect enables secure authentication with end-to-end encryption across all of your websites, systems and applications.
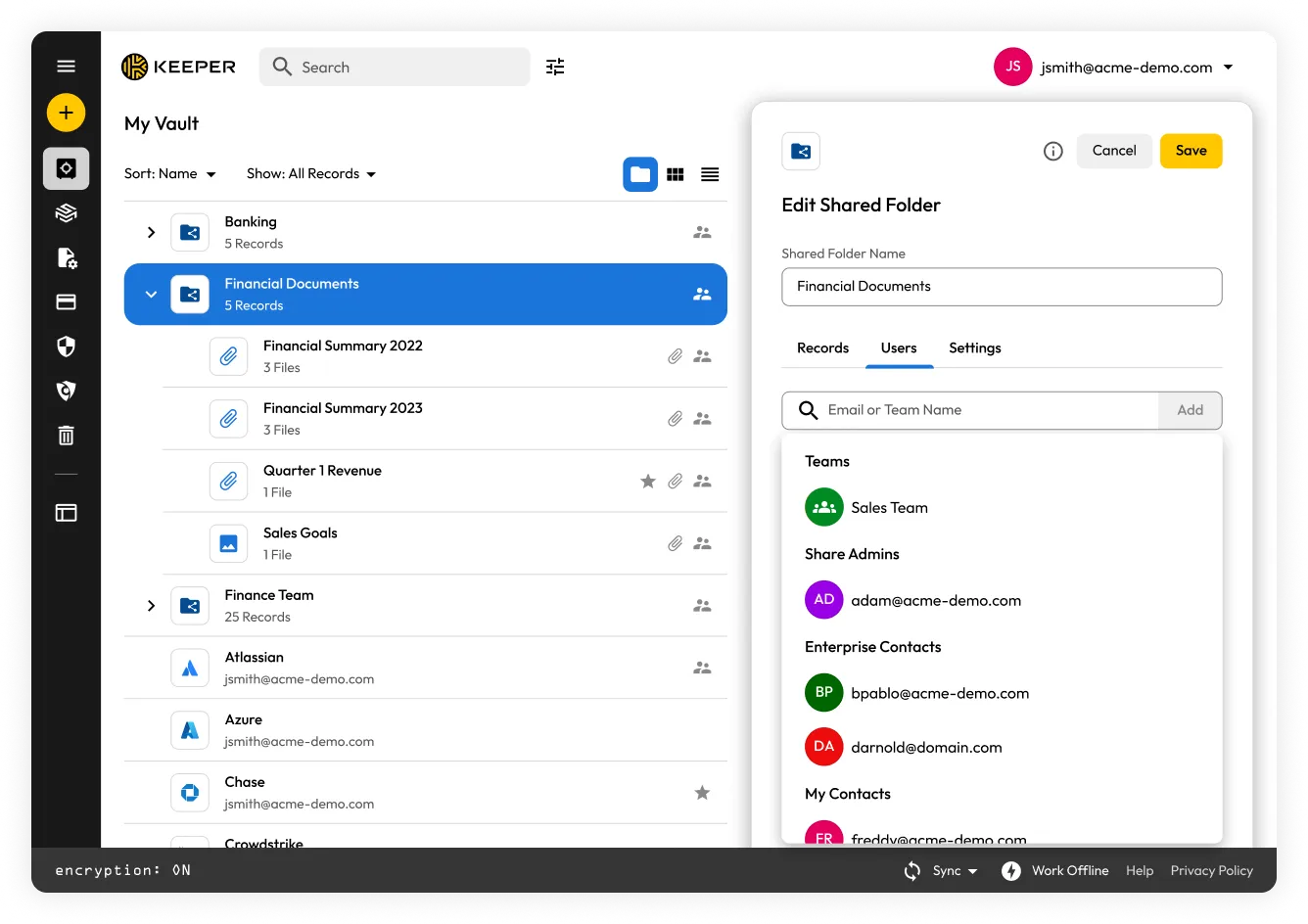
Keeper provides simple and secure sharing for users, and allows administrators to set granular restrictions on what can be shared and by whom at the role level.
If your organization already uses an SSO solution or is thinking of implementing one, pairing it with Keeper will fill the gaps in functionality and security.
*Via Keeper SSO Connect®
Keeper Security holds US utility patents for integrating SSO with a zero-knowledge platform. In this encryption model, the user has no master password and encryption is performed using Elliptic Curve (EC) cryptography.
Patent 11,363,009: System and method for providing secure cloud based single sign-on connections using a security service provider having zero-knowledge architecture
Patent 10,356,079: System and method for a single sign on connection in a zero-knowledge vault architecture
In this architecture, the Data Key of the user is decrypted with the Device Private Key and the Device-Encrypted Data Key is provided to the user upon successful authentication from their designated identity provider. Learn more about the Keeper SSO Connect encryption model.

Keeper acts as the bridge between SSO and biometric authentication solutions for a true passwordless experience. Employees can access every application, website and service without ever needing to enter a password.
With Keeper, any size organization can adopt a fully passwordless authentication process in a matter of hours.
You must accept cookies to use Live Chat.