You can protect your digital footprint by deleting any accounts you no longer use, adjusting your privacy settings, avoiding oversharing on social media and using a
Updated on April 4, 2025.
Common indicators of a phishing attempt include warnings from your email service provider, generic greetings, urgent or threatening language, too-good-to-be-true offers and more. These tactics are designed to manipulate you into revealing sensitive information. According to IBM, phishing is the catalyst for 41% of cyber attacks, leading to malware infections, account takeovers, fraud and identity theft.
Continue reading to learn how to spot phishing attempts and ways you can protect yourself from falling victim to phishing attacks.
1. Warning from your email service provider
Since phishing has become more common, many major email service providers, including Gmail, now feature built-in warnings about suspicious emails that could be phishing attempts. When your email service provider suspects that an email you’ve received may be a phishing attempt, you will see a warning message informing you that the message appears dangerous and suggesting that you report it.
2. Generic greetings
It’s a major red flag if you receive an email that uses generic greetings like “Dear Customer” or “Dear User” to address you. This is because most cybercriminals will send out mass phishing emails in hopes of deceiving as many people as possible. A generic greeting indicates that the email was sent to a large group as there was no effort to personalize it. In contrast, legitimate companies with which you have an account will typically address you by your full name as they have your personal information on file.
3. Urgent or threatening language
Phishing attempts often use urgent or threatening language to pressure victims into acting quickly. This is because the cybercriminal wants the targeted victim to act as quickly as possible so they don’t second-guess themselves when sending their personal information.
For example, a phishing text message, also known as smishing, may say something along the lines of, “Act now or your account will be deactivated. Click on the link below to update your login information.” Clicking the link could infect your device with malware or take you to a spoofed website to steal your credentials. Once you’ve entered your credentials on the spoofed site, cybercriminals can use it to compromise your legitimate account. Some phishing attempts may even threaten more serious consequences, like saying you’ll be arrested if you don’t pay them a certain amount of money by a specific deadline. While these threats are false, many people fall for them, risking financial loss and identity theft.
4. Too-good-to-be-true offers
If you ever receive an unsolicited message with an offer that seems too good to be true, it is likely part of a phishing attempt. These messages may offer incredible deals, prizes or exclusive opportunities, but they’re designed to trick you into revealing personal details or downloading malicious content. When cybercriminals execute their phishing attempts, they know exactly what to say to convince you of their authority, leading you to fall for their scams. Before clicking any links or buying anything from unsolicited messages, investigate further before taking any actions that could harm you and jeopardize your data or finances.
5. Misspellings and grammatical errors
Another common indicator of a phishing attempt is when a message contains misspellings and grammatical errors, especially if the email claims to be from a company you have an account with. Legitimate companies typically have strict review processes to ensure their emails are free from errors before sending them to customers. So, if you notice errors, it’s best not to click on anything in the email because it could be a phishing attempt. However, it is becoming harder to tell the difference between legitimate emails and phishing attempts because cybercriminals have started using Artificial Intelligence (AI) to quickly draft personalized phishing emails that contain no spelling or grammatical errors.
6. Unsolicited links and attachments
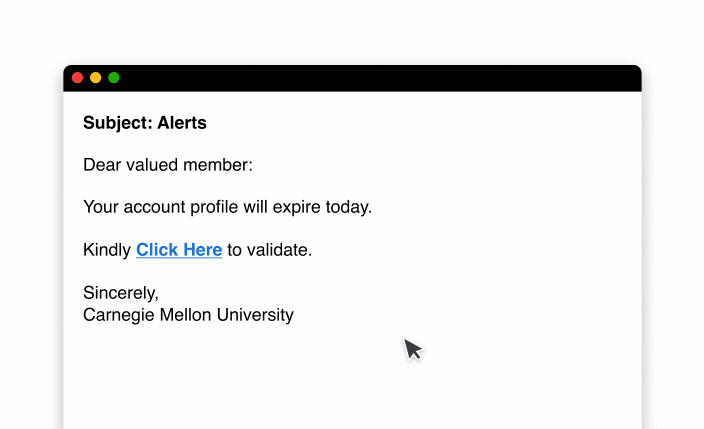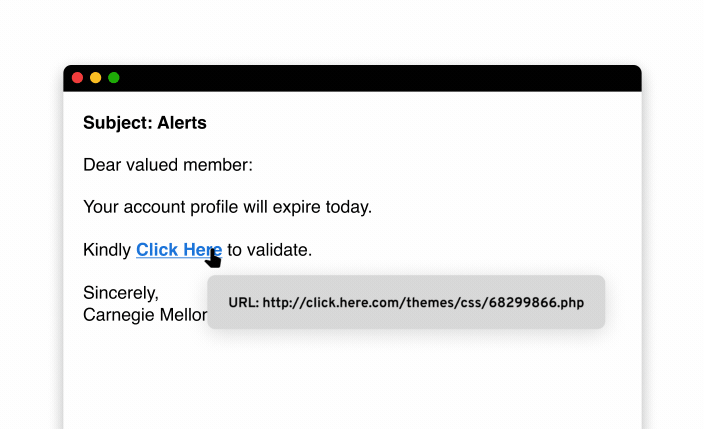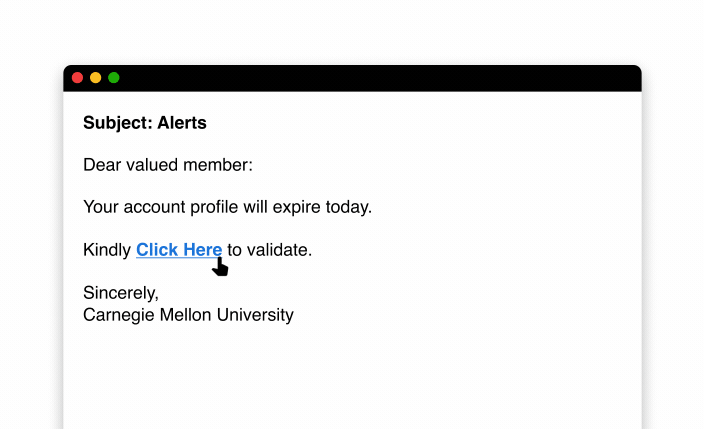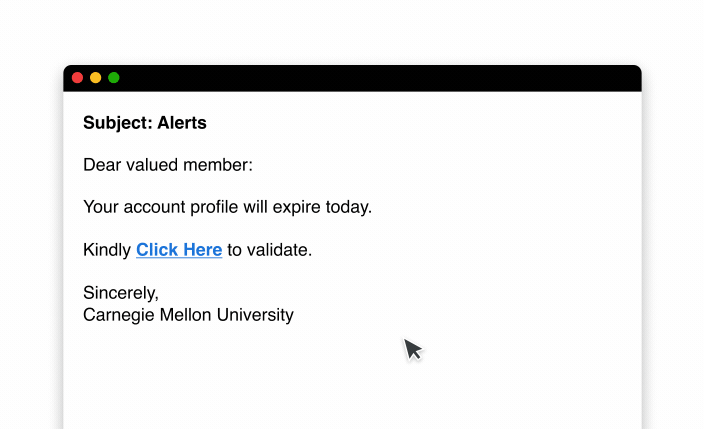
When you receive unsolicited links and attachments through email or text messages, this can be a sign that the message is a phishing attempt. Before clicking them, you should check if a link is safe by hovering your mouse over it and previewing the URL to determine if the link matches what it claims to be. Another easy way to check a link’s safety is by copying and pasting it into a URL checker. Check that an unsolicited attachment is safe by verifying who the sender is, avoiding attachments marked as spam and using antivirus software to scan attachments.
7. Requests for personal information
If you’re asked to provide personal information via email, text message or phone call, be cautious. Legitimate companies, such as banks or government agencies, typically don’t request sensitive details like passwords, credit card details or Social Security numbers, especially if you didn’t initiate the conversation. As phishing has evolved, some attackers even spoof phone numbers to make it seem like the message is coming from a familiar contact. If you’re asked to “verify” your accounts or “update” your personal details, these are requests designed to trick you into sharing private information that cybercriminals can use. If you receive such a request like this, verify its legitimacy by contacting the organization directly through official channels rather than responding to the message.
8. Discrepancies in email addresses and domain names
Another key indicator of a phishing attempt is when the sender’s email address or domain name doesn’t match the person or company they claim to be. For example, if you receive an email claiming to be from your bank but the domain name doesn’t match the official bank website, this is a clear sign of phishing. Legitimate companies typically use official domain names, so if the email address differs from the company’s official domain, someone may be impersonating your bank to steal your money or gain access to your financial information.
How to protect yourself from phishing attempts
Cybercriminals are becoming more clever in creating more advanced cyber attacks, especially with the help of AI. So, it’s even more important to know how to stay protected from these phishing attempts. Here are a few ways to protect yourself.
Use strong passwords on your accounts
Your online accounts are valuable to cybercriminals because they contain Personally Identifiable Information (PII), such as your credit card numbers, home address and date of birth. To protect your accounts, each one is secured with a strong password containing at least 16 characters and a combination of uppercase and lowercase letters, numbers and symbols. Creating strong, unique passwords on your own can be challenging, which is why we highly recommend using a password or passphrase generator.
Enable Multi-Factor Authentication (MFA) on your accounts
Your accounts should not only be protected with strong passwords, but they should also have MFA enabled whenever possible. MFA is a security measure that requires an additional form of authentication before you can access your account. When enabled, MFA requires you to provide at least one more form of authentication beyond your username and password. Even if you fall for a phishing attempt and give a threat actor your credentials, having MFA enabled would prevent them from compromising your account since they can’t verify their identity.
Checks links before clicking them
If you receive an unsolicited link, you must confirm that it is safe before clicking on it. Here are two ways to check if a link is safe:
- Hover your mouse over the link: Hovering your mouse over a link will reveal the actual website address that it will direct you to when you click it. If something about the website address looks suspicious, do not click on the link, as you may trigger a malware infection.
- Use Google’s Transparency Report: Google Transparency Report is a free tool you can use to check if a URL is safe. Simply copy and paste the link into the report, which will tell you whether it’s safe to click.
Use antivirus software to scan email attachments
Antivirus software is a type of program you install on your device that detects, prevents and removes known viruses and malware. Some antivirus software can also scan email attachments that you receive. When antivirus software detects that an attachment contains a virus, it removes the virus, preventing it from infecting your device.
Don’t respond to requests for personal information
You should never respond to sudden requests for personal information. Companies you have accounts with, such as your bank, will never randomly contact you to confirm credit card details. The only time a company will request personal information is if you were the one who initiated contact.
Reach out to the company or individual through another form
Whenever you receive an email, text message or phone call that makes you question its legitimacy, contact the individual or company directly through another method of communication. For example, if you receive a text from someone claiming to be your boss, send your boss an email to confirm if they actually sent you the text. If they say the message isn’t from them, then you know the text message was a phishing attempt.
Be vigilant in spotting phishing attempts
Falling for a phishing scam can lead to serious consequences, both financially and personally. By knowing how to spot phishing attempts, you can protect your personal information and prevent cybercriminals from gaining access to your data. The most important step when it comes to being protected against phishing attempts is to use strong passwords on your online accounts. You can create, update and store your passwords in a password manager like Keeper®.
Start your free 30-day trial of Keeper Password Manager to secure your online accounts and protect yourself from phishing attempts.