Password hygiene tips to follow include using unique passwords, enabling Multi-Factor Authentication (MFA) and keeping your passwords safe in a password manager. Password hygiene encapsulates the
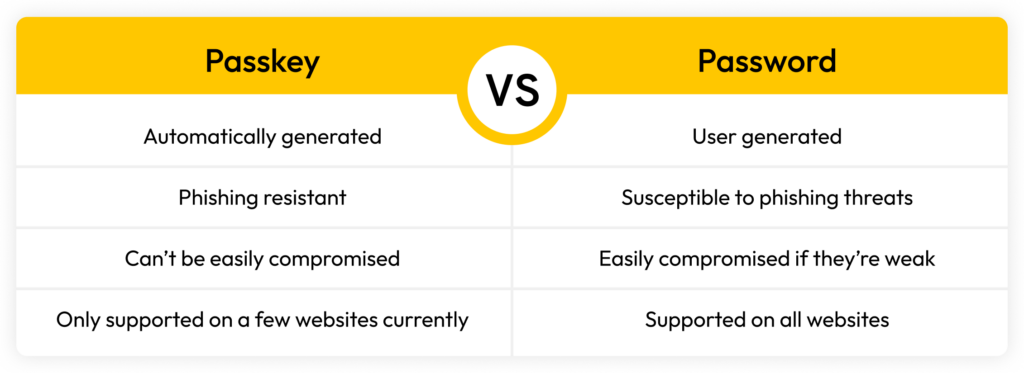
There are several ways in which passkeys are different from passwords in terms of how they are created, how they are filled into websites and how they are secured. Passwords are user-generated whereas passkeys are automatically generated using public key cryptography. Unlike passwords, passkeys are a new type of digital credential that is phishing-resistant and can’t be easily compromised. However, only a few websites currently support passkeys. And managing passkeys from different devices can be complicated.
Continue reading to learn more about what makes passkeys and passwords different and why passkeys are considered more secure.
What Is a Passkey?
A passkey is a new way to log in to online accounts without the use of a password. To understand what a passkey is, you have to understand how passkeys work. A passkey is made up of both a private cryptographic key and a public cryptographic key. The public key is stored with the company you created your account with and the private key is stored locally on the device you used to create the passkey.
Once you’ve generated a passkey for your account, you can log in to that account without having to enter a password. When you go to log in to an account that has passkeys enabled, the account server will send a challenge to the authenticator, which can be a phone, computer, tablet, browser or password manager. The authenticator uses the stored private key to solve the “challenge” and responds back to the server. This process is also known as “signing” the data to confirm you own the private key and to verify your identity so you can successfully log in to your account.
What Is a Password?
A password is a string of characters used to log in to online accounts in combination with a username. Together, they are known as your login credentials. Strong passwords vary in length and consist of a combination of upper and lowercase letters, numbers and symbols. The longer and more complex a password is, the better it’ll protect an account.
Although passwords are universal, they present cybersecurity risks. This is due to many users not understanding or taking password best practices seriously, so they often resort to using weak passwords or reusing the same password across multiple accounts. This is a dangerous practice because weak passwords are easier for cybercriminals to crack and password reuse places multiple accounts at risk of being compromised if only one of your passwords is part of a data breach.
A password can also be stolen by cybercriminals using phishing techniques and spoofed websites if a person is not using a secure password manager with adequate protection. Password managers provide a built-in warning about spoofed websites. If your saved login credentials aren’t auto-filling on the website you’re on, you’re on the wrong site and should get off of it immediately.
The Key Differences Between Passkeys and Passwords
Here are some of the key differences between passkeys and passwords.
Passkeys are created differently than passwords
When creating passwords, users have to ensure they follow password best practices so they aren’t easily cracked by cybercriminals. Users also have to ensure that each password is unique, meaning it isn’t being reused across multiple accounts. Creating strong, unique passwords on your own can be difficult to do, especially when you consider that you also have to remember all of the passwords you create. When it comes to passkeys, users don’t have to create anything. All they have to do is generate the passkey for their account and then they can log in using the device they generated the passkey from.
Passkeys are phishing-resistant, unlike passwords
Phishing is a cyber attack in which cybercriminals pretend to be someone they’re not – like a company, family member or friend – so their targeted victim is persuaded into providing them with sensitive information such as login credentials. In a phishing attack, cybercriminals will often try to get victims to click on a link that takes them to a spoofed website. This phony website is designed to look legitimate so the victim will log in with their account credentials.
With passwords, it’s easy to fall for phishing attacks because users can enter their username and password into a malicious site unaware that the site was designed by a cybercriminal to steal their credentials. With passkeys, cybercriminals can’t trick users into entering a passkey on a phishing website because there’s nothing for them to enter – making passkeys phishing-resistant.
Passwords are easier to compromise than passkeys
For online accounts to be secure, it starts with creating strong passwords. A strong password is at least 16 characters long and contains upper and lowercase letters, numbers and symbols. Strong passwords are also never reused and don’t contain personal information or dictionary words and phrases. While these are the rules for creating strong passwords, many users don’t follow them and continue to use weak passwords for their online accounts, making them more vulnerable to being compromised.
With passkeys, users don’t have to worry about creating strong passwords or having their accounts compromised if the company their account is with experiences a data breach. Since account servers only store the public key part of a passkey, if the server is breached cybercriminals will only have access to the public key which is useless without the accompanying private key.
Passkeys are only supported on a few websites
Passkeys are a new passwordless authentication technology, meaning that many websites don’t support them yet. This differentiates from passwords which are supported on all websites. Some websites that do support passkeys include Apple, Google, PayPal, Best Buy, Adobe, Microsoft and more. To see which other websites support passkeys, check out our passkeys directory.
Are Passkeys More Secure Than Passwords?
Yes, passkeys are more secure than passwords. This is not only because passkeys are phishing-resistant, but they are also error-proof. When users generate a passkey, they can’t make mistakes like they do with passwords.
In addition to being phishing-resistant and error-proof, passkeys also support Two-Factor Authentication (2FA) by design. 2FA is a second form of authentication that should be enabled on all online accounts when possible. Unless it’s required, many users don’t enable 2FA on their accounts because it creates an additional step to log in. Since passkeys are tied to the devices they’re generated on, the device acts as the authenticator, making passkeys even more secure than passwords since that device will always be required to log in.
However, because passkeys are tied to the devices they’re generated on, it makes managing them across different operating systems and device types complex. For example, if you use a Windows PC to generate a passkey and you want to log in to that account from your iPhone, you’ll need to have your Windows PC with you to be able to log in with the passkey.
Keep Your Accounts Secure With a Strong Password or Passkey
While passkeys are considered more secure than passwords, not all websites support them, so you will still have to continue using strong passwords for those online accounts. In addition to a strong password, you should also have 2FA or Multi-Factor Authentication (MFA) enabled. Like 2FA, MFA adds an extra layer of security to your account by requiring that you provide one or more additional authentication factors to your username and password before you can successfully log in.
Keeping your accounts secure with strong passwords or passkeys doesn’t have to be difficult. Password managers like Keeper Security are designed to help you secure your online accounts by storing both passwords and passkeys – making it a seamless experience to log in no matter which method is used. Start a free 30-day trial of Keeper Password Manager to see how Keeper can help you manage your passwords and passkeys.
 Password
Password