You can check your iPhone for viruses by checking for unfamiliar apps, seeing if your data usage has spiked, seeing an unusual number of pop-up ads
Managing IT infrastructure secrets is a hassle. Ironically, deploying and maintaining most secrets management solutions is at least half the battle. Typically, installing a secrets manager requires purchasing and installing additional on-prem hardware, then enduring a complex and time-consuming software installation process, and maintaining servers moving forward.
Keeper Secrets Manager (KSM) was designed to be simple to deploy and maintain so that you don’t spend more time managing your secrets manager than you do managing your secrets! It’s fully cloud-based, so it integrates into virtually any data environment, and there’s no need for any additional hardware or cloud-based infrastructure. It integrates with a wide variety of DevOps tools, including Github Actions, Kubernetes, Ansible, and more, right out of the box. While competing solutions take hours to install and configure, KSM can be up and running in minutes.
Unlike competing secrets managers, and like the rest of the Keeper security suite, KSM is zero-knowledge and encrypted to the endpoint, so credentials and other secrets are never exposed in plaintext format.
KSM also comes with a lightweight command line interface (CLI) that provides core Secrets Manager Vault interaction from Linux, Mac, or Windows command line terminals, shell scripts, or any software that can be launched from a shell. In addition to catering to developers and administrators who prefer working at the command line, the KSM CLI addresses a particularly vexing pain point in secrets management: removing hardcoded credentials.
Remove Hardcoded Credentials at the Command Line
Hardcoded credentials – user IDs and passwords written directly into source code – are notoriously insecure, yet maddeningly common. They’re seen a lot in the industrial control systems used to run manufacturing lines, utilities, and critical infrastructure, as well as all manner of IoT devices. Historically, removing hardcoded credentials has meant refactoring code, a tedious and error-prone process.
The KSM command line interface solves this problem with the exec subcommand, which enables developers and administrators to perform environmental variable substitution simply by executing a script. This means that, instead of rewriting code, KSM users can execute a script to perform a token replacement of hardcoded passwords – reducing a once-onerous project to a simple “find and replace” executed at the command line.
And that’s not all! The KSM command line interface lets admins and devs dig into their Keeper Secrets Manager implementation and automate other time-consuming tasks. For example:
Initialize a configuration file for use with external integrations
The init command initializes a one-time access token and creates a configuration profile for use with external integrations such as Github Actions, Terraform, and more. The output of the configuration can be generated as either base64 encoded JSON (default), or in Kubernetes format. Other KSM Developer SDKs, and applications, will understand configurations in this format.
Create a local profile to execute commands as a client device
The profile command enables administrators to switch between device profiles. You can also switch between KSM device profiles to support multiple environments on the same device.
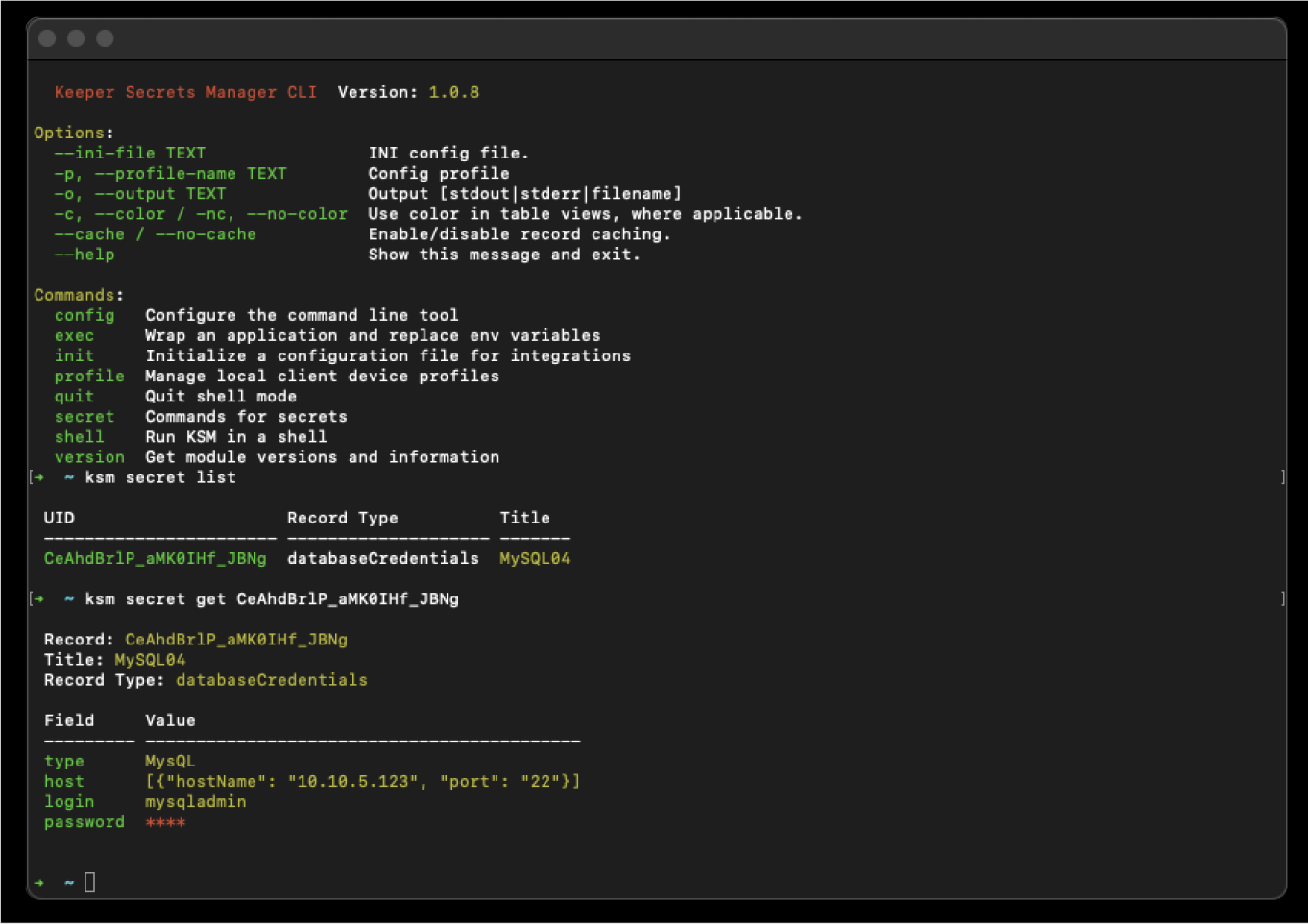
Query the Keeper vault and retrieve secrets
The secret command retrieves secrets from the Keeper Vault and parses the response. A wide variety of subcommands enable administrators to list all secrets associated with an application; retrieve a secret from the vault, or specific fields from a secret; add a new secret to the vault; generate a pass code from a TOTP field of the secret, and more.
The Keeper Secrets Manager CLI is available as a binary application for Windows/Mac/Linux or a pip3 install for any Python environment. For installation instructions and more information on how to use the KSM CLI, check out Keeper’s documentation.
Not a Keeper customer yet? Sign up for a 14-day free trial now! Want to find out more about how Keeper can help your organization prevent security breaches? Reach out to our team today.
 Cybersecurity
Cybersecurity 
