Yes, you can get scammed on Cash App in a variety of ways, including cash flipping, accidental payments and phishing messages. Cash App scams are harmful
Clickjacking, also known as a clickjacking attack or a clickjack, is a cyber attack in which hidden links trick users into completing an unintended action which results in the exposure of sensitive information and hacking.
Keep reading to understand more about clickjacking and how it works.
Understanding Clickjacking
In a clickjack, users will click on something online expecting to complete one action without realizing that the click actually results in a different, unintended action. This means that cybercriminals can trick you into downloading malicious software (known as malware), accidentally exposing sensitive Personally Identifiable Information (PII) or facing other serious consequences.
Clickjacking is used as a medium for launching a variety of cyber attacks. It can be hard to spot and can result in cybercriminals stealing your passwords or sensitive information like bank account, credit card and Social Security numbers. The ultimate goals of collecting this information include stealing money from you, taking over your accounts or stealing your identity.
How Clickjacking Works
Cybercriminals use clickjacking to trick you by manipulating what you see on screen. They overlay invisible fields on top of legitimate-looking fields in order to disguise the action you are taking. This can happen with a whole website or just a pop-up ad. Sometimes, the hacker even embeds the legitimate website inside their own site to make it look as real as possible. This is also known as a spoofed website.
Believing you are on a legitimate site, you will click things, enter your credentials or provide other sensitive information. You will believe you are completing legitimate actions but the invisible fields will cause you to accidentally download malware or send your information to cybercriminals instead.
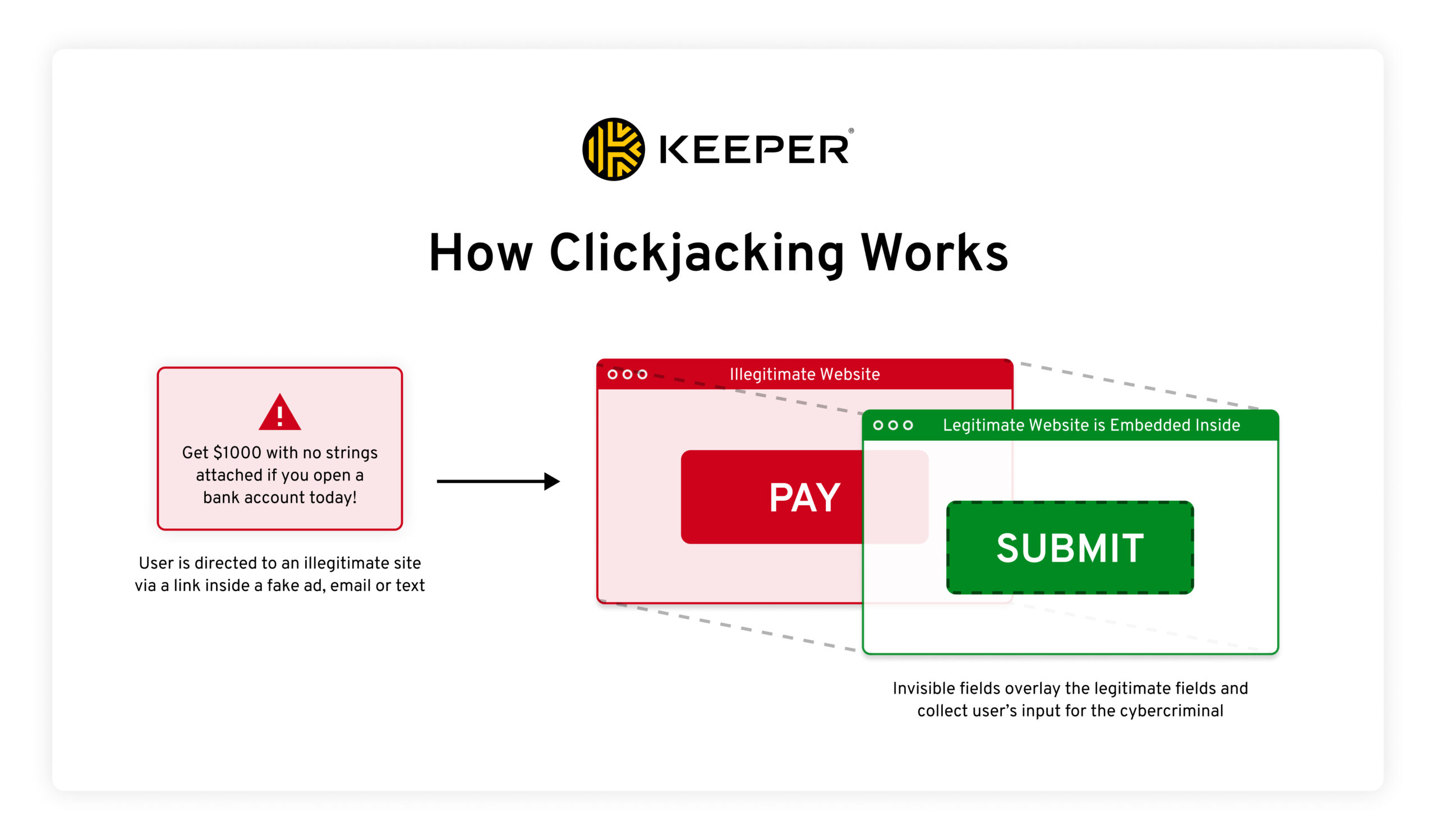
Cybercriminals direct you to their illegitimate interface by running fake ads that look like they lead to legitimate sites, sending fake emails and texts to you, making a post on social media or running infected pop-ups.
Examples of Clickjacking
Here are some examples of how clickjacking can work in the real world:
- The user gets an email from what they believe to be a legitimate social media site, like Facebook. They click the link, which takes them to a fake site with the real Facebook site embedded inside. The user tries to log in to their Facebook account by entering their credentials into the fields. However, the fake site has invisible fields overlaid on top of Facebook’s fields, allowing the cybercriminal to steal the user’s credentials.
- The user sees an ad that appears to be run by a well-known banking company, such as Chase. They decide to make an account, so they click the ad which takes them to a fake website with the Chase website embedded inside. They try to create an account by filling in sensitive information, like their Social Security number. However, invisible fields overlaying the real ones will copy the information and send it to the cybercriminal.
- A pop-up appears while a user is navigating a website. The user clicks the “X” to close the pop-up, but the “X” is actually a download link that installs malicious software on the user’s computer.
The Impact of Clickjacking
If a clickjack is successful, the cybercriminal can steal information such as PII or credentials, or install malware on your device. It could be any kind of malware, including spyware or a keylogger, which is malware that steals passwords from your browser.
Whether cybercriminals steal data themselves or install software that steals data for them, the end goal is to either sell your data to other cybercriminals or use the data to steal money or your identity.
It can be challenging and expensive to prove your identity has been stolen or that someone has taken over your bank account. It can take years to fully recover from these kinds of attacks.
Preventing Clickjacking Attacks
Preventing clickjacking attacks is the responsibility of the owner of the website where clickjacking may occur. There are methods to prevent cybercriminals from embedding a legitimate site on a fake site, such as using X-frame options, which is code that prevents websites from being embedded in a frame. This would be a major barrier to a successful clickjack.
Website owners should also carefully vet potential advertisers on their site. They should ensure any ads running on their site are legitimate and will not lead to clickjacking.
How Users Can Protect Themselves
While website owners are responsible for protecting users, sometimes they make mistakes. Luckily, basic internet safety tips can help protect you from clickjacking.
- Browse trusted websites. Well-known and highly-trafficked sites are more likely to properly protect their users from attacks like clickjacking.
- Navigate to websites using the official URL. If you are uncertain, Google the website. The legitimate URL, also known as the website address, should be the first search engine result.
- Avoid clicking pop-ups. Because any click could result in downloading malware, the safest way to leave a pop-up is by closing the browser window.
- Investigate the legitimacy of urgent emails and texts. Cybercriminals often use language with a sense of urgency to keep you from pausing to check whether a message is legitimate. Always contact the supposed sender directly with official contact information to see if the message really came from them.
- Download apps or files from trusted places. Random links online to download files or apps could potentially contain malware. Always download apps from the official Apple App Store or Google Play Store, even if it’s more expensive.
- Be suspicious of too-good-to-be-true ads. Cybercriminals often trick users into clicking their ads that redirect to fake sites by making seemingly amazing offers, like heavy discounts on expensive, popular items.
- Use a password manager. Many password managers have an autofill feature that only works on the URL that you save with the password. If you’re on a spoofed website of a company that you have an account with, your password manager won’t autofill your credentials and you’ll know the site isn’t legitimate.
Stay Vigilant To Avoid Being a Victim
Clickjacking is just one way that cybercriminals can attack you. Following cybersecurity best practices and keeping up to date with cybersecurity news can help you stay aware of the latest cyber threats, while also keeping your data and identity protected.
 Cybersecurity
Cybersecurity 
