Multi-Factor Authentication (MFA) helps add an extra layer of security to accounts, but it’s important to understand that not all MFA methods are created equal in
Personally Identifiable Information (PII) is any data that can identify a specific individual. Data like your Social Security number allows you to open credit cards, get a loan and more. It’s also data that is vital to keep secure in order to protect your identity and assets.
Read on to learn more about what types of information qualify as personally identifiable information and how to protect it from cybercriminals.
Sensitive vs. Non-Sensitive PII
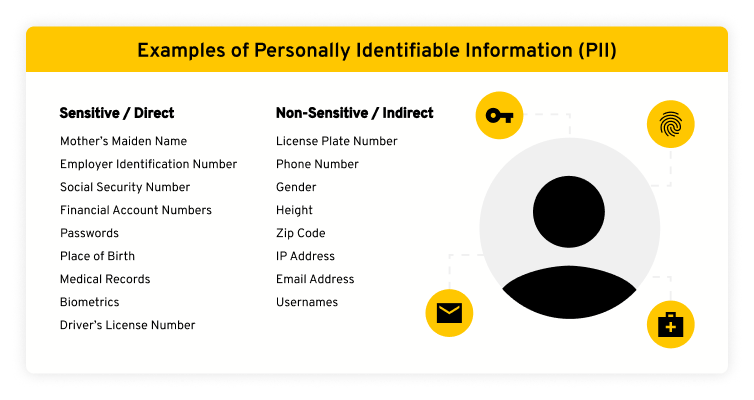
There are different types of PII known as sensitive or non-sensitive (also sometimes called direct and indirect, respectively). Sensitive or direct PII can reveal your identity with no additional information needed but is not publicly available. Sensitive PII includes your driver’s license number or Social Security number. Sensitive PII should be kept as confidential as possible from anyone who does not have a legitimate and confirmed need for it. Non-sensitive or indirect PII is publicly-available information still associated with your identity but cannot be used to identify you by itself. Phone numbers fall into this category.
Sensitive PII, when compromised and combined with your name, can make you vulnerable to cybercrimes such as identity theft. Non-sensitive PII can also make you vulnerable, especially when combined with sensitive PII.
For example, a list of names of people who are members of a book club would not be that compromising, but a list of names and addresses of people who are receiving medication in the mail would reveal details about their medical history that makes them vulnerable to medical scams and other cyber attacks, if it were to be leaked.
Examples of Personally Identifiable Information
Here are examples of both sensitive and non-sensitive personally identifiable information:
| Sensitive / Direct PII | Non-Sensitive / Indirect PII |
|---|---|
| Social Security number | Phone number |
| Driver’s license number | Race/ethnicity |
| Passport number | Height |
| Biometrics – fingerprints and iris scan | IP address |
| Bank account number | Zip code |
| Employer identification number | License plate number |
| Medical records | Gender |
| Credit or debit card number | Religion |
| Date of birth | Email address |
| Mother’s maiden name | Usernames |
| Criminal history | |
| Place of birth | |
| Full legal name | |
| Passwords | |
| Home address | |
The Importance of Securing PII
Since personally identifiable information is used to identify you for activities like opening bank accounts and applying for a driver’s license, compromised PII can lead to cybercriminals committing serious fraud against you. They can use PII to pretend to be you in order to make fake insurance claims, open accounts in your name and more.
Unfortunately, according to the FTC, Americans made 761,660 imposter scam fraud reports in 2022, resulting in nearly $3 billion in losses.
Your PII is worth money on the dark web – your credit card could be worth up to $22 and your medical records worth up to $1,000. There is an incentive for cybercriminals to target everyday people and sell their PII to other cybercriminals or use it themselves.
How Cybercriminals Steal PII
Cybercriminals steal PII through a variety of methods:
- Phishing and smishing: These are emails or texts from criminals pretending to be an official entity requesting access to your information.
- Data breaches: Personal information may be exposed on the dark web through breaches.
- Man-in-the-middle attacks: This type of attack intercepts your information in transit.
- Malware: This is malicious software that can attack your computer and steal confidential information.
- Steal credentials: This can happen through a variety of methods, including data breaches. If a cybercriminal steals your credentials it can give them access to accounts, like your email, that may contain PII.
Consequences of stolen PII
Cybercriminals who steal PII are able to commit identity fraud against the rightful owners, along with other types of crime. Theft of PII is incredibly common and results in consequences like financial loss and identity theft, as well as untold stress and time spent on recovery.
- As mentioned above, Americans experienced nearly $3 billion in losses from imposter fraud in 2022.
- In the past five years, the FBI has received complaints of internet scams resulting in $27.6 billion in losses.
- Businesses are greatly affected by Business Email Compromise (BEC), resulting in losses of $2.7 billion in 2022.
- 21% of Americans have experienced doxxing (according to SafeHome).
- In 2022, over half of the companies that experienced data breaches spent more than $50,000 on the aftermath. For some companies, costs surpassed $1 million dollars (according to Keeper’s 2022 Cybersecurity Report).
How to Protect PII and Reduce Risk
Both individuals and companies have a responsibility to protect PII. Individuals need to follow cyber hygiene best practices to protect their information. Businesses that hold PII in their databases also have an obligation to protect it. In fact, there can be legal liability for businesses that don’t.
How Organizations Can Protect PII
Keeper’s 2022 Cybersecurity Report found 48% of IT leaders have been aware of a cybersecurity attack but kept it to themselves. With proper security practices and password management, businesses can more effectively manage data and prevent breaches.
1. Implement a PAM solution
PAM – Privileged Access Management – is a term that describes the solution a business uses to manage and secure passwords, credentials, secrets and connections for highly-sensitive accounts, systems and data. A good PAM solution is quick to deploy and uses the best encryption to comprehensively protect against threats like supply chain attacks and insider attacks by limiting access to only what each user needs.
According to Verizon’s Data Breach Report, 74% of breaches involve the human element – whether that means simple error, misuse or malicious attacks by vendors, insiders or cybercriminals. PAM solutions help limit both malicious and accidental threats through precise management of access to sensitive information.
2. Conduct cybersecurity training
Data leaks caused by employees or vendors (called insider attacks and supply chain attacks, respectively) are not always malicious – sometimes they are simply the result of a user with poor cyber hygiene. Human error, including poor passwords and falling for phishing attacks, can result in compromised systems. Verizon’s report shows errors cause 13% of breaches.
In our 2022 US Cybersecurity Census Report, Keeper uncovered that 26% of leaders are concerned about a lack of employee training in cybersecurity. It’s time to train all employees. PAM is just one part of security management, and your cyber defenses are only as strong as the weakest link.
3. Anonymize data and don’t collect unnecessary data
There is a danger in many individual companies collecting a lot of data on users on a daily basis. Data breaches can result in compromised information, including personally identifiable information of users. If you do collect data, be sure to strip it of any identifying details and refrain from collecting data that’s not critical to run your business.
4. Erase “dark data”
Because it’s incredibly common for companies to collect lots of unnecessary data on users, they may also have data laying around from the past that they don’t really use. This is called “dark data” and it should be destroyed. Reports estimate over 50% of data possessed by companies qualify as dark data. Employees may not even remember where it came from. Any data a company is handling should have a clear purpose, be stored in secure locations, be fully accounted for and have usage records attached. Once you are done with the data, get rid of it or else it’s in danger of becoming dark data.
5. Have a plan in case of a breach
Data breaches are incredibly common for companies without the proper protections. With over 1,800 breaches last year, companies should be aware that they could be next. While it’s important to protect your data up front, there should also be a plan in case of a breach. The FTC has guidance on securing your operations.
How Individuals Can Protect PII
Individuals should also be protecting their own PII because cyber attacks can target anyone – not just businesses.
We’ve written in detail about how to keep your data safe online, but here are some of the key points:
1. Use strong, unique passwords for each account
Strong passwords have at least 16 characters and include a combination of upper and lowercase letters, numbers and symbols. They should not contain dictionary words or personal information like birthdays.
Passwords should be unique for every single account. If a compromised password is used on multiple accounts, all of those accounts will be at risk. You can easily generate strong passwords using a password generator. Since every password should be unique to that specific account, you can store all your passwords in a password manager. Password managers securely store all your passwords and allow you to access them anywhere, making it easy to have unique passwords for every account.
2. Use Multi-Factor Authentication (MFA)
MFA requires at least one extra form of identification in addition to your password. This prevents cybercriminals from accessing accounts because if they have compromised credentials, they would also need access to your MFA method(s), which can be harder to obtain.
MFA may be codes sent through text, a Time-Based One-Time Password (TOTP) in an authenticator app or a hardware security key.
3. Don’t share personal information online
When interacting with friends and family on social media, or completing a quest in with other users in a live video game, it can be easy to forget that you may be sharing information in a vulnerable space and you should restrict or withhold certain personal information. Things like your mother’s maiden name or details about your location may come up naturally, but you should avoid sharing them nonetheless.
4. Encrypt confidential files
Because we send images and more through email and text all the time, it can be easy to forget that those methods of communication are not encrypted. It’s vital to ensure that you’re using encryption to protect the confidential information you send over the internet, such as tax information or your insurance card.
Use a service like Keeper Password Manager with One-Time Share to share confidential files with users. Using the One-Time Share feature is a more secure way to encrypt and share files.
5. Don’t use public WiFi
You should avoid using public WiFi because cybercriminals have just as much access as you do. If you must use public WiFi, use a VPN.
PII is Worth Protecting
Whether you are an individual or a business, protecting PII is a serious responsibility that is vital to cybersecurity. Lack of adequate solutions to manage PII and poor cyber hygiene can make you vulnerable to dealing with the costly consequences of having sensitive stolen information.
Keeper Security has a business password manager and a next-gen PAM solution built to protect businesses of all sizes. We also offer a personal password manager for individuals and families to streamline the management of passwords and confidential files. Check out our free trials to learn how we can make life easier for individuals, families and organizations.

