An insider threat is a cyber threat that happens within an organization. Insider threats occur when current or former employees, partners, contractors or vendors cause sensitive data and systems to become compromised or steal data for their own malicious purpose. Insider threats can be intentional or unintentional, depending on the goal of the insider and
Identity theft is common in the US and can happen to anybody. The FTC received 1.1 million reports of identity theft in 2022, which made it the most prevalent type of fraud complaint they received that year. The internet has made identity theft easy, with the FTC reporting that most fraud happened via text, phone,
Yes, the dark web is dangerous because numerous criminal activities take place on the dark web. There are also cyber threats that are common on the dark web such as malware, a type of malicious software, that can be installed onto your device by a cybercriminal and used to steal your information. Read on to
Business Email Compromise (BEC) is a targeted cyber attack in which a cybercriminal poses as a trusted figure, such as the CEO of a company, and sends out an email to specific individuals requesting sensitive information or money. BEC attacks involve research and preparation in order for the cybercriminal to develop a convincing impersonation. Continue
Smart devices are amazing, and they make our lives easier. Smart light bulbs for your home allow you to change the color and schedule lights to turn on and off based on your activities. Internet-connected cameras allow us to monitor our homes with phone apps. Unfortunately, even a device as simple as a light bulb
Juice jacking is a security exploit in which devices are compromised when plugged into an infected USB charging station, port or use an infected charging cable. This type of security exploit takes advantage of the fact that many people need to charge their devices, especially when traveling, and use the provided USB cables to do
Since its launch in 2010, Microsoft Azure has been deployed to millions of organizations worldwide. Azure offers a vast array of services, including virtual machines, databases, AI and machine learning tools, analytics, networking, and storage options. Due to the global popularity of these cloud services, Keeper Security has prioritized seamless integration with Microsoft Azure. By
A bait-and-switch scam is a practice in which a vendor lures in a buyer with a tempting offer for a great product that the vendor does not intend to sell. This usually means advertising a too-good-to-be-true deal which, when the buyer is “baited,” is then “switched” out for a different offer. Understanding Bait-And-Switch Scams Bait-and-switch
If you use iCloud Keychain, you should switch to a dedicated password manager because it has superior security and more features to help you streamline password and data management. Password managers are cross-functional, allow you to securely share passwords, provide you with the ability to store more than just passwords and have secure add-ons available
Gmail accounts often contain vital, sensitive information including confidential documents and personal photos. They also often serve as a way to recover passwords for accounts like your banking login. That’s why email accounts are a common target for cybercriminals. Access to your Gmail account could be used to steal your money or your identity. You
Depending on how you create your passwords, such as the length or including letters, numbers and symbols, the time it would take a cybercriminal to crack it varies. Understanding what makes it easy for cybercriminals to crack your passwords is critical to keeping yourself safe from becoming a victim of this type of attack. Read
You can help prevent cyberstalking by protecting your data with a password manager, staying private on social media and following other cybersecurity best practices to keep yourself and your data safe. Keep reading to learn the best tips for preventing cyberstalking. What Is Cyberstalking? Cyberstalking is stalking conducted using technology. It involves repeated, frightening harassment
According to Pew Research, 41% of Americans have experienced some form of online harassment – and the severity of incidents has been getting worse over time. Understanding what different types of online harassment look like, and what behaviors harassers engage in, can help you recognize and address it. Keep reading to learn about the different
Privileged Access Management (PAM) enables organizations to address core controls needed to qualify for many cyber insurance policies. It’s important for organizations to be insured and mitigate the potential impact of a breach, and PAM is a critical part of any risk management strategy. In this blog, we’ll take a look at how organizations can
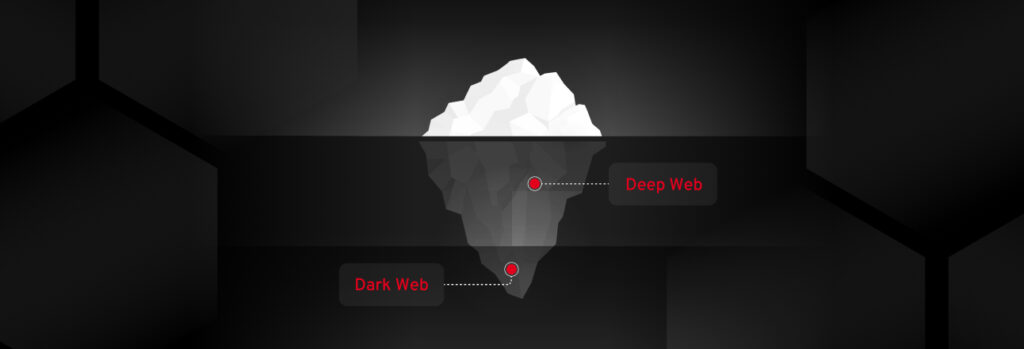
The main difference between the deep web and the dark web is that the deep web is bigger and used every day by most people without even realizing it. The dark web can only be accessed with the Tor browser and is riskier to access than the deep web. Continue reading to learn more about
Keeper Security has released its latest research, Password Management Report: Unifying Perception with Reality, which assesses the password habits of individuals across the United States and Europe. For the report, Keeper surveyed over 8,000 people. The survey focuses on the differences between what people say they do to ensure their cybersecurity, and what they actually
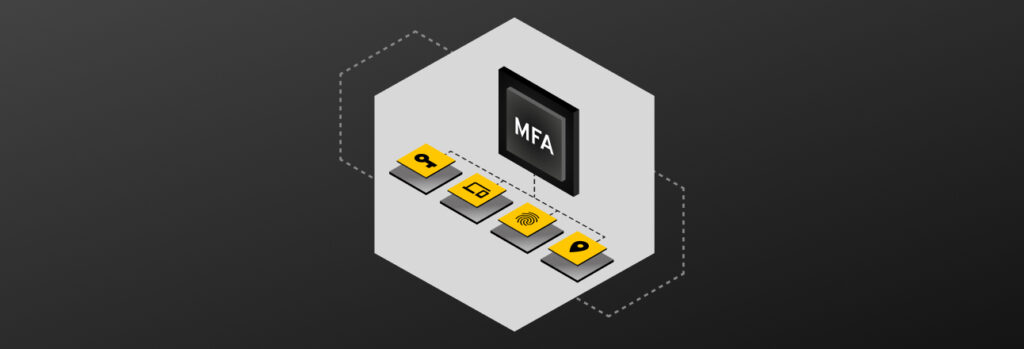
The four types of Multi-Factor Authentication (MFA) are knowledge, possession, inherence and location. These authentication types provide a foundation for a number of MFA methods, giving users multiple options for securing their data, ranging from SMS message tokens to hardware security keys. Which method is right for you or your business can depend upon what
Hackers fall into one of three general categories: white hat hackers, black hat hackers and gray hat hackers. But these aren’t the only types of hackers that exist. There are also red hat hackers, green hat hackers, blue hat hackers and more. Read on to learn more about the types of hackers and what makes
Yes, anyone who has access to your web browser or uses malicious software to hack it will be able to access the passwords saved in your browser. These known security flaws in browser password managers are often ignored because they are convenient to use. However, your passwords are not secure in a browser password manager.
Keeper Security partnered with Brigantia almost three years ago to focus on growing our business in the UK and Ireland MSP markets. It was an honour to re-join forces for a productive afternoon in London for an informative workshop with current partners. Brigantia’s Sales Director, Angus Shaw, and Keeper Security’s Global Channel Director, John Andrews,