The main difference between an attack vector and an attack surface is that an attack vector is the specific way a cybercriminal can take advantage of
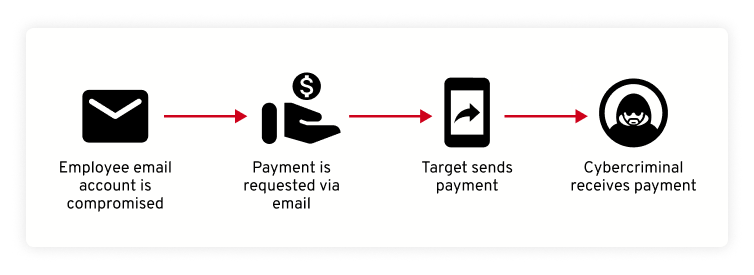
Business Email Compromise (BEC) is a targeted cyber attack in which a cybercriminal poses as a trusted figure, such as the CEO of a company, and sends out an email to specific individuals requesting sensitive information or money. BEC attacks involve research and preparation in order for the cybercriminal to develop a convincing impersonation.
Continue reading to learn more about business email compromise and what organizations should do to prevent this type of attack.
How Business Email Compromise Works
To carry out business email compromise attacks, cybercriminals start by researching their potential targets. The research includes understanding the targeted company, the industry and the organizational structure in order to get the details correct when they attack. BEC attacks are typically more targeted than other types of cyber attacks and because of this, people tend to fall for them at a higher rate.
Once cybercriminals know who they want to target and who they’re going to impersonate, they send an email to their target pretending to be a trusted figure such as a coworker, high-level manager, vendor or partner.
After a cybercriminal has established a convincing impersonation, they will send an urgent email to their target and create a convincing story, also known as a pretext. The goal of this story is to convince the target to send money or other sensitive information. Depending on what they’re asking for, cybercriminals may also create spoofed sites to make their request look legitimate.
In BEC attacks, cybercriminals often target mid-level employees who have access to highly sensitive systems and data such as finance or human resources employees. These employees have access to the Personally Identifiable Information (PII) of other employees and have the authority to issue payments. Cybercriminals may also choose to target newer employees who don’t have much security training or awareness of procedures within an organization.
It’s important to understand that cybercriminals carry out BEC attacks over a period of time. They will often communicate with their targets until they have a better understanding of who has access to what and when certain payments are made out to vendors. They may even attempt to compromise their target’s email account so they can pose as them to their email contacts and make launching their attack seamless.
Business Email Compromise vs Phishing: What’s the Difference?
Phishing is a type of cyber attack where a cybercriminal uses social engineering tactics to convince a targeted victim that they’re someone they’re not. They do this in an attempt to get them to reveal sensitive information like their account logins or credit card numbers.
Business email compromise is a type of phishing attack known as spear phishing. Spear phishing targets specific individuals or groups, typically through malicious emails. BEC attacks differ from general phishing attacks in that they are more targeted, meaning the individuals cybercriminals choose to target are chosen specifically and for a reason.
Business Email Compromise Examples
Here are a few examples of business email compromise:
CEO fraud
CEO fraud is when a cybercriminal impersonates the CEO of an organization to gain the trust of a targeted employee. Once they build trust with their potential target, cybercriminals ask them to send money or share sensitive information.
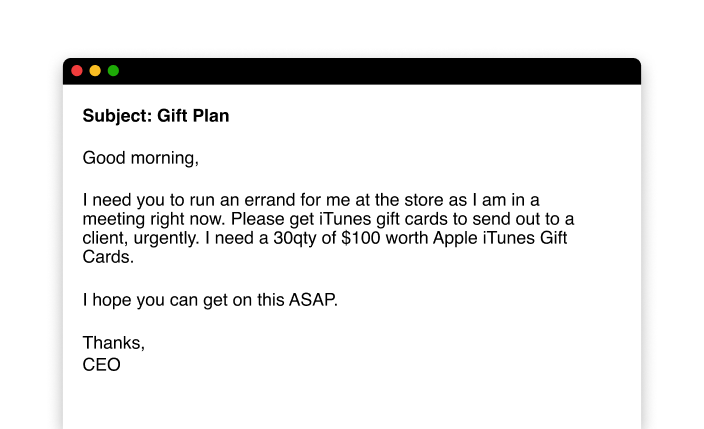
One common CEO fraud scam you’ve probably heard of is a gift card scam where the cybercriminal asks their target to purchase a certain amount of gift cards and provide them with the card identification number. Cybercriminals then use the number to redeem the money on the gift card.
Email Account Compromise (EAC)
EAC is a method that many cybercriminals use when carrying out BEC attacks. With EAC, cybercriminals gain access to an employee’s email account and go through their contact list to search for valuable connections like suppliers, partners or vendors. After identifying who they want to contact, cybercriminals send them an email to request bogus invoice payments.
The Risks of Business Email Compromise
The impacts of business email compromise attacks can be devastating if organizations are not taking preventative security measures. After experiencing BEC attacks, organizations experience significant monetary losses, reputational damage and legal consequences that are also costly.
BEC is one of the most pervasive cyber attacks that organizations face because of the payouts cybercriminals gain from them. According to Microsoft, between April 2022 and April 2023, they detected and investigated 35 million BEC attempts. On average, there were 156,000 BEC attempts daily.
How To Prevent Business Email Compromise
Here are a few of the ways organizations can prevent or lessen the impact of business email compromise.
Use strong, unique passwords
Each employee email account should have a unique, strong password that should never be reused for any other account. Relying on your employees to create their own passwords is a risk since they often use weak passwords that are easy to remember – and therefore easy to crack.
To prevent employees from using weak passwords, organizations should invest in a business password manager. A business password manager is a scalable tool that will aid employees with creating, managing and securely storing all of their passwords. It also enables them to securely share passwords with coworkers or contractors if necessary. Business password managers make it easy for IT teams to audit passwords and identify those that are weak or compromised.
Require employees to use MFA
Multi-Factor Authentication (MFA) is an extra layer of security that should be added to accounts whenever available. MFA verifies that the person attempting to log in to an account is who they say they are. In the event of a security breach or BEC attack, MFA prevents cybercriminals from being able to access an account because they won’t be able to verify who they are.
Business password managers enable IT teams to enforce the use of MFA on employee accounts to make them more secure.
Invest in a PAM solution
Privileged Access Management (PAM) refers to how organizations manage and secure access to highly sensitive systems, data and accounts. This includes payroll systems, administration accounts and more. Because BEC attacks often target employees who have access to highly sensitive systems, it’s important that organizations securely manage them at all times to prevent misuse and compromise.
Train and educate employees
One of the best ways you can prevent BEC attacks at your organization is by training and educating your employees on cybersecurity best practices. Teach employees that they should never overshare on their social media accounts because cybercriminals can use this information to launch targeted attacks. You should also teach your employees how to spot BEC attacks so they don’t easily fall for them.
These are only two of many cybersecurity best practices that you should train and educate your employees on. You should also teach your employees to keep up to date with the latest cybersecurity news so they are familiar with the latest cyber threats.
Stay Protected Against Business Email Compromise
Business email compromise continues to be a threat to organizations of all sizes. In order to mitigate this threat, organizations should always be on guard and implement preventative cybersecurity measures and tools like a password manager and PAM solution.
One PAM solution that organizations should consider is KeeperPAM™. KeeperPAM unifies three solutions into one unified platform: Enterprise Password Manager (EPM), Keeper Secrets Manager (KSM) and Keeper Connection Manager (KCM). With KeeperPAM, organizations can easily secure their passwords, secrets and remote connections.
To learn more about KeeperPAM, request a demo today.
 Cybersecurity
Cybersecurity