Many organizations have yet to invest in a PAM solution because they can be expensive and complex. While this is true for some legacy PAM solutions,
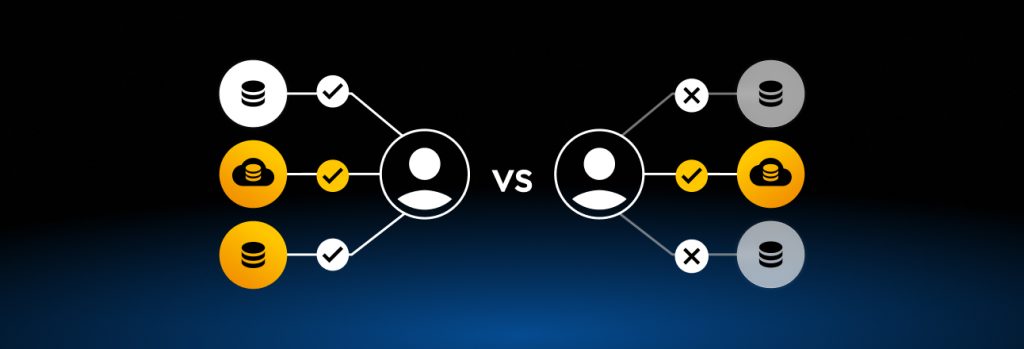
While trust plays an important role in access management, not all types of trust are created equal. When it comes to access management, there are two types of trust to pay close attention to, implicit trust and explicit trust.
Let’s go over what these types of trust are in access management and how they differentiate from one another.
What is implicit trust?
Implicit trust grants access to resources based on the assumption that every person within a system is to be trusted, unless they prove otherwise. With an implicit trust model in place, all authorization attempts that happen within an organization are approved as long as valid credentials are provided. It does not matter when, where or what device that trusted individual accesses those resources from, because under the implicit trust model, they are authorized to access those resources whenever they need to.
What is explicit trust?
Explicit trust grants access to resources based on continuous authorization. Rather than allowing anyone to access resources at any given time and on any device, individuals have to verify their identity and provide their need to access those resources. With an explicit trust model in place, an individual’s device, location and activities have to be approved before they’re granted access. If individuals are granted access, their activity is monitored to ensure there is no misuse of resources.
Key differences between implicit trust and explicit trust in access management
Now that you know how implicit trust and explicit trust work, here are some of their key differences.
| Implicit Trust | Explicit Trust |
|---|---|
| Every device is approved by default | Every device is explicitly approved |
| Location is not considered for authentication | Access from specific locations is explicitly approved |
| All actions are approved based on permissions | All actions are explicitly approved in real time, regardless of role |
| Best when used for low-risk resources | Best when used for high-risk resources |
| Common for in-person work environments | Best for hybrid and distributed workforces |
Device approval
When it comes to device approval, implicit trust approves every single device by default. On the other hand, explicit trust requires that each device be explicitly approved for use.
Location approval
When the implicit trust model is used to grant access, location is never verified. However, when the explicit trust model is used, access to resources from specific locations must always be explicitly approved.
Actions approval
Many organizations have permissions set for each employee based on their roles that allow them to perform certain actions. Implicit trust means all of these actions are approved as long as they’re included in an individual’s permissions within the organization. The explicit trust model requires that each specific action the user wants to perform be explicitly approved in real-time. It doesn’t matter what the individual’s role is set to within the organization.
Use case
Implicit trust and explicit trust both play an important role in access management within an organization; however, they each have their specific use cases. Implicit trust provides convenience for individuals within the organization since it allows them to access resources with minimal friction; however, it poses security risks. This means the implicit trust model should only be used for low-risk resources. Explicit trust, on the other hand, should be used for high-risk resources that contain sensitive data, and access to critical systems to ensure those resources are not mismanaged or misused.
How explicit trust helps organizations adopt zero trust security
Zero trust is a security framework that eliminates implicit trust and requires that all humans and devices be continuously and explicitly approved. Under a zero-trust security framework, the ability for a cybercriminal or other unauthorized individuals to move laterally throughout an organization’s network becomes a lot more difficult because of the need for continuous approval. This not only reduces an organization’s attack surface but also mitigates the risk of suffering data leaks and breaches.
Any organization that is planning to adopt zero-trust security needs to start with the implementation of explicit trust in its access management strategy.
KeeperPAM™ helps organizations implement explicit trust
Explicit trust can be difficult for organizations to implement without the right tools, but KeeperPAM makes it secure and easy. KeeperPAM is a next-generation Privileged Access Management (PAM) solution that combines Keeper Enterprise Password Manager (EPM), Keeper Secrets Manager (KSM) and Keeper Connection Manager (KCM) into one unified platform. KeeperPAM makes implementing explicit trust easy while also enabling zero-trust and zero-knowledge security and compliance.
To learn more about how KeeperPAM helps organizations implement explicit trust into their access management strategy, request a demo today.
 PAM
PAM