Remote access to company resources through web browsers has grown exponentially in recent years. With that growth comes an increased risk of exposing sensitive information and
ServiceNow users can eliminate secrets sprawl in their organization by dynamically retrieving credentials from their Keeper Vault via a seamless integration with Keeper Secrets Manager.
ServiceNow is a cloud-based platform that provides workflow automation, service management and business-process automation solutions to enterprises. ServiceNow is one of the most popular and widely deployed IT Service Management (ITSM) solutions available today.
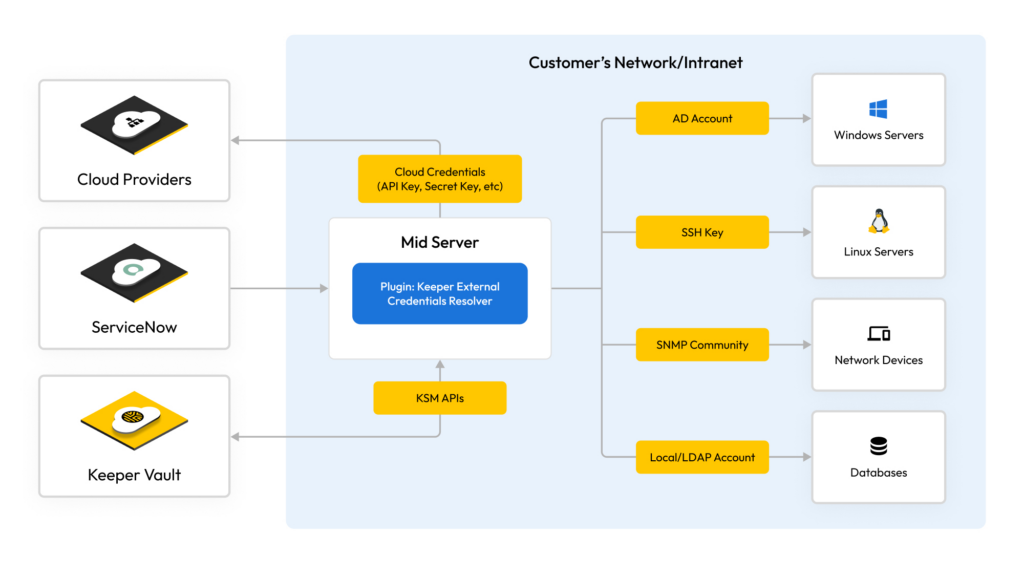
The ServiceNow Management, Instrumentation and Discovery (MID) Server is an essential component of ServiceNow’s IT Operations Management (ITOM) suite, especially for the discovery and orchestration modules. MID acts as a bridge between the ServiceNow instance in the cloud and an organization’s local network or infrastructure.
When the MID Server needs to access various infrastructure components (like systems, devices, applications and servers) for tasks such as discovery or orchestration, it relies on the credentials that are typically stored in the ServiceNow instance. However, storing credentials directly in the ServiceNow instance can potentially cause integration and audit challenges for organizations. More importantly, though, storing credentials in ServiceNow increases the attack surface of an organization by decentralizing where credentials are stored.
What Is Secrets Sprawl?
Organizations may experience the phenomenon of “secrets sprawl” which happens when credentials, such as SSH keys, SNMP community strings, OAuth tokens, username/password combinations and more, are scattered across multiple locations, systems, repositories or environments without proper management, tracking or protection.
Secrets sprawl creates serious security risks including
- Increased Attack Surface: The more places secrets reside, the more opportunities there are for attackers to discover and exploit them.
- Lack of Accountability: Without centralized management, it’s challenging to know who has access to which secrets and when they were last used or changed.
- Difficulty in Response: If a breach occurs, it’s harder to identify compromised secrets and rotate them promptly.
- Non-Compliance: Regulations like GDPR, CCPA and HIPAA require strict control over sensitive data. Secrets sprawl can lead to non-compliance and associated penalties.
Keeper Secrets Manager (KSM) eliminates these challenges. With KSM, DevOps and DevSecOps teams can manage and protect their secrets with a fully managed, cloud-based platform that is affordable and easy to deploy.
ServiceNow customers can use KSM for on-demand discovery, incident response and as a custom credential provider.
Example: Onboarding a New Data Center
A company has just set up a new data center with a mix of servers, network devices and other infrastructure components. The IT team wants to ensure that all these new assets are documented and managed within ServiceNow’s Configuration Management Database (CMDB).
Initiation: An IT administrator realizes that the new data center’s assets need to be added to ServiceNow. The admin logs in to ServiceNow and initiates the on-demand discovery process for the new data center.
Trigger: ServiceNow recognizes the request and knows it needs to communicate with the infrastructure in the new data center to discover the assets. It sends a request to the MID Server to start the discovery process for the specified IP range or domain associated with the new data center.
Credential Retrieval: Instead of having pre-stored credentials in ServiceNow or the MID Server (which can be a security risk), the MID Server communicates with Keeper Secrets Manager to fetch the necessary credentials. The ServiceNow instance maintains a unique identifier for every credential, its type (e.g., SSH, SNMP or Windows) and any associated credential affinities. The MID Server obtains the credential identifier, type and IP address from the instance, and uses Keeper vault to resolve these elements into a usable credential.
Discovery Process: Armed with the necessary credentials, the MID Server accesses the infrastructure in the new data center. It identifies servers, network devices, software applications, configurations and other relevant details. Throughout this process, the MID Server uses credentials from KSM, ensuring they aren’t exposed or stored insecurely.
Updating CMDB: Once the discovery process is complete, the MID Server sends the information back to ServiceNow. ServiceNow then updates its CMDB with the newly discovered assets, ensuring they’re documented, categorized and ready for management within the platform.
Completion: The IT administrator can now view the new data center’s assets within ServiceNow, manage them, link them to other IT services and ensure they’re maintained, updated or decommissioned as needed.
By integrating KSM, the credentials used in the discovery process are kept secure, reducing the risk of exposure. The on-demand nature of the discovery ensures that assets are added to the CMDB as soon as they’re onboarded, keeping records up-to-date. With accurate and timely updates to the CMDB, the organization can ensure compliance with internal policies and external regulations.
In this example, integrating Keeper Secrets Manager with ServiceNow streamlines the discovery process, ensuring that it’s both efficient and secure. The elimination of static, stored credentials in favor of dynamically fetched ones from KSM reduces the risk of “Secrets Sprawl” and enhances the overall security posture of the organization. This is just one example of the many use cases for integrating KSM with ServiceNow.
To learn more about the benefits of integrating Keeper with ServiceNow, schedule a demo today.
 Product Announcements
Product Announcements 
