The public sector continues to be a target for cybercriminals as ransomware attacks and data breaches hit government organizations at all levels, incurring large financial costs
The U.S. federal government tends to move very slowly – except when it comes to zero-trust cybersecurity. The drive to get all agencies to zero trust is cruising along at warp speed, as evidenced by White House Executive Order 14028, CISA’s Zero Trust Maturity Model, OMB OMB M-22-09 and the DoD zero trust strategy and roadmap, all of which were released within the span of less than two years.
Keeper Security’s zero knowledge SaaS platform helps federal government agencies build zero-trust security architectures as directed by EO 14028, OMB M-22-09, CISA’s Zero Trust Maturity Model and DoD’s zero trust strategy and roadmap.
Is Keeper a Cloud Computing Product?
While Keeper is a SaaS product hosted on AWS, our platform does not fit into the traditional model of what many think of as “cloud computing,” where data lives solely in the cloud.
Keeper stands out from most other SaaS products in two areas:
- While Keeper is a SaaS product, it incorporates on-premises components, meaning features can operate independent of the cloud. We’ll discuss that in more detail below.
- Keeper’s zero-knowledge security architecture ensures that customer data is never stored in plaintext on our servers. It can only be decrypted on the device level – in other words, “on-prem.”
Can Keeper Access My Data?
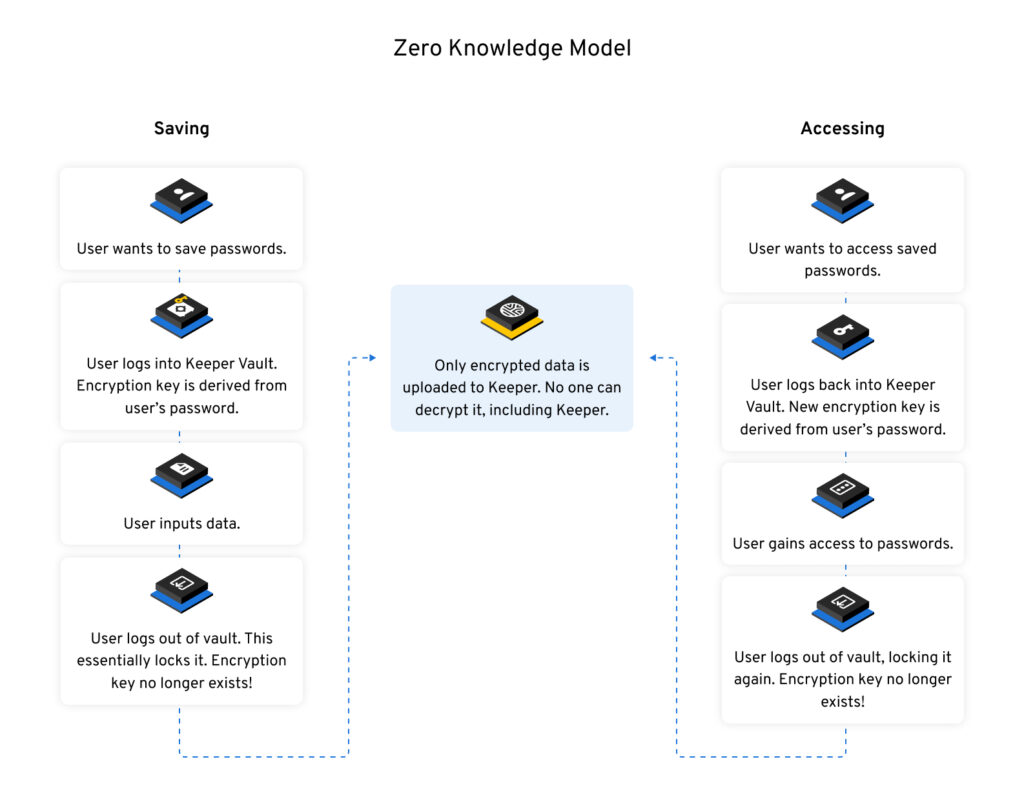
No, Keeper cannot access your data. Because of Keeper’s zero-knowledge encryption model, none of our employees can access our customers’ vault data, no matter what. This is what makes Keeper fundamentally different from most SaaS products.
When using a “true” cloud computing SaaS product, such as Gmail, every keystroke you type is immediately transferred to the cloud, and that data lives completely in the cloud. For security purposes, the data is encrypted, but the SaaS vendor can access the decryption keys and, therefore, access your data.
In stark contrast, Keeper is a zero-knowledge security provider. This means:
- Customer data is encrypted and decrypted at the device level, not on the server.
- For users who log in with a master password, the keys to decrypt and encrypt data are derived from their master password.
- For users who log in with Single Sign-On (SSO) or passwordless technology, Elliptic Curve cryptography is used to encrypt and decrypt data at the device level.
- Keeper’s servers never receive or store data in plain text. Data is encrypted on the user’s device before it is transmitted and stored in Keeper’s digital vault. When data is synchronized to another device, the data remains encrypted until it is decrypted on the other device.
- The Keeper application never stores any plain text (human readable) data, only encrypted ciphertext.
- Sharing of data uses public key cryptography for secure key distribution.
Keeper’s encryption model supports the Bring Your Own Key (BYOK) management process, because the keys are either derived from the user’s master password, or they are distributed through the functionality of the SSO Connect client-side encryption platform.
Which Keeper Components Are On-Prem?
While on-prem components are not required to operate the Keeper platform, numerous Keeper components can be optionally hosted and installed on-prem, including:
- Active Directory Bridge: Keeper Bridge allows businesses on-prem Active Directory (AD) environments to integrate with Keeper for the automatic provisioning and deprovisioning of Users, Roles and Teams to Keeper. The Keeper Bridge is designed to use the Lightweight Directory Access Protocol (LDAP and LDAPS) to communicate with LDAP-based Directory Services for the purpose of onboarding and offboarding users to the Keeper platform.
- Keeper Commander toolkit: This provides AD password rotation plugins that can be configured or customized to fit the customer’s business needs.
- Keeper SSO Connect On-Prem: Just like Keeper SSO Connect Cloud, our on-prem SSO integration works with all major SAML 2.0-compatible identity providers, including Microsoft Azure, Okta, Google Workspace, Centrify, OneLogin, Ping Identity, JumpCloud and more, with zero-knowledge encryption and seamless authentication for end-users.
- Keeper Automator: Device authentication is a crucial part of a zero-trust security architecture. Keeper Automator is a lightweight automated system that performs instant device approvals upon a successful login from the SSO identity provider.
- Keeper Connection Manager: An agentless remote desktop gateway that can be installed in any on-prem or cloud environment to provide IT admins and DevOps personnel with secure, easy access to RDP, SSH, database and Kubernetes endpoints through a web browser.
- Keeper’s desktop and mobile apps: Keeper’s apps are natively installed on the end user’s device, with offline storage and cloud sync.
- Keeper’s browser extensions and the Keeper Commander CLI: These are natively installed on the end user’s device, with cloud sync.
- Offline mode: Provides users with full, offline access to their Keeper vault data, even if the backend or an internet connection are unavailable. The encrypted ciphertext is stored on the device, and can only be decrypted by the user with a master password or biometric authentication.
The Main Benefits of Keeper For Government Agencies
Keeper allows government agencies to enjoy all the benefits of cloud computing, but with the option of on-prem components, coupled with the highest levels of security, privacy and total control over their data.
Comply with federal government zero trust cybersecurity directives
Right out of the box, Keeper enables federal agencies to meet many of the requirements of EO 14028, OMB M-22-09, CISA’s Zero Trust Maturity Model and DoD’s zero trust strategy and roadmap:
FedRAMP authorized: Keeper Security Government Cloud (KSGC) is FedRAMP authorized on the moderate level and listed in the FedRAMP Marketplace.
Simple integration with centralized identity systems: The federal government’s zero-trust strategy places significant emphasis on strong enterprise identity and access controls. Keeper integrates with all major SAML 2.0-compatible identity providers, as well as on-prem Active Directory environments and Microsoft Azure AD environments for SAML 2.0 authentication and automated provisioning with SCIM.
Phishing-resistant Multi-Factor Authentication (MFA): Per the federal government’s directive for all agencies to use phishing-resistant MFA wherever available, Keeper provides support for the most popular and secure Two-Factor Authentication (2FA) methods: SMS, TOTP-based Authenticator apps like Google or Microsoft Authenticator, RSA SecurID, DUO Security, Keeper DNA (wearable device authentication with Apple Watch and Android Wear devices) and FIDO2 WebAuthn devices like YubiKey. 2FA/MFA can be enforced through Keeper’s Role-Based Enforcement Policies and can also be configured by the end user directly in their vault.
Least-privilege access and Role-Based Access Controls (RBAC): A key tenet of zero-trust security is role-based access based on the least-privilege access principle. Keeper provides administrators with delegated administrative functions, including role-based access controls (RBAC) to control user and team access, and the ability to enforce security policies and define enforcements based on a user’s job responsibility. The number of roles an organization creates is a matter of preference and/or business need.
Secure file sharing: In support of the OMB’s requirement for enterprise-wide information sharing, Keeper Secure File Share enables efficient, secure, vault-to-vault sharing of stored files with other Keeper users. Just like passwords stored in Keeper, users can set sharing permissions for digital files (read-only, edit, share or edit and share).
Check passwords and secrets against public data breaches: In support of the OMB’s requirement for agencies to “check passwords against known-breached data,” Keeper BreachWatch® scans dark web forums and notifies IT administrators if any employee passwords have been compromised in a public data breach.
Encrypt data in transit: EO 14028 directs that all data be encrypted while in transit. Keeper encrypts data in transit with TLS 1.2, while data at rest is encrypted using AES 256 GCM. In addition to using TLS, Keeper’s API uses Elliptic Curve (ECIES) signing to defend against replay attacks, man-in-the-middle attacks and to perform integrity checks. Data in the payload is encrypted locally on the user’s device and decrypted on the user’s device. Keeper uses Protocol Buffers within encrypted payloads to ensure data models are enforced on the client device.
More benefits of using Keeper
Lower costs: Keeper is a fully managed platform that integrates into virtually any tech stack, with no additional software or hardware required. Keeper handles all maintenance and upgrades.
Scalability and flexibility: Keeper can scale to fit any size organization, and customers can easily adjust their licenses as business needs change.
Use on virtually any device, running any OS: Keeper operates native apps across all mobile devices, browsers and desktop computers, including Microsoft Windows, Mac OS, Linux, iOS, Android and Surface.
Compatible with all major web browsers: Browser extensions are available on Chrome, Safari, Firefox, Internet Explorer 11, Edge, Chromium Edge, Opera and Brave.
Compliance reporting: Keeper’s Advanced Reporting and Alerts Module (ARAM) provides Keeper administrators and compliance teams with tools for monitoring overall usage and adherence to policies. ARAM captures over 150 different user and administrator events for both detailed reporting and SIEM integration as well advanced notifications via email, SMS or Slack.
No vendor lock-in: Keeper is infrastructure-agnostic. Our platform integrates into virtually any tech stack and works with any cloud provider or combination of providers, including multi-cloud and hybrid cloud environments, allowing Keeper customers to easily switch cloud providers.
Further, you own the data in your Keeper Vault, and you can easily take it with you should you ever decide to part ways with Keeper. Our data export feature allows end users to export their passwords to .csv, .pdf. or .json files. Keeper also provides advanced export capabilities through the use of the Keeper Commander SDK.
Keeper is the modern, effective way to achieve Compliance with Executive Order 14028 and CISA, DoD and OMB Zero Trust strategies. Ready to try out Keeper for your public sector organization? Reach out to us today.
 Public Sector
Public Sector