You can check your iPhone for viruses by checking for unfamiliar apps, seeing if your data usage has spiked, seeing an unusual number of pop-up ads
The U.S. federal government is committed to implementing zero-trust cybersecurity across all government agencies. In 2021, the White House issued Executive Order (EO) 14028, directing federal agencies to adopt zero-trust network architectures. A few months later, CISA followed up with a draft Zero Trust Maturity Model. In early 2022, the Office of Management and Budget (OMB) released memorandum M-22-09, which requires agencies to meet specific zero-trust standards and objectives by the end of Fiscal Year 2024. Later that year, the Department of Defense (DoD) published its own zero trust strategy and roadmap.
That’s a lot of movement over a short period of time, especially considering that the wheels of government usually turn very slowly. However, despite all of this pressure from the top, decision-makers at government agencies remain skittish about adopting the cloud-based technology that would allow them to achieve zero-trust goals: Software-as-a-Service (SaaS) solutions. Many misconceptions abound regarding the underlying technology; in particular, a persistent myth that “SaaS” means user data is stored in the cloud, where cybercriminals can access it.
This post will explain what SaaS really means and put these fears to rest.
What is SaaS?
SaaS is a method of software delivery where a third-party vendor hosts and maintains the servers, databases and code that make up an application. Customers access SaaS applications over the internet, generally through a web browser. Some SaaS apps also offer desktop apps, mobile apps and browser extensions.
Pretty much everyone uses SaaS products every day, without even realizing it. Examples of SaaS products include Gmail, Salesforce and even social media apps like Instagram.
Is SaaS the Same as Cloud Computing?
No. SaaS is not synonymous with cloud computing.
“Cloud computing” is an umbrella term that refers to any solution that’s hosted remotely and delivered to customers over the internet. All “SaaS” means is that the application is hosted in and delivered through the cloud. However, that does not mean that an application has no on-prem components, nor does it mean that your data will be shot into cyberspace, where anyone can have at it.
SaaS platforms often have both on-prem and cloud-based components. Perhaps more importantly, if the SaaS provider uses a zero-knowledge security architecture, your data is never stored “in the clear” on the cloud. It’s stored locally, on your device; even the SaaS provider can’t access it, let alone anyone else.
What is Zero Trust?
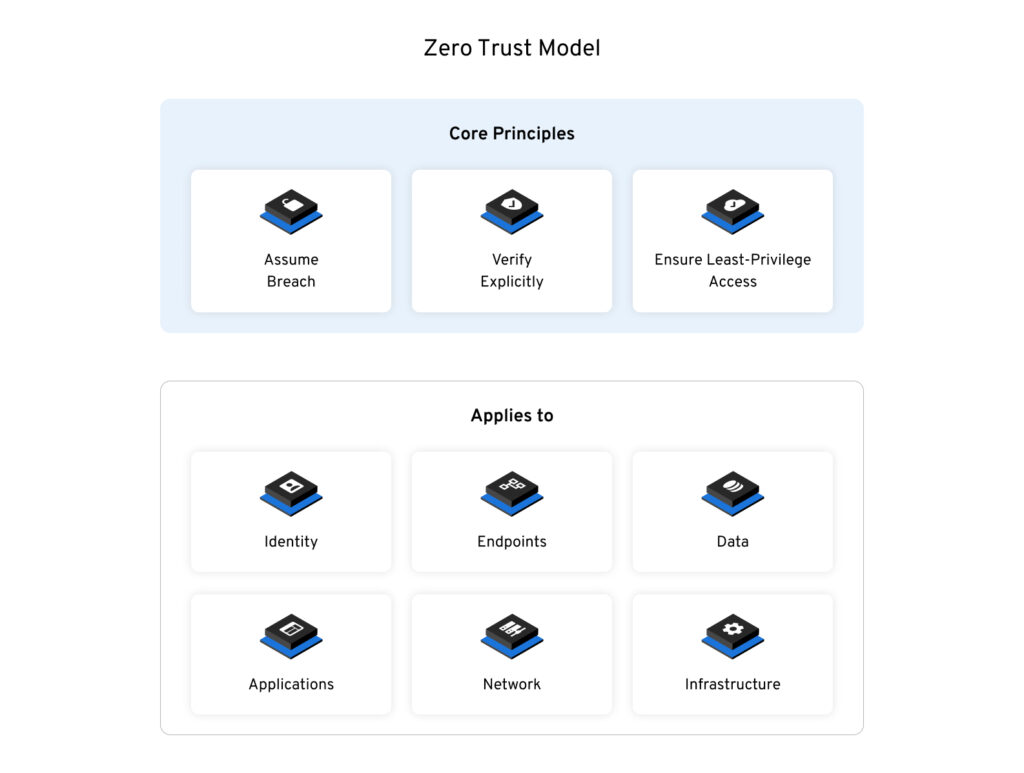
Zero trust is a modern security model that prevents unauthorized access to data and services by making users prove that they are who they say they are prior to allowing them to access a network. Further, even once a user is authenticated into a network, they are given just enough access to systems and data as they need to do their jobs – and no more.
Zero trust gives IT administrators full visibility into all users, systems, and devices. It allows people, applications, and services to communicate securely, even across network environments. It doesn’t matter if users are connecting from their homes, or hotels, or coffee shops, or airports, or even if they’re using their own devices. Administrators can see exactly who’s connecting to the network, from where, and what they’re accessing – and users can’t get in at all until they’re thoroughly authenticated.
What’s Zero Knowledge?
Zero knowledge is a security architecture that does not fit into the traditional model of what many think of as “cloud computing,” where data lives solely in the cloud. Instead, it ensures the highest levels of data security and privacy by adhering to the following principles:
- Data is encrypted and decrypted at the device level (not on the server)
- The application never stores plain text (human-readable) data in the cloud
- The server never receives data in plain text
- No one except for you can view your data
- Sharing of data uses public key cryptography for secure key distribution
- When data is synchronized to another device, the data remains encrypted until it is decrypted on the other device
That’s great. What does all that mean, in plain English?
If your eyes glazed over reading the previous section, you’re not alone! Zero knowledge is a tricky concept, even for people who are well-versed in technology. Here’s a metaphor for explaining zero knowledge in plain English:
Imagine a magic box with a magic key. Once you put something inside the box and lock it with this key, the contents turn to dust. Only the magic key can put the contents back together, so even if someone were to break inside the box, all they would find is dust.
Here’s how this works with a zero-knowledge SaaS provider:
- You put an item in the magic box, and then you lock it with the magic key.
- You give the magic box to the SaaS provider, but you keep the magic key.
- When you want the item back, the SaaS provider gives you the locked box.
- You use your magic key, which you kept the entire time, to unlock the box and retrieve your item.
In this case, the “magic box” contains your encrypted data (which is as useful as dust), and the magic key is your decryption key – which only you have access to, because that’s stored on your device, not in the cloud.
Further, this magic key isn’t laying around someplace where it can be stolen. It’s derived from your password, so it doesn’t even exist until you enter your password and a second authentication factor, like a hardware key or CAC card. After you log out or time out, the key goes away until you authenticate again.
What Are the Main Benefits of Zero-Knowledge SaaS?
Zero-knowledge SaaS solutions enable organizations to enjoy all the benefits of cloud computing, coupled with the highest levels of security, privacy and total control over their data. These benefits include:
Lower costs: Robust SaaS platforms integrate into virtually any tech stack, with no additional software or hardware required. The SaaS vendor handles all maintenance and upgrades.
Simple integration with centralized identity systems: The federal government’s zero-trust strategy, as outlined in EO 14028 and OMB M-22-0-9, places significant emphasis on strong enterprise identity and access controls, including Multi-Factor Authentication (MFA). Zero-knowledge SaaS platforms more easily integrate with modern identity management systems than traditional on-prem solutions.
Enhanced security: EO 14028 directs that all data be encrypted while in transit, a requirement that zero-knowledge solutions have out of the box.
Rapid installation and deployment: With no hardware to configure, and with no need to download software onto every user’s computer individually, SaaS solutions are much easier to install and configure than on-prem solutions.
Scalability and flexibility: SaaS products can scale to fit any size organization, and because they’re sold on a subscription basis, customers can easily adjust their licenses as business needs change.
There is no reason for government decision-makers to fear SaaS products, so long as they choose a solution that is zero-knowledge and, of course, FedRAMP-authorized. Zero-knowledge, FedRAMP-authorized SaaS solutions provide better security at a lower cost than traditional on-prem software, while allowing federal agencies to improve the services they provide to everyday American citizens and deliver those services more efficiently.
 Cybersecurity
Cybersecurity 
