The main difference between an attack vector and an attack surface is that an attack vector is the specific way a cybercriminal can take advantage of
You can protect yourself from phishing attacks by knowing how to recognize them and implementing cybersecurity solutions to keep yourself safe from these types of attacks.
Phishing attacks have been on the rise recently because, to put it bluntly, they work. The Anti-Phishing Working Group (APWG) recorded 1.09 million phishing attacks in the second quarter of 2022.
As phishing attacks continue to increase, it’s important to learn what phishing attacks entail. Phishing is the most common way attackers deliver ransomware, which is the fastest-growing form of malware. Keep reading to learn how to protect yourself from phishing attacks.
What Is a Phishing Attack?
A phishing attack is a sophisticated social engineering attack aimed to persuade the victim into disclosing sensitive information such as credit cards or social security numbers. Most phishing attacks take the form of emails disguised to look like they come from trusted sources. The subject line usually carries an urgent message intended to drive immediate action, such as notice that an account has been compromised or that a service is about to be suspended.
The attacker’s goal is to alarm the recipient and prompt immediate action – usually downloading an attachment or clicking on a link – without thinking about what they’re doing. That one click can trigger a malware infection, which can lead to your private information getting stolen.
How To Recognize a Phishing Attack
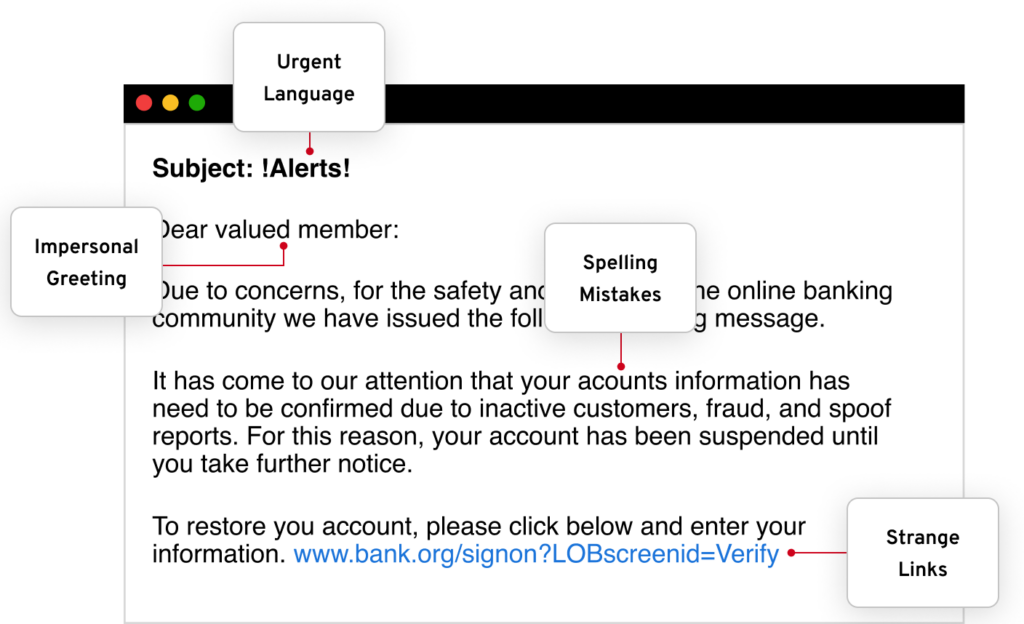
An attacker will often use phishing emails and text messages to get the victim to reveal sensitive information. Here are a few ways to recognize whether those emails and texts are legitimate.
Poor spelling or grammar. Many businesses have editors or peers to check for spelling or grammar errors before sending out business-related emails. If the email you’ve received has multiple misspelled words and poor grammar, then the email is most likely a scam and you should not respond or click on any links or attachments.
Ask you to reveal sensitive information. Reputable organizations will never ask you to send passwords, credit card numbers or other personally identifiable information by email or text messages. Make sure to never send sensitive information through email or text, especially if you’re not sure to who you’re sending it.
The email address does not match the sender’s username. There are two parts to the “From” part of an email: the username (or alias) and the email address. The alias can be anything the sender wants it to be, but you can’t disguise an email address. Phishers always change the alias to look legitimate, like “PayPal Customer Service.” But if the email address in that example isn’t PayPal.com, the message is fake. Always check before clicking.
There are unsolicited attachments attached to the email. A legitimate email from a business will never send you an email containing an attachment or demand that you download files. Instead, they will direct you to their website, where you can download files such as reports safely. Even if the email is from a supposedly legitimate organization, always avoid opening unsolicited attachments.
How To Protect Yourself Against Phishing Threats
There are several precautionary steps you can take to protect yourself against phishing threats.
Don’t click on a link or attachment unless you’re sure
If you receive an email that you are not expecting and it tells you to click on the link or it contains an attachment, do not click on any of it. This is a common phishing tactic that is used by attackers to lure unsuspecting victims and get them to click on a link or attachment that contains malware.
Never respond to requests for information
This goes without saying, one of the best ways you can go about protecting yourself from phishing threats is by never giving out any of your personal information to anyone you do not know. This can be extremely dangerous to your personal security as it can lead to more of your accounts getting breached. If you receive a request for private information from a company such as your bank, call them directly to verify the request is legitimate and never respond to the email or text.
Use multi-factor authentication
By enabling multi-factor authentication on all of your accounts, your cybersecurity will be automatically enhanced. This is due to the fact that multi-factor authentication requires that users identify themselves by more than just their username and password. This ultimately makes stealing your information harder for the attacker. Although, you must be cautious of phishing threats that pretend to ask for your authentication code if you accidentally send the attacker the authentication code you’re giving them access to your account.
Back up your data
Continuously backing up your data is extremely important especially if you ever become a victim of a cyber attack such as a phishing attack. By having your data backed up in a secure digital vault, you’re ensuring that you’ll always have access to your data, despite it getting into the wrong hands.
Invest in a password management solution
One of the little-known benefits of a password manager is that it helps protect you from phishing scams. This is because it won’t work on a login page where the URL doesn’t match the URL entered when the record was created. So even if the phisher tricks you into clicking on a link, the password manager gives you an extra layer of protection. Think of it as phishing insurance.
Stay Informed
Keeping up-to-date on the latest phishing threats is extremely important. You’ll be able to recognize phishing threats easily and know when there is a phishing threat happening at your workplace or at a business you’re a customer of. Staying updated on the latest cybersecurity news is extremely important in keeping your online security safe.
What To Do if You’ve Been a Victim of a Phishing Attack
Recognizing a phishing attack is one thing, but becoming a victim is another. If you believe you have become a victim of a phishing attack because you entered sensitive information on a webpage or clicked on an attachment, here are five steps you should take.
Step 1: Disconnect your device from the internet
Disconnecting your device from the internet lessens the chance of malware spreading to your other devices that are on the same network. Additionally, it will stop someone from remotely accessing your device or using it to send out sensitive information. Taking this step right away is vital to secure all your devices.
Step 2: Change the password on all your accounts
If you clicked on a link that took you to a fake website where you attempted to log in – the attacker may now know your credentials. This a type of phishing attack that tricks people into thinking they a visiting a well-known website such as your bank account or social media website. If you use the same credentials or variations of the same credentials, attackers could then access your other accounts using the information you inputted into the fake site.
Making sure your credentials always have strong, unique passwords is important because it can prevent the attacker from causing further harm to your accounts. By using the same username and password for all your accounts, you’re making it easier for the attacker to gain access to all of them.
Step 3: Keep an eye on your credit report for suspicious activity
Since it’s possible that the attacker may have gained access to your credit card accounts or sensitive information that can be used to gain access to your credit, it’s extremely important to keep an eye on it. You may even consider freezing your credit. A credit freeze will help prevent the attacker from being able to open new accounts under your name.
Step 4: Contact the company or person that was being impersonated by the attacker
Letting the company know that an attacker is impersonating them is important in keeping you, the company and their customers and employees safe from also falling victim. They may also be able to provide you with instructions to safeguard the information on your account.
Step 5: Report the phishing attempt
You can report a phishing text message to the Federal Trade Commission by forwarding it to SPAM (7726). You can also report the phishing attempt online at ReportFraud.ftc.gov.
 Cybersecurity
Cybersecurity 
