Remote access to company resources through web browsers has grown exponentially in recent years. With that growth comes an increased risk of exposing sensitive information and
Keeper is pleased to announce that our business solutions now support team-to-role mapping, which will allow organizations to use their existing identity provider to assign users directly into teams that can be assigned custom roles. This will save time, improve policy consistency, reduce errors, and make it easier for administrators to manage role-based access control policies (RBAC) across larger user populations.
With team-to-role mapping, a user who is a member of a team who is assigned to a role will assume the enforcements of the given role. That user can be a member of the role more than once, once via user-role membership and again via user-team-role memberships if any exist.
For security purposes, only non-admin roles are allowed to have teams as members.
How it works
Typically, identity providers that use SCIM (systems for cross-domain identity management) such as Okta and Azure support assigning users to teams, but custom role assignment is done only on a user basis. SCIM-provisioned teams and users are applied to the default role, without the ability for a team provisioned from SCIM to be mapped into an alternative, pre-defined role.
To use team-to-role mapping, administrators simply assign a role to an entire “Team,” as opposed to individual users and use role enforcements to establish different requirements and restrictions for each team.
For example, consider a situation where an administrator creates a role named “Require MFA”. The administrator wants to force all users assigned to Team A to use a MFA method when logging onto Keeper. Previously, the administrator would have added each individual user account to the “Require MFA” role. Now, the administrator can simply add Team A to the role that has the enforcement seen below.
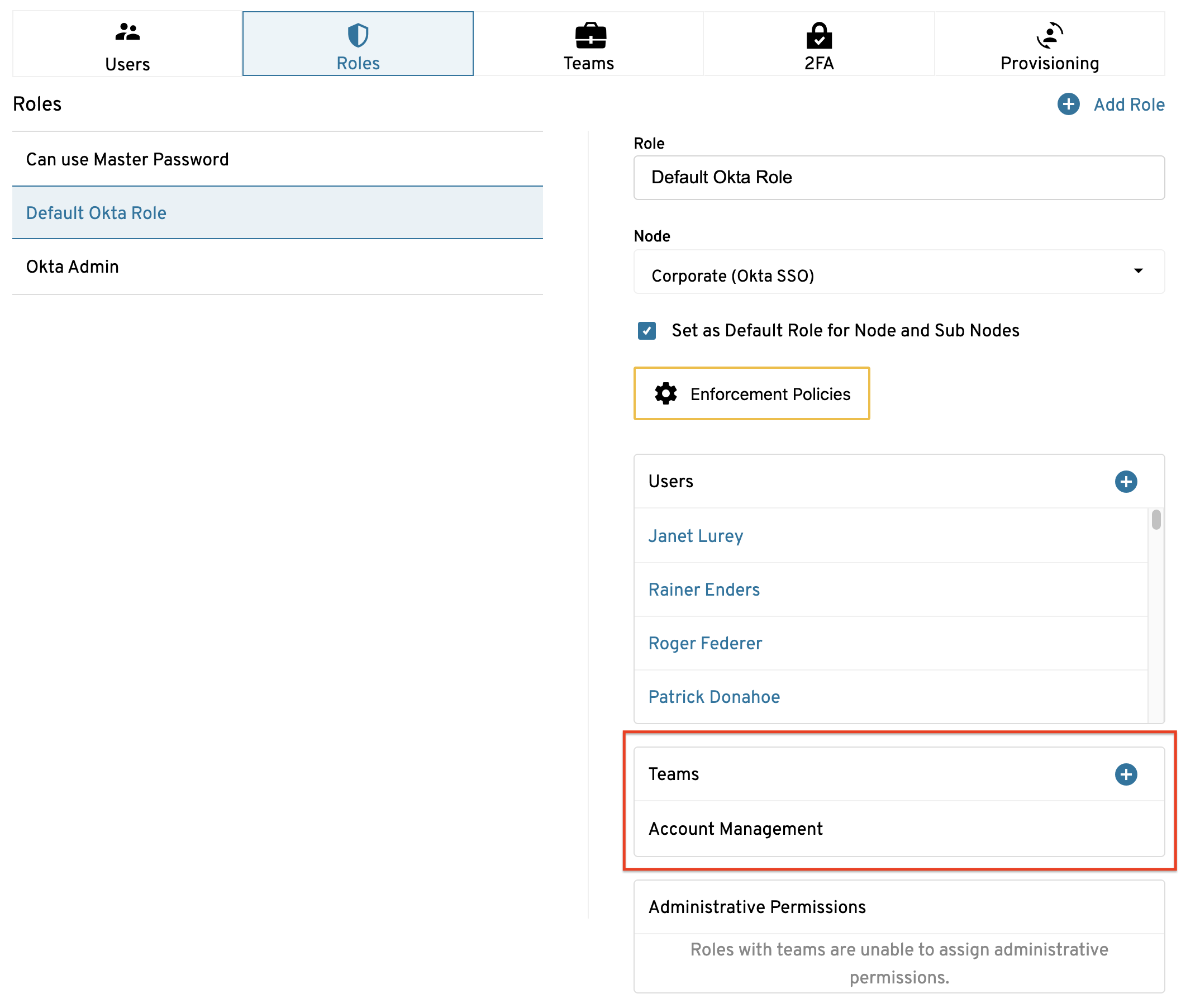
Administrators can also use team-to-role mapping to assign roles to multiple “teams” under a main department, such as a QA team in the Engineering Department. By breaking the company up into teams, the admin needs only to assign each team to a role, instead of having to individually assign roles to each user within the company. Additionally:
- Vault Transfer includes subfolders
- Vault Transfer moves the vault into a folder (instead of directly into the destination root)
- Admin Console better UI support for small screen laptops and tablet devices
Get started right now
Team-to-role mapping is available now on all Keeper Business and Enterprise plans for customers who are running Version 14.4 or later.
Not a Keeper customer yet? Download Keeper Password Manager and Digital Vault now! Interested in how Keeper can help protect your business against the #1 cybersecurity risk? Reach out to our team today.
 Product Announcements
Product Announcements