Zero-Trust Cybersecurity for Educational Institutions
Keeper protects your organization’s passwords, credentials and secrets with zero-trust and zero-knowledge security.
The Education Security Challenge
is the cost per record in higher education data breaches (40% higher than industry average)1
of breaches start with weak or stolen passwords3
of higher education cybersecurity incidents and breaches were caused by social engineering attacks2
Zero-Trust cybersecurity is vital to protecting students and staff - on and off campus. Out of 17 major industries, education ranks last in cybersecurity preparedness.4 Educational institutions are entrusted to secure vulnerable data, including personal information about staff and students at every level, from K-12 to higher education.
With the rise of remote learning, the number of cyber attacks on educational institutions also rose. This exposure comes from students and faculty connecting to databases and applications via unsecured networks. Providing cybersecurity solutions to every student, teacher, staff, and parent is essential in order to protect institutions from cyber attacks.
Protecting Educational Institutions from Cyber Threats
While the education industry is vulnerable to every type of cyber threat, there are two that occur most often.
Phishing
Phishing is a sophisticated social engineering attack meant to entice victims into voluntarily revealing sensitive information.
The challenge with phishing is that it can be difficult to spot as methods become more sophisticated.
Ransomware
Ransomware attacks lock users out of their systems until a ransom is paid. This ransom payment is often requested in cryptocurrency to maintain anonymity.
Keeper’s Enterprise Password Management (EPM) solution gives IT administrators complete visibility into how employees, students and parents use school-related login credentials – enabling them to monitor password hygiene across the entire network. Policies such as strong passwords, 2FA and additional security protocols can be easily enforced through the admin console.
Educational institutions choose Keeper for flexible, scalable integrations with any tech stack and environment and to fill security gaps in existing solutions such as SSO.
Keeper helps prevent phishing, ransomware and many other cyber threats. Schedule a demo to learn how.
Protect your institution with these easy to adopt, unparalleled capabilities:
Email Auto-Provisioning
Provision vaults to thousands of users with a domain match on email addresses to allow large-scale deployment with minimum administration. Other advanced provisioning methods are also available.
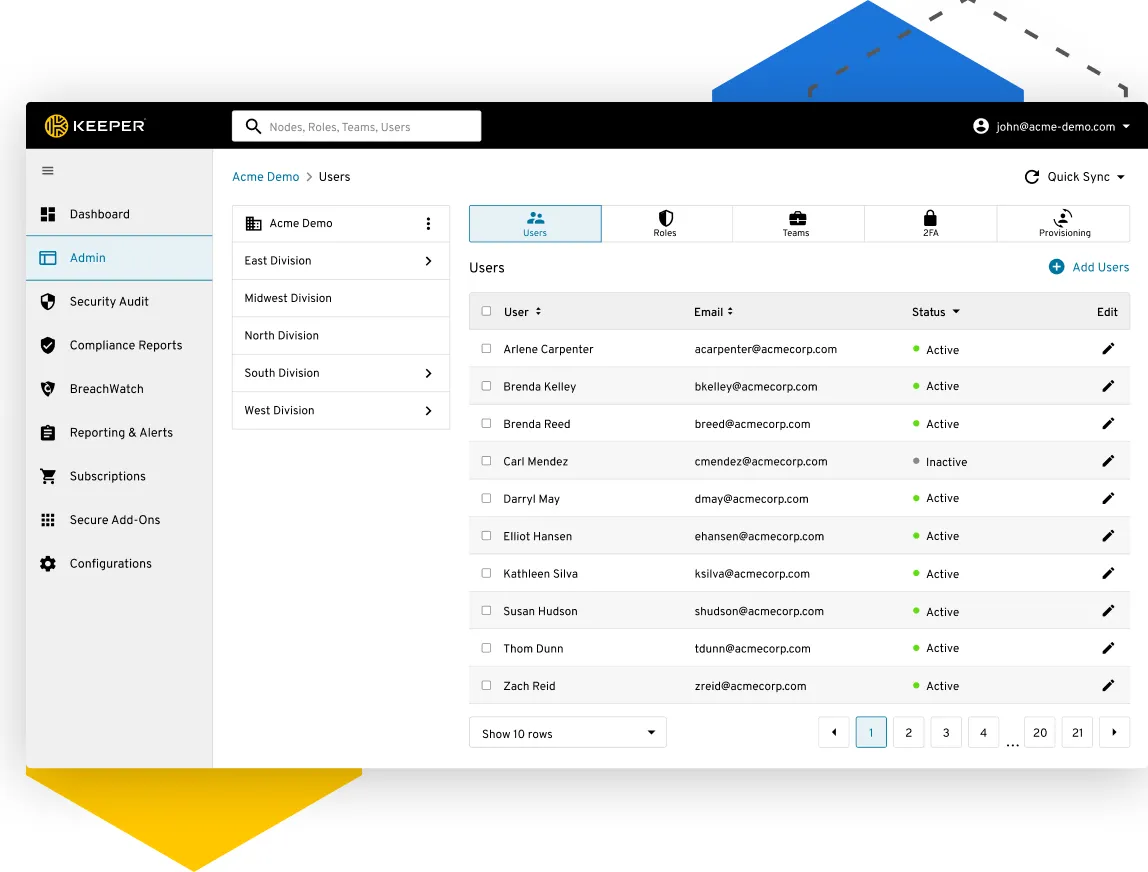
Admin Console
Distribute, manage and monitor Keeper across your entire organization and enforce password security, 2FA and other data security policies.
Shared Folders, Subfolders and Passwords
Securely create, share and manage both individual records and encrypted folders across teams or individual users.
Password Security Audit Score and Reporting
Gain visibility into your organization’s password security with robust reporting and auditing tools to enforce internal controls and maintain compliance standards.
Zero-Trust Architecture
Our zero-trust framework and zero-knowledge security architecture safeguard your information and mitigate the risk of a data breach.
Role-Based Access
Permissions can be fully customized through fine-grained access controls based on the role and responsibilities of each user.
Keeper Third-Party Attestations and Certifications

Ready to get started? Learn more about our two Keeper plans below!
Keeper Business
- Encrypted vault for every user
- Folders and subfolders
- Shared team folders
- Access from unlimited devices
- Policy engine and enforcements
- Security Audit
- Team management
- Basic Two-Factor Authentication (SMS, TOTP, smartwatch and FIDO WebAuthn)
Keeper Enterprise
- Everything in Keeper Business, plus:
- Single Sign-On (SAML 2.0) authentication
- Automated Team Management
- Advanced Two-Factor Authentication (DUO & RSA)
- Active Directory and LDAP sync
- SCIM and Microsoft Entra ID (Azure AD) provisioning
- Email auto-provisioning
- Command line provisioning
- Developer APIs for password rotation and backend integration
1IBM/Ponemon Cost of Breach 2017 2Cybercrime Magazine 3Verizon 2018 Data Breach Incident Report 4Cision