Simple brute force attacks
Simple brute force attacks involve guessing every possible password combination until one works. They may be time-consuming, but they are highly effective against short or weak passwords.
Cyber Threat: Brute Force Attack
A brute force attack is a cyber attack in which a cybercriminal systematically attempts a high volume of username and password combinations until they find a match. Unlike attacks that exploit software vulnerabilities, brute force attacks target weak or reused passwords. Improving password security and authentication methods has become essential for every user and organisation to protect their data and systems.
Brute force attacks rely on automated tools to generate and test millions of username and password combinations in rapid succession until they find a match. Cybercriminals use stolen credential databases, lists of commonly used passwords and algorithmic variations to mimic how people typically create passwords. Once a match is found, cybercriminals gain access to their victim's account, enabling data theft, privilege escalation or fraud. Because these attacks can be distributed across large botnets, their activity can blend into normal traffic.



Simple brute force attacks involve guessing every possible password combination until one works. They may be time-consuming, but they are highly effective against short or weak passwords.

Dictionary attacks automate login attempts using lists of commonly used passwords or phrases. Instead of testing random character strings, cybercriminals prioritise likely options, reducing the time spent to find a correct match.

Hybrid brute force attacks combine the coverage of simple brute force and the speed of dictionary attacks. They begin with common or leaked passwords, then substitute characters with numbers or symbols to mimic typical variations.
Credential stuffing uses previously compromised credentials to attempt to log in across multiple platforms. If users reuse passwords, cybercriminals can quickly gain access to more accounts and escalate the impact of a breach.
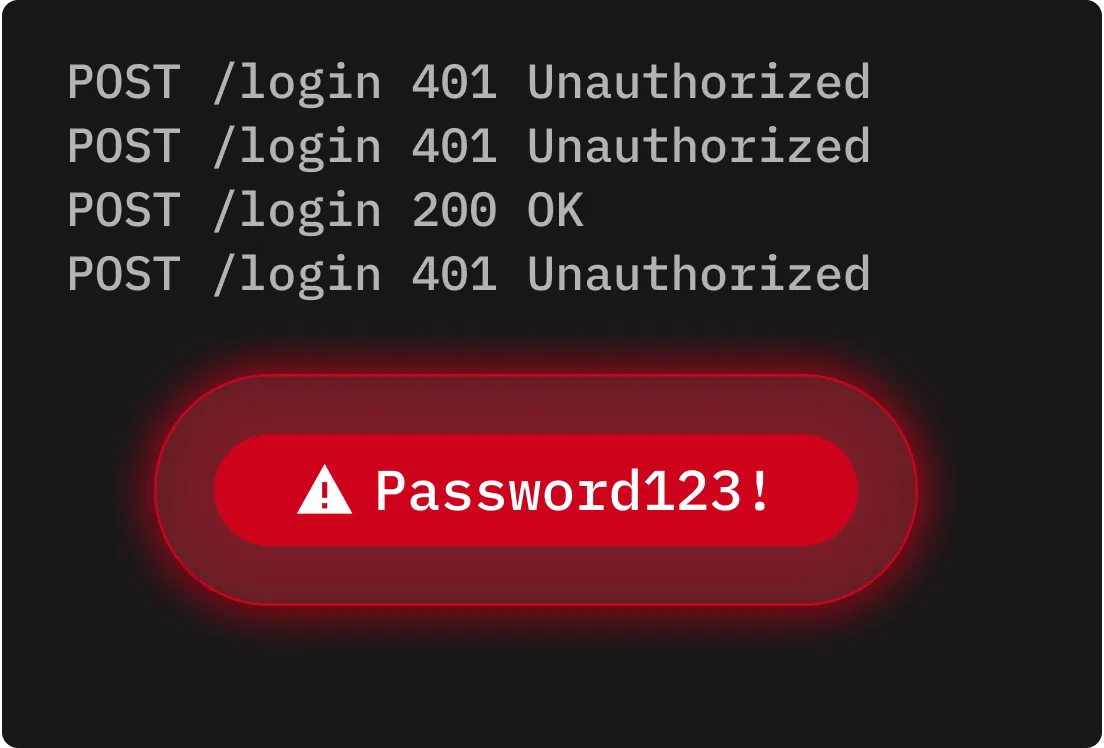
Reverse brute force attacks start with a single common password, like “123456,” and attempt to match it against thousands of usernames. This exploits the prevalence of weak or common passwords to increase the chance of a successful login.
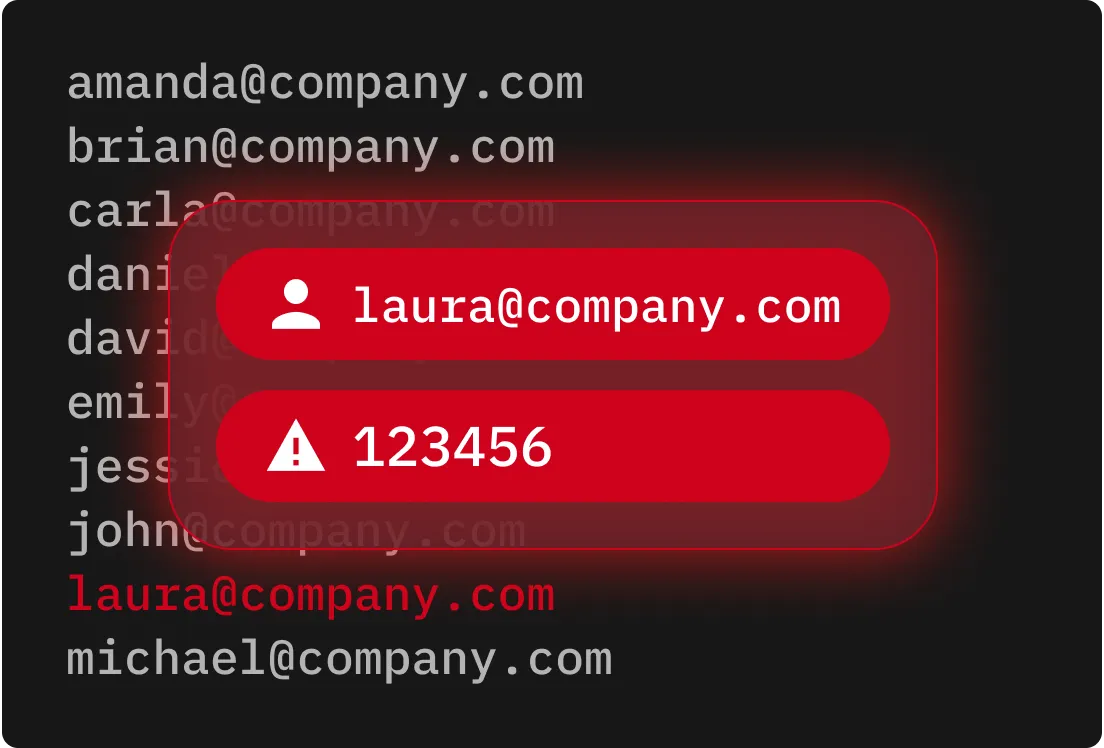
Password spraying targets many accounts using a small group of commonly used passwords. By limiting the number of login attempts per account, cybercriminals can avoid triggering lockout policies and security alerts.
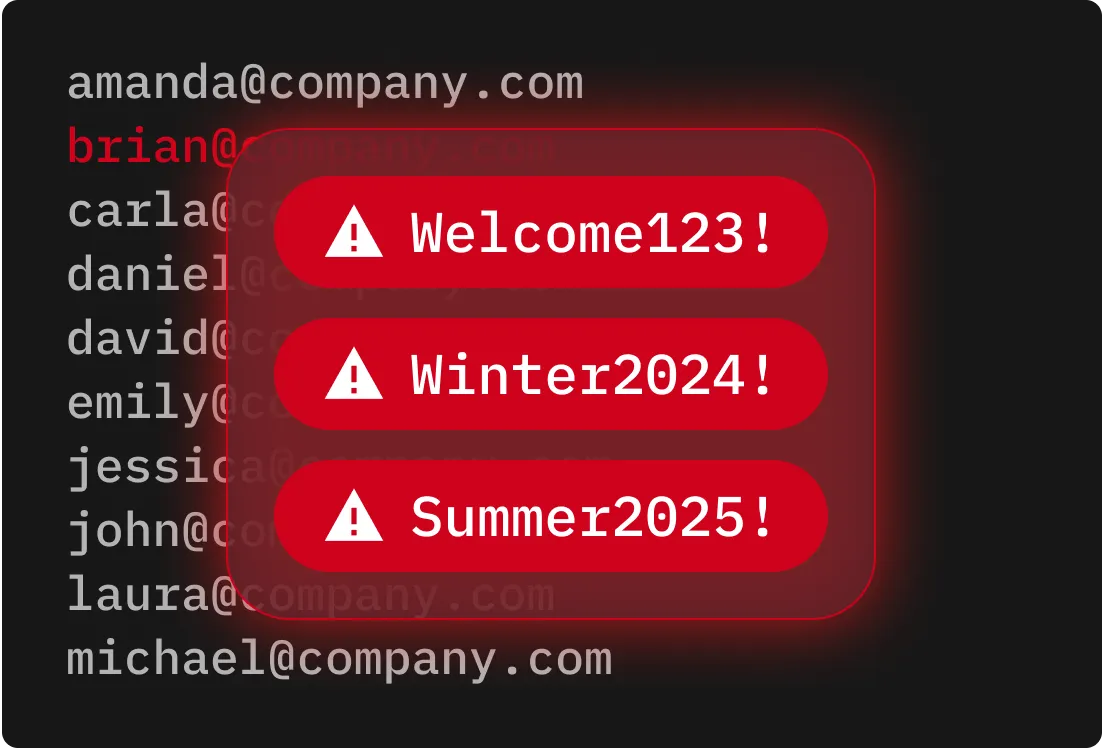
Brute force attacks thrive on weak, reused passwords, so protecting your accounts with long, complex passwords and passphrases is a must.
MFA adds another layer of protection because even if a password is compromised, a cybercriminal cannot access your account without the second factor.
Security solutions can detect behavioral anomalies and trigger real-time alerts when suspicious login activity occurs, stopping brute force attacks before accounts are compromised.
Orphaned or forgotten accounts are valuable to cybercriminals, making it crucial to audit all accounts and remove inactive ones. Enforce least-privilege access to reduce the risk of overprivileged accounts being exploited.
Store passwords and authentication data in encrypted formats, both in transit and at rest, to stop cybercriminals from exploiting exposed credentials. Even if cybercriminals gain access to stored data, encryption makes it unusable and protected.
Implementing account lockouts reduces repeated failed login attempts, making brute force attacks more difficult to execute and easier to detect.
Keeper prevents brute force attacks by replacing weak and reused passwords with strong, unique ones for every account. With MFA support and advanced monitoring, Keeper prevents unauthorised access and alerts IT administrators about suspicious activity in real time. By combining zero-knowledge encryption with enforcement policies, Keeper helps both individuals and organisations prevent brute force attacks before they turn into full-scale data breaches.
You must accept cookies to use Live Chat.