An Accountant’s Cybersecurity Guide
5 Easy Ways to Maximise Security and Mitigate Risk
The cliche “an ounce of prevention is worth a pound of cure” has never been more true for accounting security. Just ask the security professionals at Deloitte Touche Tohmatsu Ltd., who are reeling from a late September attack, the scope of which is still unknown. The cybercriminals who targeted Deloitte were able to gain access to the firm’s Microsoft Entra ID (Azure) cloud because the account was only protected by a single, weak password with no two-factor authentication in place.
Simple Measures Accountants Can Take to Maximise Cybersecurity
Accounting computer systems are brimming with information that attackers covet. Fortunately, the vast majority of attacks can be prevented with a few simple measures. Follow this guide for easy ways that a password manager and secure digital vault could prevent similar data breaches. Your clients will appreciate you for it.
1 Enforce Strict Password Policies
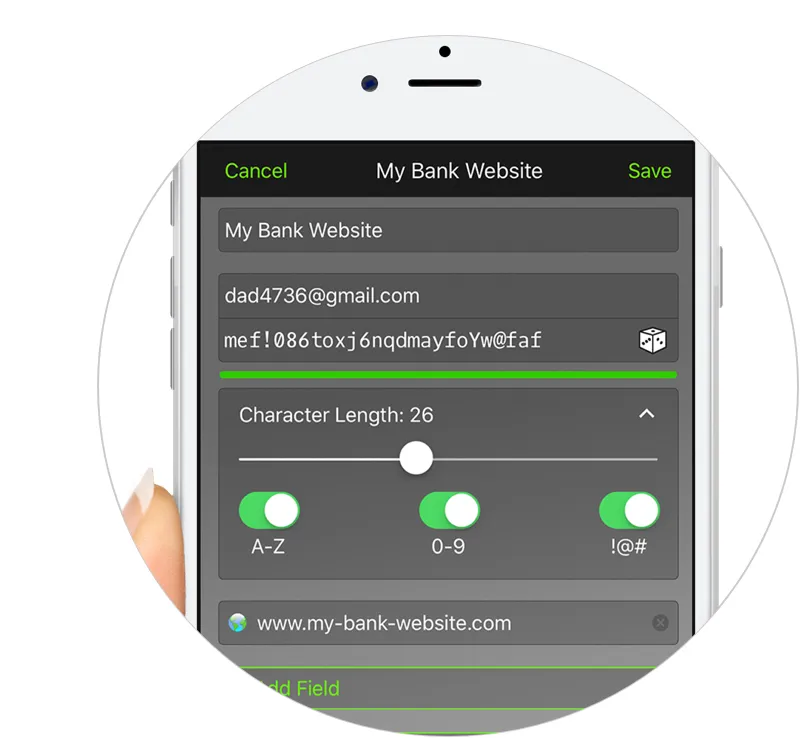
Although most commercial accounting software products are designed to be fairly secure, regulating secure access to those systems falls in the hands of the user and becomes the weakest security link. It is crucial that anything that contains secure data is protected by a strong password. A password manager, like Keeper’s leading password manager and digital vault, can automatically create high-strength, random passwords that make it nearly impossible to hack.
A password manager also allows administrators to assign a complex password to an employee without giving the employee the ability to see the characters of the password. The employee can then log into web services without ever being tempted to write the password down or share it with another employee. Further, if an employee leaves your organisation, simply delete or change the password record.
2 Increase Your Document Security
Like most industries, accounting firms have moved their documents online for greater speed, efficiency and convenience. The difference is that accountants are privy to highly sensitive client data. Often, documents containing secure data are downloaded and stored locally as simple, unguarded text files. They are also shared internally and with clients over email, which is notoriously insecure. Combined, these practices leave sensitive data wide open for cybercriminals to steal.
A much more secure method is to share files within the confines of Keeper’s encrypted vault. When sharing secure information, either internally or with an outside client, place the file within the secure digital vault and share the encrypted record with anyone with a free Keeper account.
3 Extend Security Measures to Employee-Owned Devices
With the rise of BYOD policies and the infiltration of smartphones and tablets for business, accounting firms must ensure that an employee’s mobile device use does not weaken their cybersecurity posture. While extremely convenient, without the right security precautions, employee-owned devices can be a troublesome gateway to your client’s data. This is a growing problem, as illustrated by The Ponemon Institute’s 2018 State of SMB Cybersecurity report showing that 50% of a small business’ data is accessible from a smartphone.
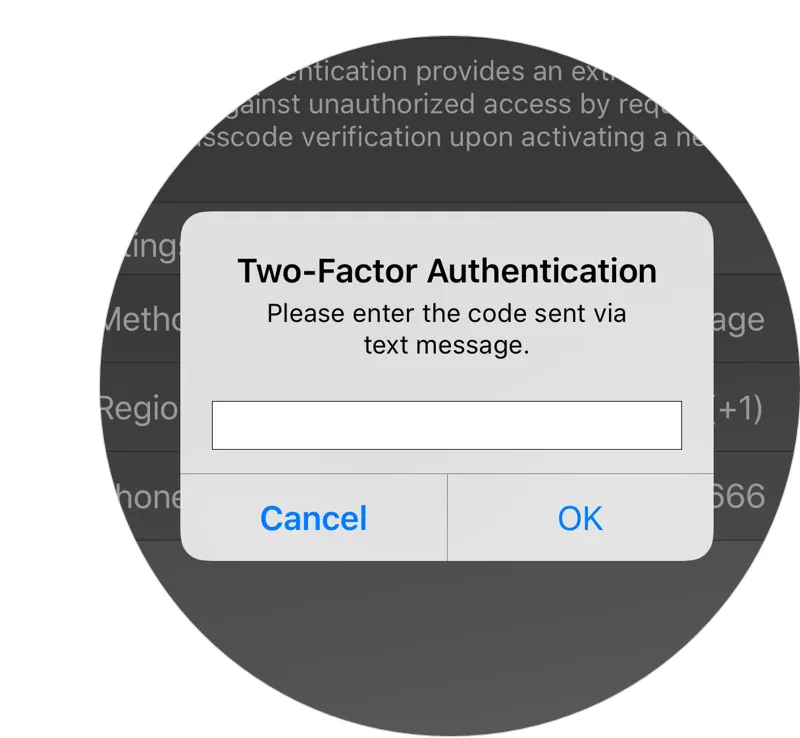
Accounting firms should never access or host sensitive information on a mobile device unless it is protected by two factor authentication. For the sake of convenience, many people use a simple PIN, pattern match or biometric protection. Research has shown that PINs and patterns can be guessed by human or video observation, and that even face and fingerprint recognition systems don’t provide absolute protection. At a minimum, a combination of the two is needed to properly guard a mobile device. Keeper DNA® was developed as enhanced two-factor authentication to add the necessary device security and is embedded in all Keeper mobile applications.
More about using Keeper Password Manager and Secure Digital Vault
- Start a Free Trial of Keeper’s Password Manager and Digital Vault for Business
- The Future of Accounting Technology - Delivering Innovative Cybersecurity Solutions: SlideShare
- Exclusive Research Report: The 2018 State of SMB Cybersecurity
- Read How Keeper Has Helped Financial Services Companies In The Past: Case Study
4 Increase Your Document Security
Email is a major vulnerability point. As previously mentioned, accountants should not use email to send clients their returns or other documents, and should instead share them from within a secure, encrypted vault. It is equally important to ensure that your office staff is on high alert for phishing attacks, in particular spear phishing, which targets specific individuals. Accountants are primary targets because of the value of information they hold. Savvy spear phishers are so good at trickery that their emails may be almost impossible to detect. Teach colleagues to look closely at originating email addresses and never click on a link unless they are certain where it takes them.
By storing all employee login credentials in a password manager, employees will be less likely to fall for a phishing scam. They will be in the habit of only logging in using the URL and hidden passwords. When employees have never known the actual password values, they cannot be tempted to type it into a phishing site or email.
5 Work Remotely, Smartly
Remote work has increased dramatically across all industries. Whether working from home, traveling for business or checking email while in transit, employees are expected to be able to keep working regardless of location. Although the ability to work on the go offers increased flexibility, it also creates increased opportunities for data breaches.
Accountants should never use public Wi-Fi services to access or exchange sensitive information. Cybercriminals can easily tap into public data streams and intercept data exchanged in plain text format. If you’re planning to use a public computer, invest in VPN software for-end-to-end encryption, or be sure that all data exchanged stays within the encrypted vault.
What Information Do Cybercriminals Target Accounting Professionals For?
Accountants hold a special place of honor in the cybercriminal community. They’re privy to the kind of information that commands some of the highest premiums on the dark web of stolen data. That makes them prime targets for all manner of cyber thieves. They are also especially vulnerable to damage from attacks. Clients trust their accountants as stewards of highly sensitive information. A breach can be devastating to an accounting firm’s reputation.
Accounting computer systems are brimming with information that attackers covet, including:
Client Social Security numbers
Cyber criminals can use this information to unlock a wealth of fraud and identity theft opportunities. This includes signing up for credit cards under stolen identities and compromising bank and healthcare accounts through social engineering. Once attackers have a Social Security number, they’re halfway to their goal of disrupting clients’ lives.
Address, phone number and date of birth
All standard fields on a 1040 form, this is the rest of the information attackers need to create fictitious credit accounts and hijack existing ones.
Names of spouses, children, places of employment and annual income
Also useful in identity fraud, spouse and street address names can be used to get past security barriers such as challenge questions. Together with the other private information noted above, attackers may be able to successfully talk their way past customer representatives to gain access to financial accounts.
Health records
1099-HC forms and medical receipts reveal a bounty of information that cybercriminals can use for insurance or prescription fraud. In fact, health records currently fetch the highest price on stolen information exchanges.
Employer information
Criminals who can access Employee Identification Numbers, payroll information and contact names in an organisation’s accounting department can file fraudulent expense reports, invoices and insurance claims.
Financial records
Year-end tax financial documents that clients give their accountants usually include account numbers. Taxpayers also routinely share receipts that include credit card information. These can be used for check and credit card fraud, or to access accounts through social engineering.
Email addresses
Armed with a bank account and email address, a cybercriminal may be able to hijack online banking and stock accounts through a simple “forgot password” process. Email addresses can also be spoofed, enabling the criminal to send realistic-looking messages to others that appear to come from a legitimate sender.