Complex legacy systems
Many federal agencies still rely on legacy systems. These systems are difficult to patch, don't support modern authentication protocols and often lack integration with current cybersecurity tools. Their complexity and fragility make them resistant to change, leaving gaps that adversaries can exploit. Even routine security upgrades can be disruptive, causing delays and compounding risk.
Compliance requirements
Federal entities are subject to an evolving landscape of compliance mandates, such as FISMA, NIST 800-63B and executive orders that mandate stricter access control and data protection practices. Meeting these requirements is challenging due to fragmented environments and limited visibility into who has access to what. Auditing privileged user actions, demonstrating least privilege and producing compliance reports can be resource-intensive.
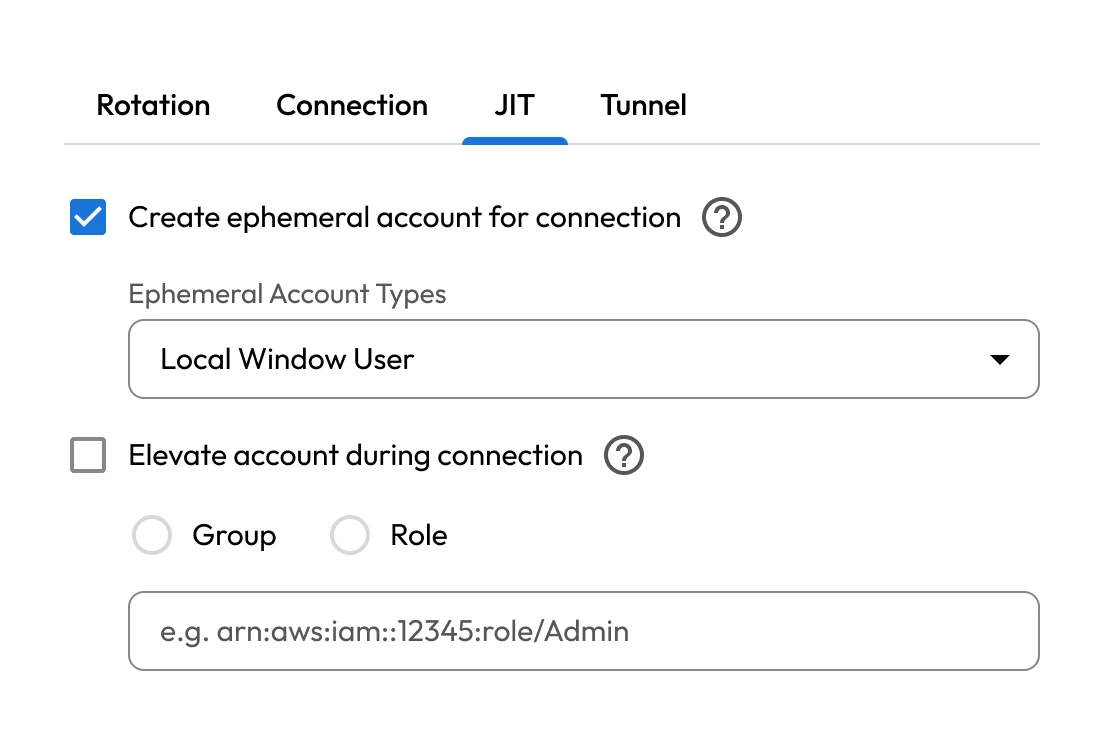
Adopting zero trust
The journey to zero trust requires all Department of Defense (DoD) components to adopt and integrate zero trust capabilities across their systems, architectures and budgets. Many agencies struggle to prioritize the cybersecurity solutions needed for this shift. Tightly managing privileged access is critical in zero trust, as these accounts pose the greatest risk if compromised and demand continuous oversight to protect sensitive data and operations.
Decentralized IT infrastructure
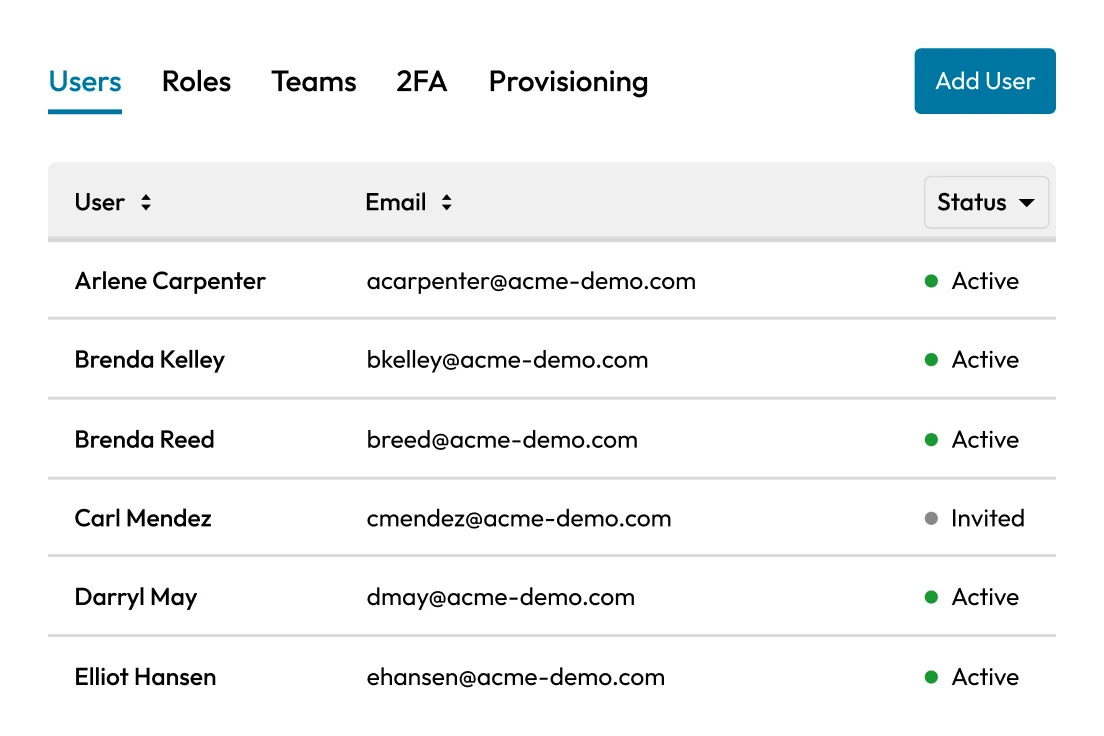
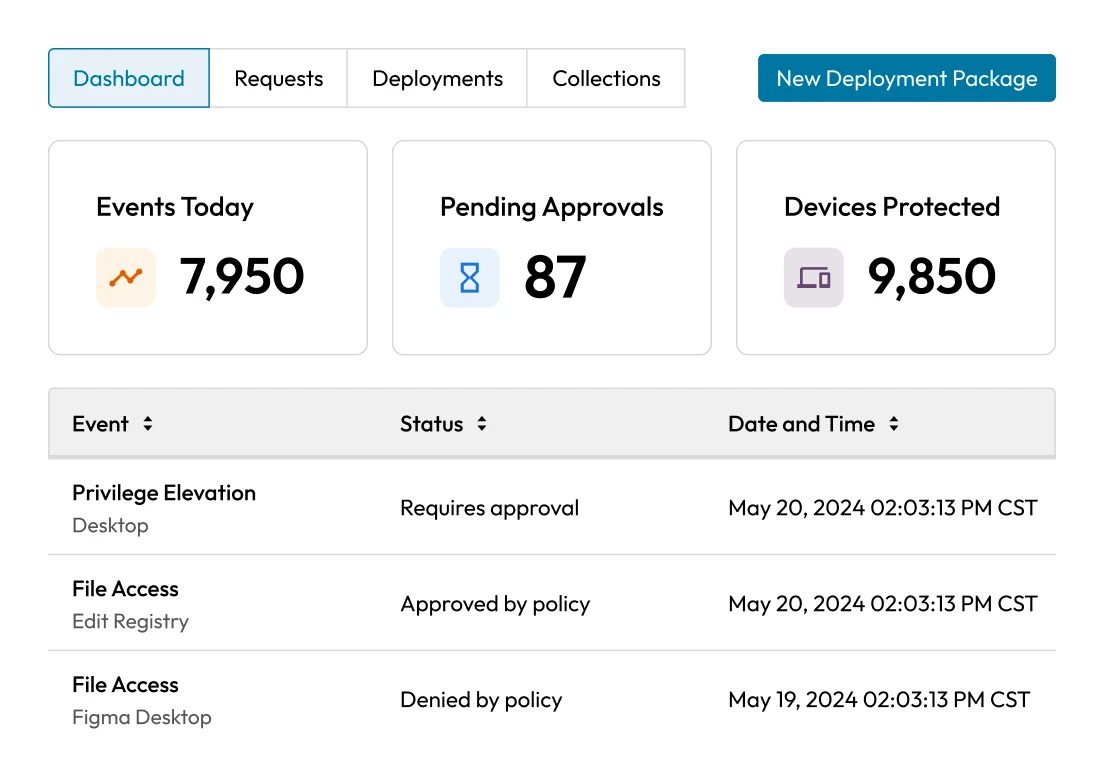
Government agencies often operate in perimeterless, multi-cloud environments, with systems spread across on-premises, cloud and remote locations. This fragmentation complicates enforcing access controls and monitoring privileged activity. A unified ICAM strategy requires centralized visibility and control over all users and devices, yet many agencies still lack this foundation, making risk management and incident response more difficult.
Budget constraints
Federal agencies are often asked to do more with less. Tight budgets, inflexible procurement processes and competing priorities make it hard to invest in comprehensive security programs. Modern cybersecurity requires investment in tools, talent and training, all of which may be constrained. This can result in reliance on manual processes or legacy tools that are ill-equipped to address modern threats.
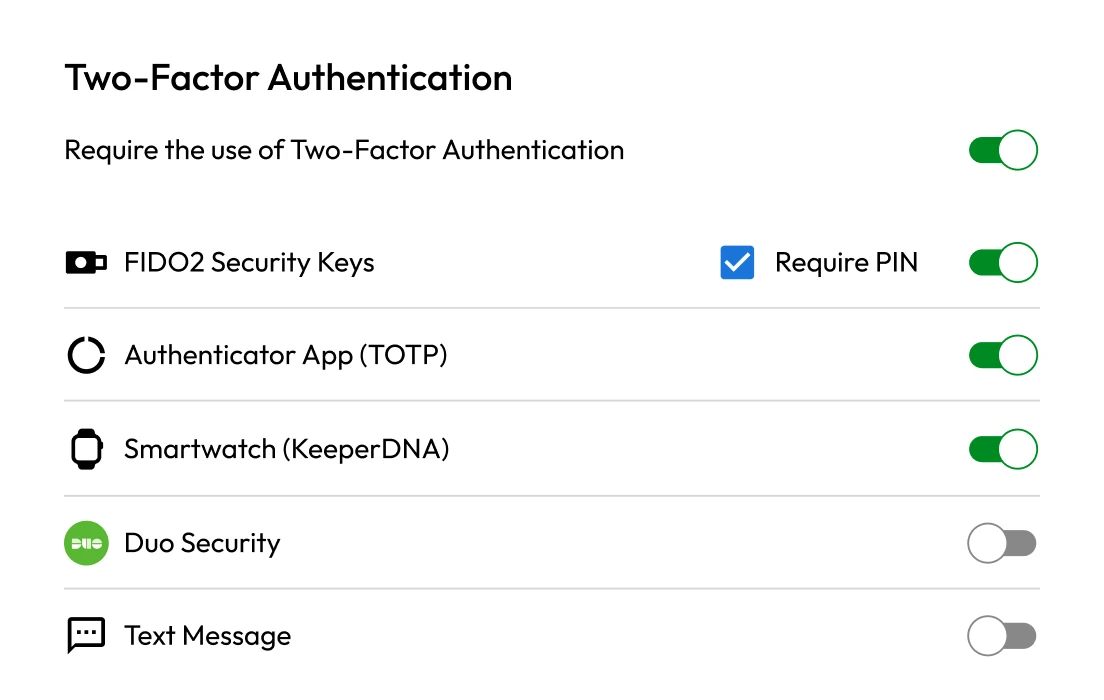
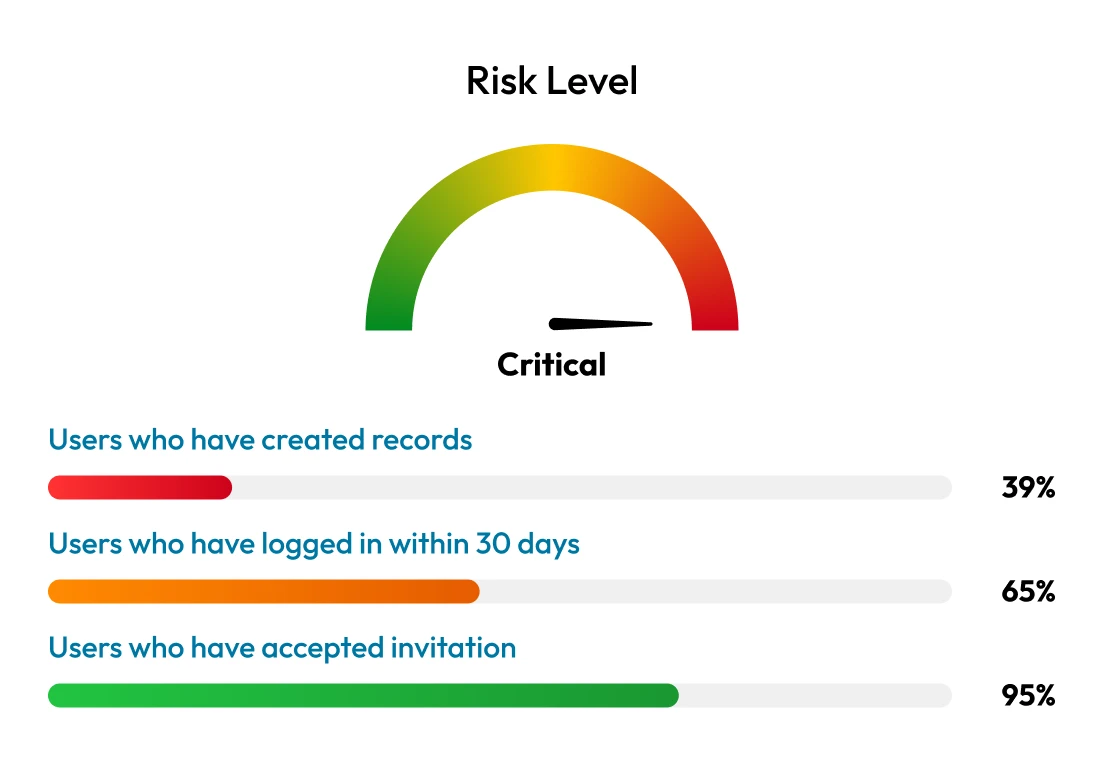
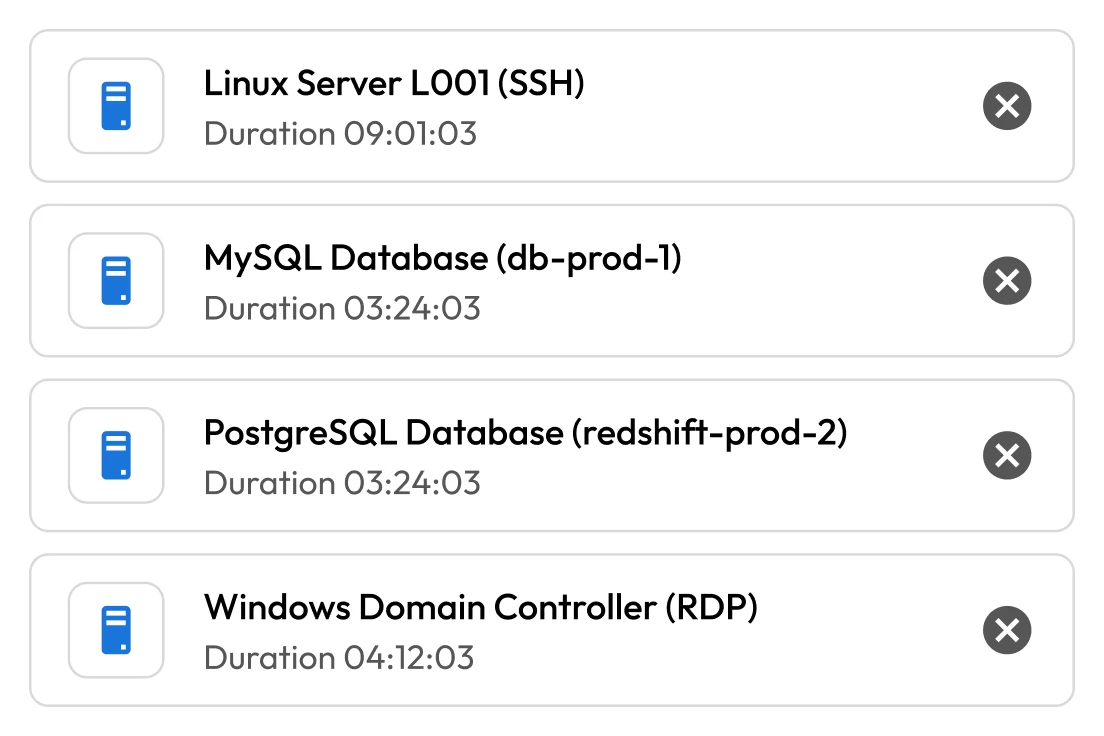
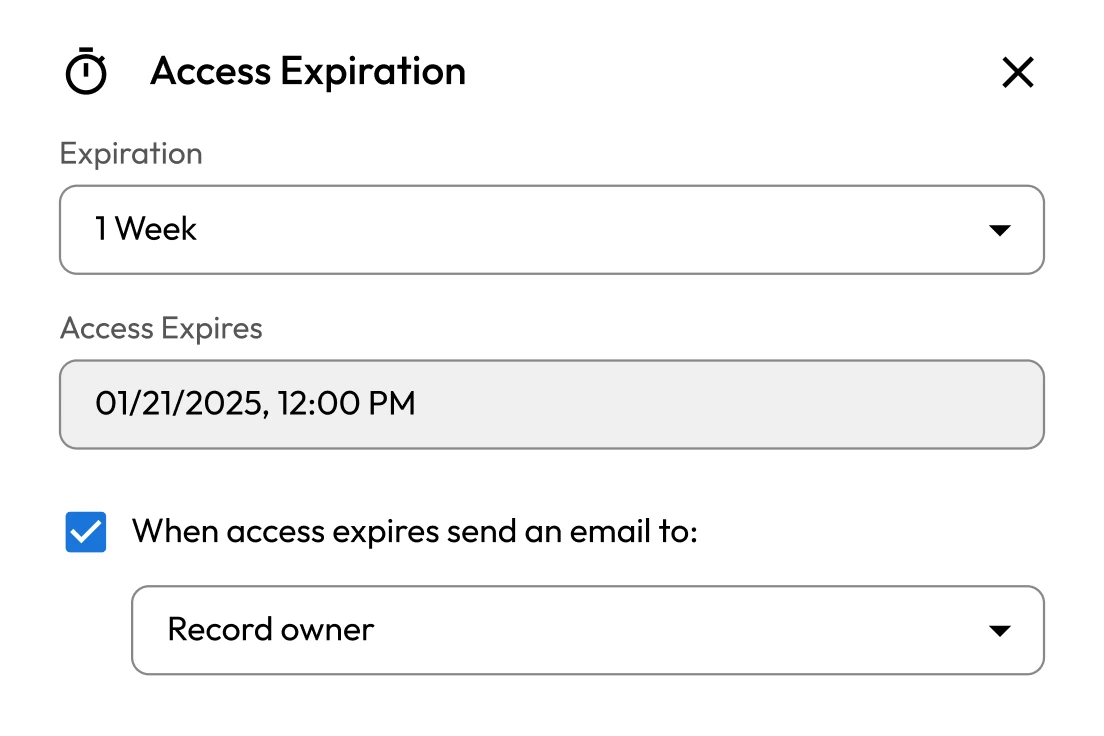
Unmanaged privileged credentials
Privileged accounts grant access to the most sensitive systems and data within federal agencies. If compromised, they can allow adversaries to move laterally and access classified information. To protect national interests and uphold public trust, agencies must prioritize the secure management of privileged credentials. This helps strengthen cybersecurity and ensures compliance with federal mandates.