Protecting sensitive data
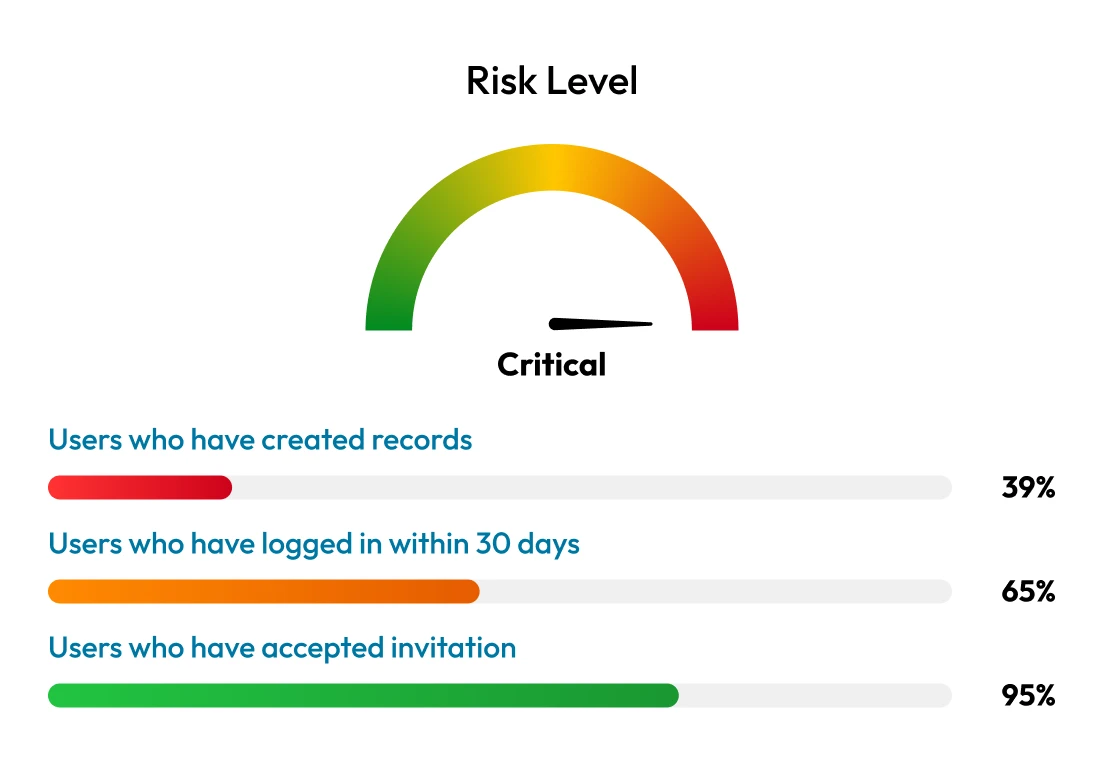
Retailers collect vast amounts of sensitive data, including payment details and personal information. This makes them attractive to cybercriminals but also places them under immense pressure to protect that data. A single breach can result in millions of dollars in losses and irreparable brand damage. Weak privileged access controls and unsecured cloud storage are often exploited to access and exfiltrate customer data.
Expanding attack surface
Retailers are rapidly adopting IoT devices, mobile apps and hybrid cloud systems. While these technologies enable efficiency and a better customer experience, they also increase the number of exposed endpoints and systems vulnerable to exploitation. Most retail IoT devices weren't designed with security in mind, which makes them easier for cybercriminals to exploit.
Complex IT environments
Retailers operate across widespread systems, from corporate offices and data centers to stores and e-commerce platforms. This distributed infrastructure makes it difficult to maintain consistent security policies, patch systems promptly and centrally manage privileged access. Retailers often rely on a mix of legacy systems and modern cloud tools, which creates integration challenges that cybercriminals can exploit if access controls are inconsistent.
Limited visibility
Retailers often lack comprehensive visibility across all endpoints and user activity. This makes it difficult to detect anomalous behavior or unauthorized access in real time. Without centralized SIEM tools, user behavior analytics or comprehensive logging of privileged sessions, cybercriminals can operate undetected for days or weeks.
Regulatory compliance
Retailers must comply with a growing list of cybersecurity and data privacy regulations, including PCI DSS, GDPR, CCPA and others. PCI DSS has strict requirements for access control, Multi-Factor Authentication (MFA) and activity logging. Failure to meet requirements can result in fines, legal action and restrictions on payment processing.
Third-party vendor risks
Retailers rely on third-party vendors for various services such as payment processing and customer support. However, third-party access is often over-provisioned or poorly monitored. Without enforcing least privilege, time-limited access and session auditing for vendors, retailers expose themselves to major supply chain risk and make themselves easy targets for breaches.