远程特权访问管理 (RPAM)
在不暴露凭据的情况下,安全地进行远程特权访问
无需 VPN,就可为员工、供应商和受信任的第三方提供对关键系统的特权远程访问 。
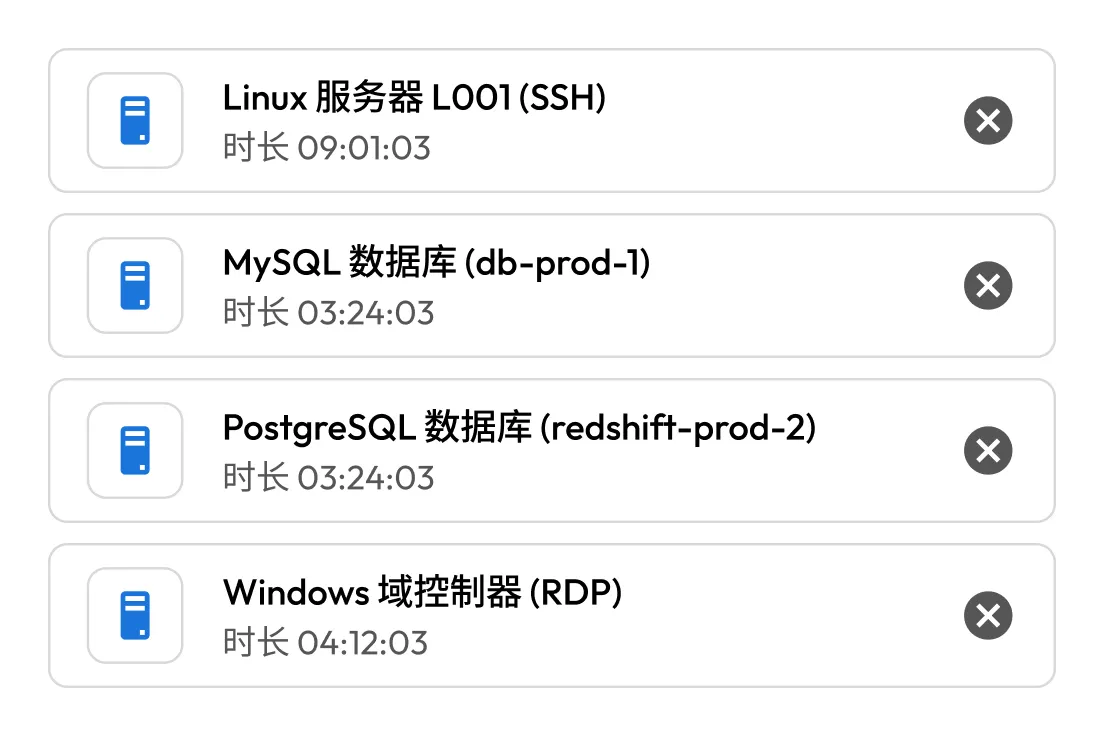
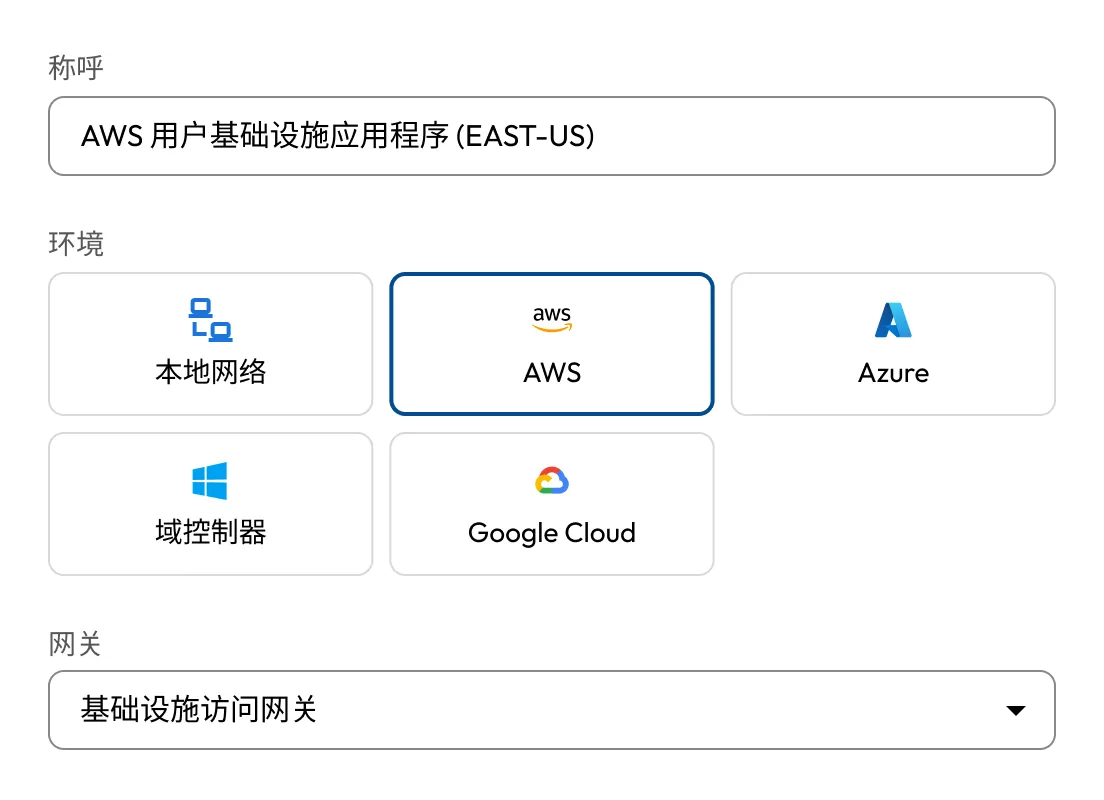
统一访问多云和本地基础架构。Keeper Gateway 为所有环境提供安全、加密的入口点。
通过加密隧道和凭证注入启用加密远程访问。无需更换防火墙,避免广泛的网络暴露,也不需要使用 VPN。
KeeperPAM 通过将所有特权连接路由至 Keeper 保管库,实现了安全的远程访问。这消除了对目标系统的直接访问需求,减少了攻击面,并简化了用户的远程访问。
Keeper Gateway 可建立到目标系统的出站加密隧道——无需代理、VPN 或防火墙更改。这简化了部署流程,同时在云端和本地环境中执行零信任原则。
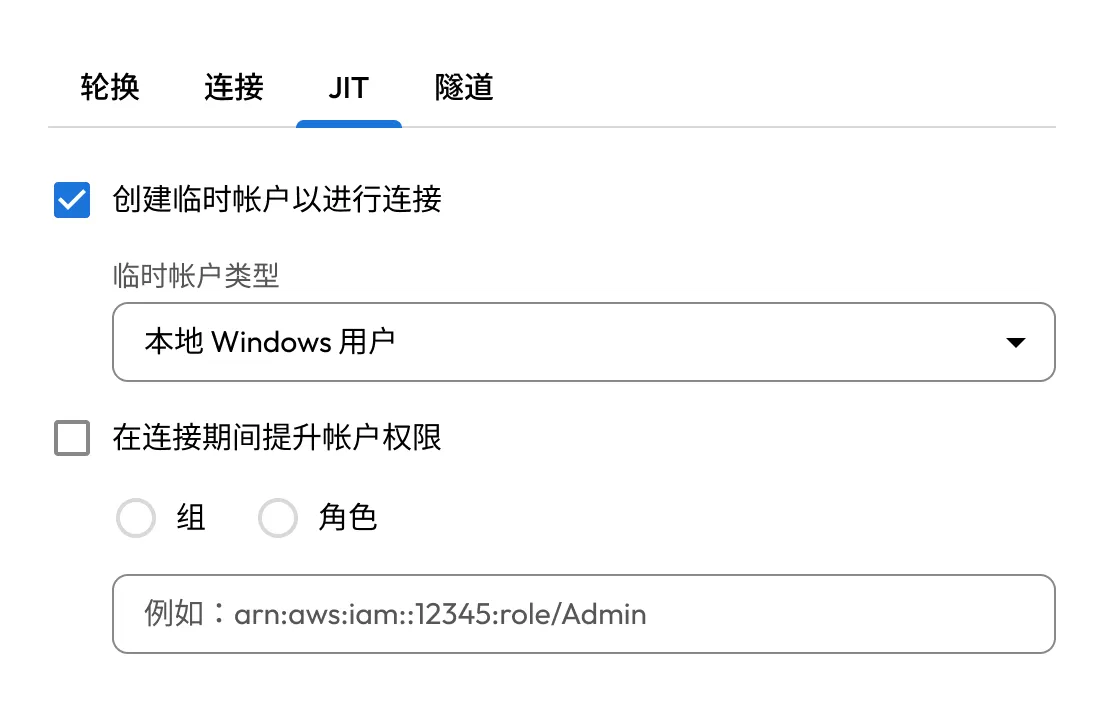
凭借 KeeperPAM,用户可以获得对基础设施的有时限的临时访问权限,而无需查看凭据或 SSH 密钥。撤销访问权限后,凭证可自动轮换,以防止重复使用并降低风险。
KeeperPAM 支持流行的开发和数据库工具,例如 PuTTY、pgAdmin 和 MySQL Workbench。用户可以直接从保管库发起加密隧道,保持安全访问而不改变工作流程。
在单一用户界面中集中管理跨 AWS、Azure、GCP 和本地系统的特权访问。在每个环境中部署的 Keeper Gateway 可确保跨分布式基础架构的策略执行一致性和可见性。
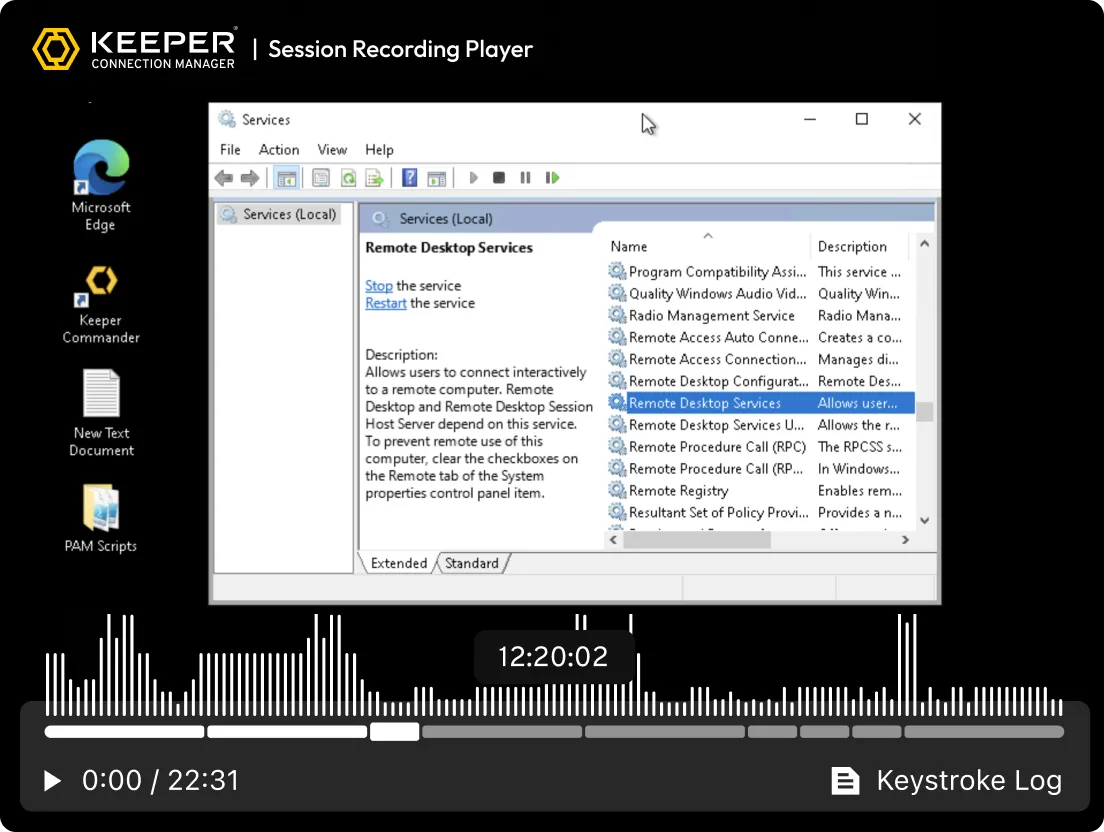
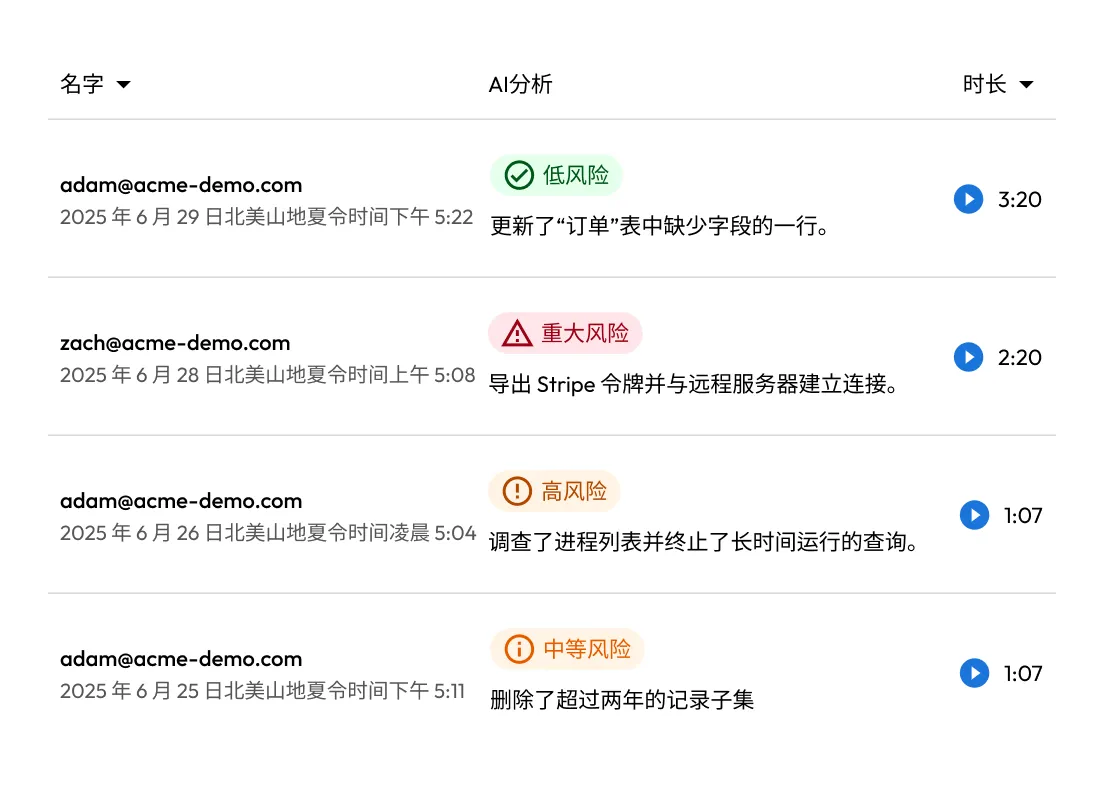
KeeperPAM 记录所有远程会话的屏幕和按键活动:SSH、RDP、VNC、数据库和浏览器。这确保了所有特权活动的合规性、审计准备就绪和问责制。
应用细粒度的基于角色的访问控制(RBAC),并在所有系统中强制实施多因素认证(MFA),即使是那些没有原生MFA的系统。
自动记录所有远程会话中的屏幕和键盘活动,包括终端、桌面、浏览器和数据库协议。录音经过加密,存储在云端,供审计、合规性检查及事件调查使用。
RPAM 是一种安全解决方案,允许内部和外部的特权用户,如 IT 管理员、第三方供应商和承包商,在不依赖传统 VPN 的情况下安全访问关键系统。它执行最小权限原则,保护敏感系统不被未经授权或过度访问。
RPAM 与 VPN 的区别在于,RPAM 侧重于控制特权访问,确保安全性,并严格执行最小特权原则。VPN 仅提供广泛、安全的网络访问,而不涉及管理谁可以访问哪些资源的具体细节。
随着远程和外部员工数量的增加,组织面临着新的网络安全威胁。挑战在于确保特权用户能够安全地远程访问系统和资源,同时不降低安全性、合规性或生产力。管理远程特权访问增加了复杂性,尤其是在需要基于 VPN 的访问时,这会降低 IT 管理员和最终用户的灵活性和效率。
KeeperPAM 旨在应对远程特权访问的复杂性,确保访问得到严格控制、实时监控,并符合合规要求。通过结合细粒度访问控制、安全会话管理、审计和合规功能,它解决了RPAM的挑战,帮助组织安全地管理特权访问,即使是远程员工也能做到。
特权用户需要提升权限才能执行敏感任务。确保这种访问安全需要在安全性、合规性和用户便利性之间找到平衡。当特权用户远程访问系统时,传统的 VPN 解决方案会带来更多复杂性并降低生产力,从而使 IT 团队在保护访问权限时面临更大挑战。
您必须启用 Cookie 才能使用在线聊天。