Privilege creep
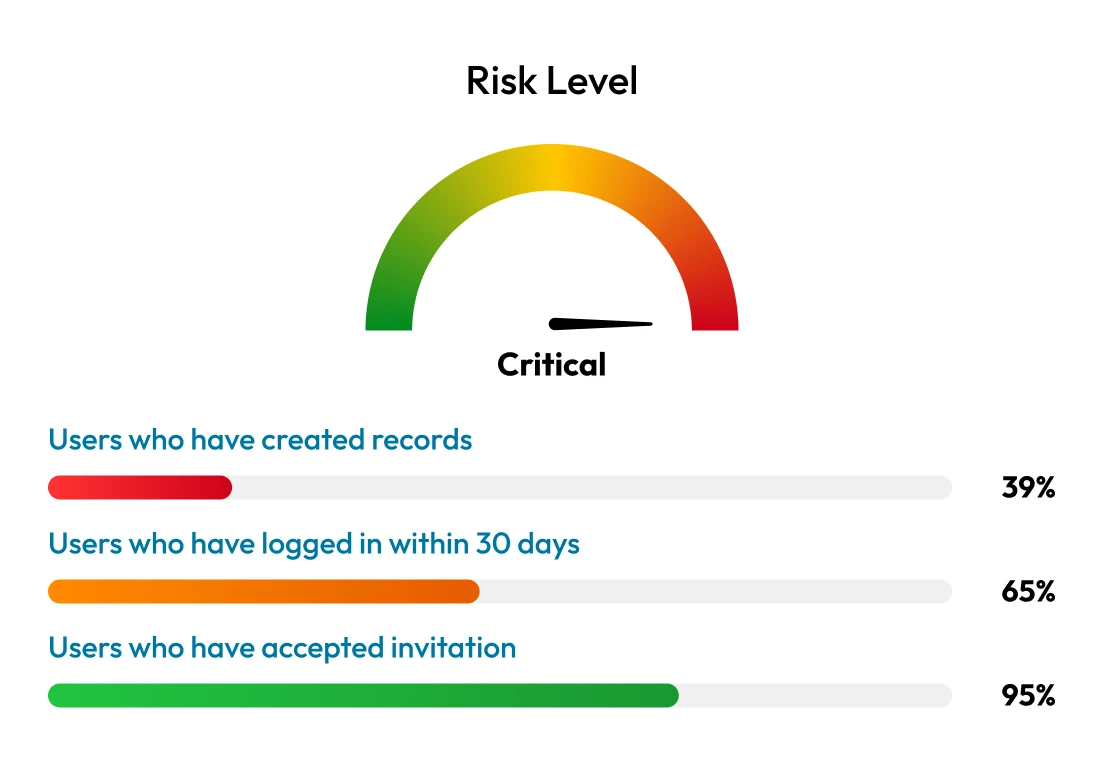
Privilege creep occurs when users quietly accumulate excessive access over time. In many firms, legacy systems, poor visibility and infrequent access reviews allow staff to retain permissions they no longer need. Over time, this creates hidden pathways for cybercriminals and makes it harder to detect malicious activity.
Lack of real-time oversight
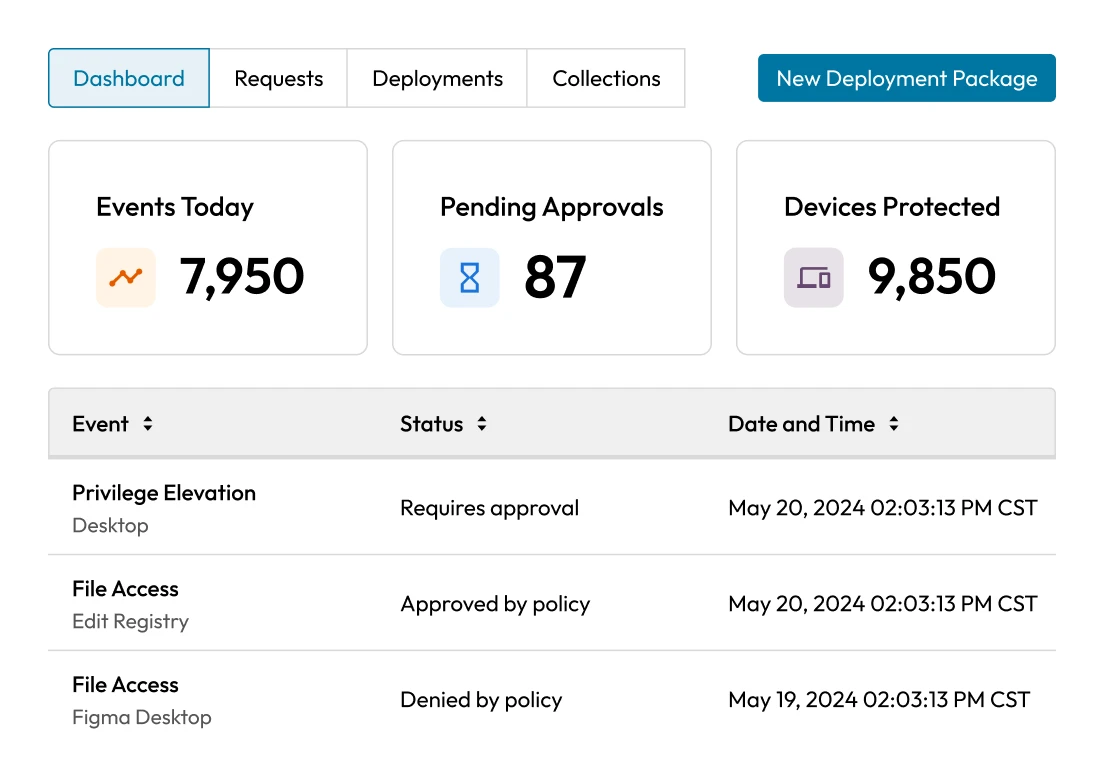
In banks and investment firms, privileged users often access critical systems like trading platforms, financial records and customer databases. Without real-time oversight, there's no way to immediately detect if an admin alters transaction logs or misconfigures security settings. These actions may not trigger alerts and are often discovered only during audits or after a breach.
Credential theft and lateral movement
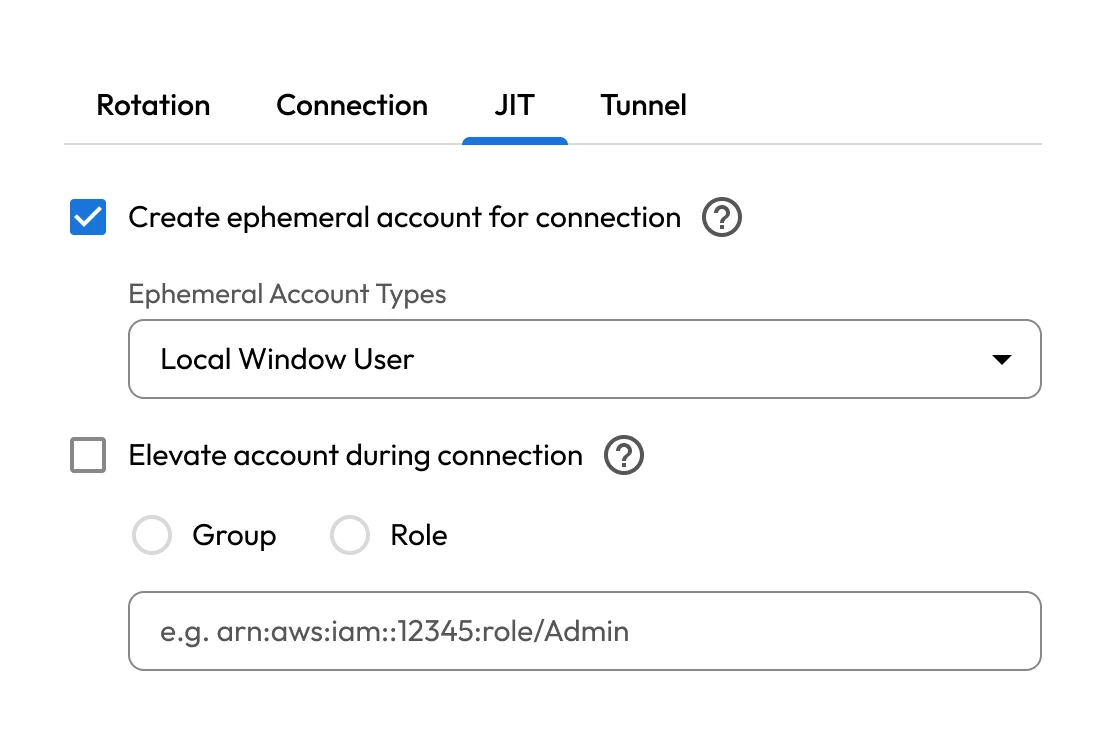
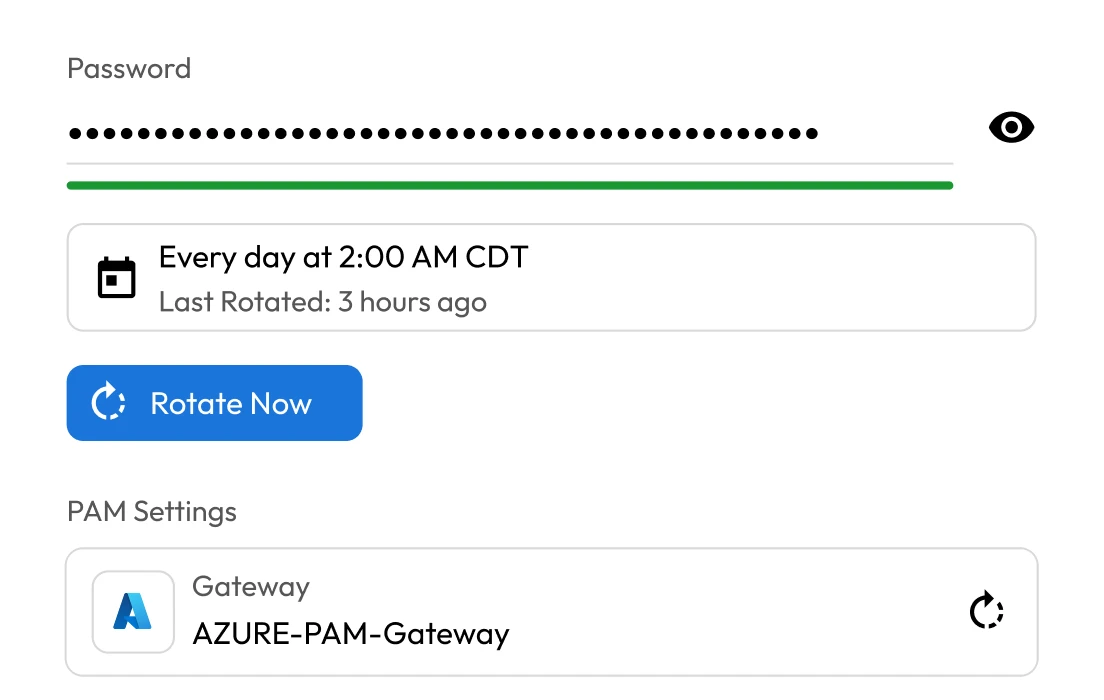
One stolen administrative credential in a financial institution can give cybercriminals trusted access to critical systems. Without controls to restrict scope, monitor activity or enforce least privilege, that single point of entry can give cybercriminals the ability to escalate their privileges and move laterally through the network.
Insider threats
Insiders with elevated access can misuse their privileges to steal data, alter transactions or bypass controls. In the financial sector, where access often extends to trading platforms, payment systems and customer records, these risks are especially serious. Without strict oversight and clear access boundaries, even trusted users can become a major security and compliance threat.
Regulatory compliance
The financial sector faces mounting pressure to meet complex regulations that require strict control over privileged access. Frameworks like SOX, GLBA and FFIEC demand clear oversight, auditability and least-privilege enforcement. Without centralized controls, even small gaps in access governance can lead to compliance failures, fines and reputational damage.
Third-party access
Banks and investment firms rely heavily on third-party vendors who often need privileged access to critical systems. If a vendor's credentials or systems are compromised, cybercriminals can bypass perimeter defenses and gain direct access to sensitive environments. Despite this risk, many institutions struggle to monitor, control and audit third-party access effectively.