Keeper protects organisations with zero-trust, zero-knowledge password management, security and encryption solutions.
Request a DemoEnterprise Password Management is Critical to Protect Your Organisation from Cybercriminals
Cybercrime is on the rise, and threat actors are launching sophisticated attacks that gain access to your business through stolen credentials. These credentials are often obtained by exploiting password vulnerabilities such as weak and reused passwords. Strong and unique passwords are necessary, but employees cannot remember the hundreds of passwords they typically need for their jobs. Users resort to reusing passwords that are easy to remember, but also easy for threat actors to guess. Stolen credentials are the root cause of most breaches, and this problem is growing as the attack surface expands in today’s multi-cloud, work-from-anywhere environment.
With over 80% of data breaches being related to weak or stolen passwords, credentials and secrets, cybersecurity must start with password security. Passwords are frequently the only thing protecting confidential business plans, intellectual property, network access, and confidential information belonging to employees and customers. Despite this, employees and contractors often use weak passwords and reuse them.
Moreover, organisations are unaware of the existential Dark Web threat, where cybercriminals transact on more than 20 billion stolen usernames and passwords from public data breaches, to target websites, applications, databases and systems. They do this because they know that more than 60% of the time, employees and contractors reuse the same password or use common-stolen passwords on multiple websites, applications and systems. This represents the most pervasive cyber attack landscape the world has ever seen. Every few seconds, an organisation is hit with a ransomware attack. Compounding the stolen credential problem is the fact that IT and security teams have no visibility or centralised control over the passwords used to access company assets.
Deploying a zero-trust password management platform is absolutely essential for preventing the most common data breaches. The software generates high-strength, random passwords and tracks security and compliance throughout the organisation. Implementing two-factor authentication (2FA) and role-based enforcement policies help keep businesses of any size safe from ransomware and other password-related data breaches.
Zero-Trust Password Management to Protect Your Workforce, Devices and Data
Zero-trust is a security model that enforces secure access to everything by everyone. All users and devices are authenticated and authorised before being granted access to critical networks, applications and data. It is a comprehensive framework that ensures maximum security without sacrificing performance and user experience.
Keeper uses best-in-class encryption technologies, multi-factor authentication, granular access controls, and sharing policies that may include business unit isolation. These capabilities ensure that access to critical resources is granted only when needed and only by authorised users.

Secure and Scalable Password Management that Easily Integrates with Your Security Infrastructure and Processes
Keeper deploys at enterprise scale across any number of users, from a small entity to organisations with hundreds of thousands of employees and contractors. Keeper seamlessly and quickly integrates with any on-premise or cloud-based identity solutions, including AD, LDAP, Entra ID (Azure), SCIM, as well as IdPs that are SAML compliant. This includes SSO solutions such as Entra ID (Azure), Okta, Centrify, BeyondTrust, JumpCloud, OneLogin and Ping Identity.
Keeper also provides developer APIs, which allow Keeper to be integrated with any type of on-premise, cloud-based, or hybrid-cloud environment. For event tracking and reporting, Keeper seamlessly integrates with all major security information and event management (SIEM) solutions, including Splunk, Sumo Logic, LogRhythm, IBM, DEVO and any system that supports Syslog-formatted events.

Zero-Knowledge Security Architecture
Keeper is fanatical about protecting customer data. Customer data is encrypted and stored in Keeper’s cloud server so that it is not visible to Keeper or third parties. Credentials, secrets, and other customer data are only accessible by the end user. All encryption and decryption is done on-the-fly on the client’s device, and the data is encrypted both in-transit (TLS) and at rest on Keeper’s Infrastructure (AES-256). The plaintext version of the data is never available to Keeper Security employees nor any outside party.

Complements and Extends Your Single Sign On Solution
Employees use weak passwords and still forget them. Gartner found that up to 50% of helpdesk calls are for password resets, and another study showed each call costs more than $30. SSO solutions were created to address this problem, but many legacy (and even many newer) applications don’t support SAML protocols. It’s important to note that SSO solutions perform authentication - not end-to-end encryption. Many privileged access accounts don’t use passwords, so storing encryption keys, digital certificates and access keys are use cases that SSO solutions don’t cover.
Applications and use-cases that don’t support SAML protocols fall through the cracks with an SSO deployment. Privileged access users, such as IT admins and security professionals, need one secure location to store and find all their (non-SSO) passwords, digital certificates, SSH keys, access keys, API keys, and more. These assets need the same role-based access, fine-grained control of policies and ability to share and revoke as the SSO assets.
Keeper works with any application or use case that uses a password. Every employee is provided a secure, cloud-based digital vault that stores passwords and other critical information, such as encryption keys and digital certificates. Keeper generates strong, random passwords and automatically fills them for users. This saves them time and frustration, and it eliminates the need for them to reuse and remember passwords.
In fact, many SMBs can meet all their IAM needs in a very cost-effective way with Keeper alone. For organisations that require SSO Solutions, Keeper is a perfect complement for the legacy applications and other use cases that SSO misses. Keeper SSO Connect® works with popular SSO IdP platforms, such as Okta, AWS, OneLogin, Ping Identity, F5 BIG-IP APM, Google Workspace, JumpCloud, and Microsoft ADFS and Microsoft Entra ID (Azure AD) to provide businesses the utmost authentication flexibility.
Fully-Integrated Multi-Factor Authentication (MFA), Including Passwordless Authentication
Passwords are not enough when it comes to protecting your critical resources. Adding additional factors to the authentication process significantly increases security.
Multi-factor authentication is recommended as a best practice by the US National Institute of Standards & Technology (NIST) to reduce risk. MFA offers additional layers of security beyond credentials and the factors fall into three categories: “something you know,” “something you have,” and “something you are.” Passwords are “something you know.” Adding other factors into the authentication process strengthens security.
Keeper supports several 2FA methods that include “something you have” and “something you are” factors. Supported 2FA methods include Keeper SMS, FIDO2 WebAuthn devices, Passkeys, Duo Security, RSA SecurID, time-based one-time password (TOTP) applications such as Google Authenticator, and Keeper DNA-compatible wearable devices like the Apple Watch or Android Wear.
Passwordless solutions offer a frictionless login experience and support biometrics such as fingerprints and face recognition. Keeper SSO Connect®, which is included in Keeper Enterprise, seamlessly integrates with all popular passwordless authentication platforms, including Trusona, Veridium, HYPR, Secret Double Octopus, Traitware and PureID.
Least-Privilege Access to Critical Systems and Infrastructure
As a component in Keeper’s Zero Trust architecture, Keeper includes granular and flexible policies for least-privilege access control. As Keeper adds new applications to the platform, and as customers’ compliance requirements increase, Keepers’ access control capabilities are continuously being tuned to offer the most granular functionality in the market. Keeper’s access control model follows the current guidelines established by the public and private sectors.
While role-based access control, or RBAC, is used for tight security controls, attribute-based access control (ABAC) is used in situations requiring more dynamic and flexible policies. As Keeper expands its access control model to include more fine-grained policies in support of least-privileges, Keeper is extending the RBAC model to include elements of ABAC. This hybrid RBAC and ABAC access control model offers the strengths of both models while providing maximum flexibility and control.
Keeper includes elements of ABAC through the use of team and record attributes. For example, a user might be in a role that allows them to share records containing secrets, but they’re also on a project team that restricts the sharing of these records with secrets. This person can share these secrets when given access as an individual, but they cannot share these secrets when only given access to the secrets via the project team. Additionally, specific secrets may have attributes used to control access, such as record type (e.g. bank card, database, SSH Key) or time-based access restrictions. The resource or record attributes, in combination with the user attributes (e.g. role, team, organisational unit (node) will be combined to determine the effective least-privilege access to that specific set of records.)
This hybrid RBAC and ABAC model reduces administrative load, reduces the number of user roles needed, and provides the most granular access controls to meet the requirements of least-privilege access for all your business situations.
Secure Sharing of Passwords, Credentials and Secrets
Each user has a set of public and private encryption keys used for encrypting their vault, sharing password records, and sending messages to other Keeper users. Shared information is encrypted with the recipient's public key. Keeper’s record sharing methodology is easy to use, secure and intuitive. It supports fine-grained access controls for sharing information with privileged users, non-privileged users, technology partners, contractors and other third parties.

Dark Web Monitoring
Keeper BreachWatch continuously compares your passwords to current scans of stolen credentials from data breaches, malware-infected devices, and other underground sources. Alerts are immediately sent to users and administrators when compromised passwords are found. These early warnings allow users and administrators to take action before becoming victims of account takeover, ransomware or online fraud.

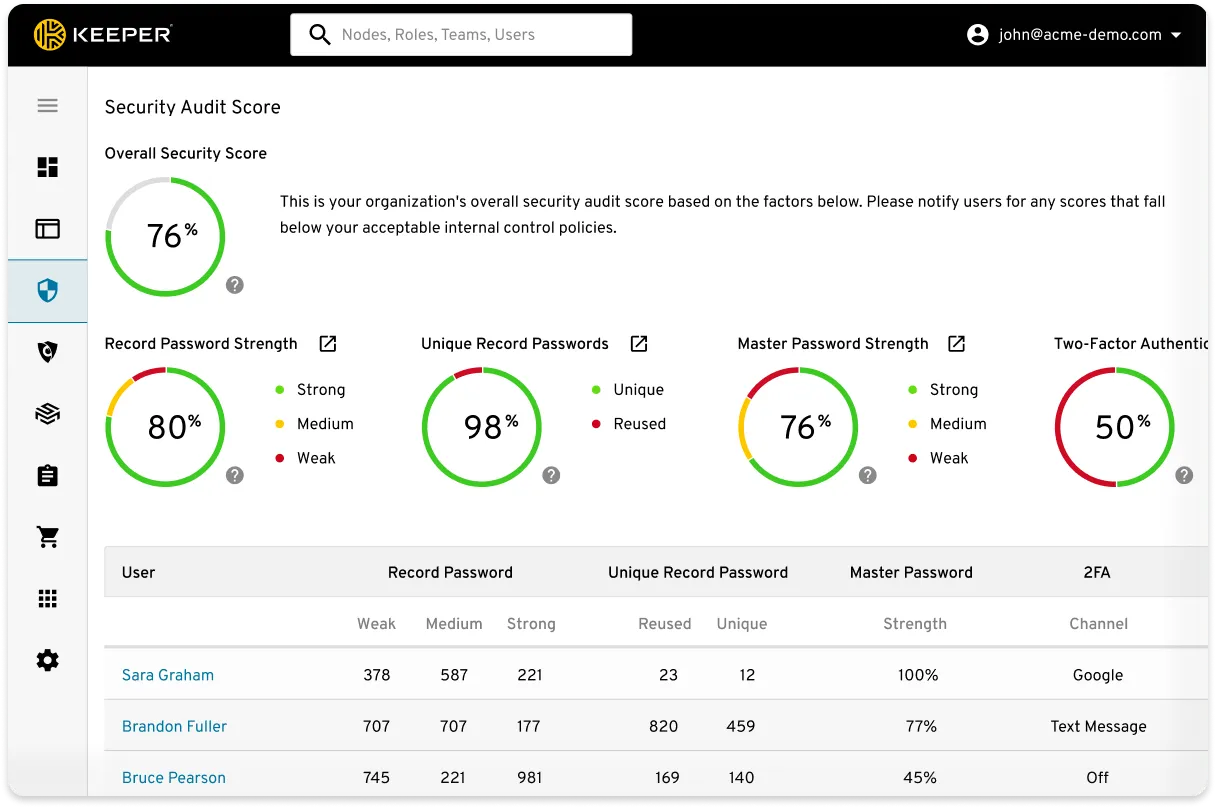
Security Auditing
Conformance with audit compliance mandates is an essential component to protect your company against data breaches and internal threats. Keeper tracks and logs all user activity related to over 100 event types, including those related to passwords and logins. Keeper supports compliance audits by monitoring these events, generating customised reports and real-time notifications, and integrating into third-party SIEMs.
The logs and reports provide detailed information about user and administrator activity that is needed for security auditing (e.g. GDPR, PCI, ISO, SOC and NCUA).
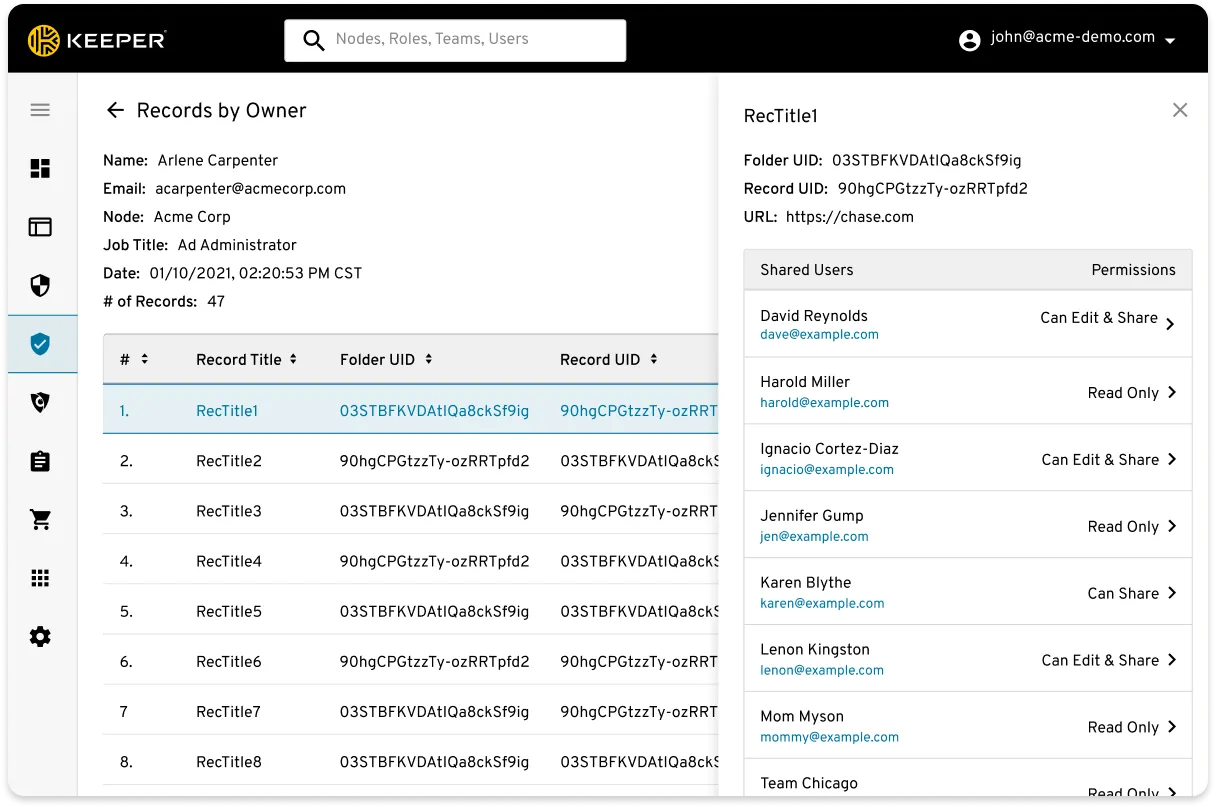
Compliance Reporting
Compliance regulation costs are on the rise, and staffing budgets are constrained. Distributed remote work has exponentially increased the attack perimeter for cybercriminals. Auditing access control policies has become more critical than ever.
Keeper’s reports are fully customisable and provide on-demand visibility of access permissions to your organisation’s credentials and secrets. As Identity and Access Management (IAM) cybersecurity regulations increase, organisations require comprehensive policies and tools to ensure compliance. The ability to audit and control access to credentials and sensitive information is critical to obtain compliance and prevent data breaches.
Audit and finance teams require cost-effective tools that enable remote auditing, monitoring and event reporting. These reports reduce the time and cost for compliance auditing. The compliance reports follow zero trust and zero knowledge because the data is visible and under the control of privileged administrators.
The report builder is easy to use and fully customisable. The reports allow administrators to see the access permissions by user, for all records in their enterprise. Report previews by user are available for viewing and exporting prior to generating the final report. This is useful for user permission validation and editing.
Market-Leading Security Infrastructure and Policies
Keeper holds the longest-standing SOC 2 attestation and ISO 27001 certification in the industry. Keeper utilises best-in-class security, with a zero-trust framework and zero-knowledge security architecture that protects customer data with multiple layers of encryption keys at the vault, shared folder and record levels.
