Einfache Brute-Force-Angriffe
Bei einem einfachen Brute-Force-Angriff werden alle möglichen Passwortkombinationen ausprobiert, bis eine funktioniert. Es mag zwar zeitaufwändig sein, ist aber gegen kurze oder schwache Passwörter äußerst wirksam.
Cyber Threat: Brute-Force-Angriff
Bei einem Brute-Force-Angriff handelt es sich um einen Cyberangriff, bei dem ein Cyberkrimineller systematisch eine große Anzahl von Benutzernamen- und Passwortkombinationen ausprobiert, bis er eine Übereinstimmung findet. Im Gegensatz zu Angriffen, die Software-Schwachstellen ausnutzen, zielen Brute-Force-Angriffe auf schwache oder wiederverwendete Passwörter ab. Die Verbesserung der Passwortsicherheit und der Authentifizierungsmethoden ist für jeden Benutzer und jede Organisation unerlässlich geworden, um ihre Daten und Systeme zu schützen.
Bei Brute-Force-Angriffen werden automatisierte Tools eingesetzt, um Millionen von Benutzernamen- und Passwortkombinationen in schneller Folge zu generieren und zu testen, bis eine Übereinstimmung gefunden wird. Cyberkriminelle nutzen gestohlene Anmeldedatenbanken, Listen häufig verwendeter Passwörter und algorithmische Variationen, um die Art und Weise nachzuahmen, wie Menschen normalerweise Passwörter erstellen. Sobald eine Übereinstimmung gefunden wird, erhalten Cyberkriminelle Zugriff auf das Konto ihres Opfers, was Datendiebstahl, Rechteerweiterung oder Betrug ermöglicht. Da diese Angriffe über große Botnetze verteilt werden können, kann ihre Aktivität im normalen Datenverkehr untergehen.



Bei einem einfachen Brute-Force-Angriff werden alle möglichen Passwortkombinationen ausprobiert, bis eine funktioniert. Es mag zwar zeitaufwändig sein, ist aber gegen kurze oder schwache Passwörter äußerst wirksam.

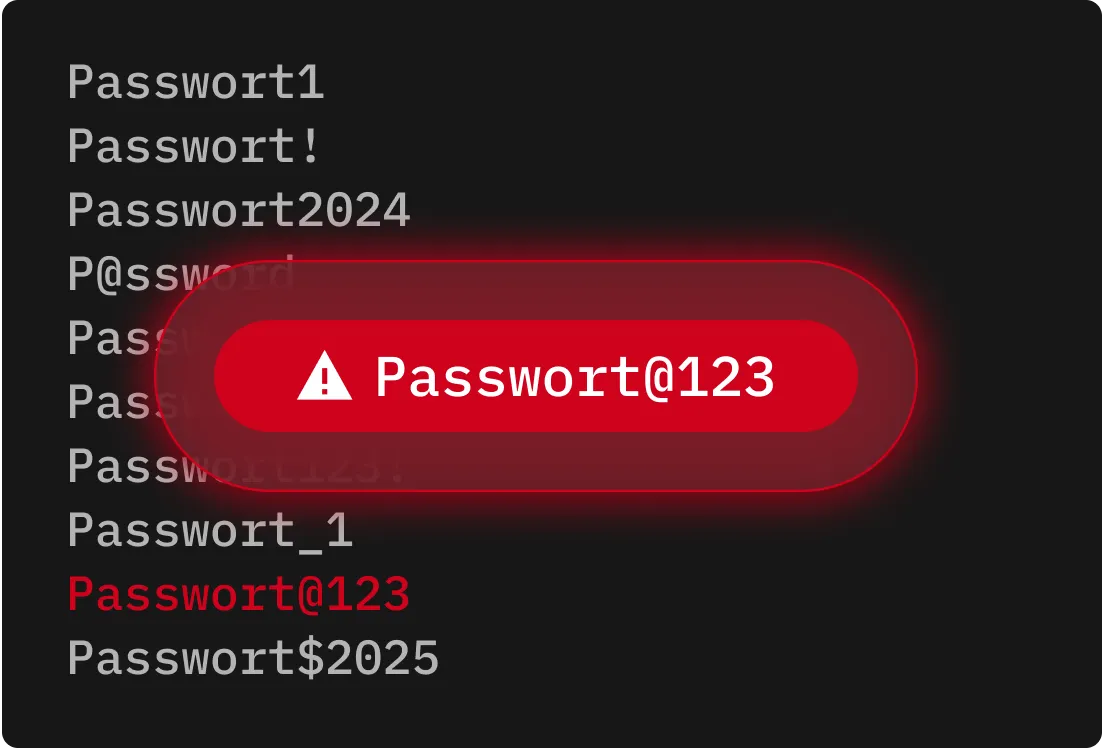
Wörterbuchangriffe automatisieren Anmeldeversuche mithilfe von Listen häufig verwendeter Passwörter oder Phrasen. Anstatt zufällige Zeichenketten zu testen, priorisieren Cyberkriminelle wahrscheinliche Optionen, wodurch sich die Zeit für die Suche nach einer korrekten Übereinstimmung verkürzt.

Hybride Brute-Force-Angriffe kombinieren die Reichweite einfacher Brute-Force-Angriffe mit der Geschwindigkeit von Wörterbuchangriffen. Sie beginnen mit gängigen oder durchgesickerten Passwörtern und ersetzen dann die Zeichen durch Zahlen oder Symbole, um typische Variationen nachzuahmen.
Beim Credential Stuffing werden zuvor kompromittierte Anmeldeinformationen verwendet, um sich auf verschiedenen Plattformen anzumelden. Wenn Benutzer Passwörter wiederverwenden, können Cyberkriminelle schnell Zugang zu mehr Konten erlangen und die Auswirkungen eines Datenlecks vergrößern.
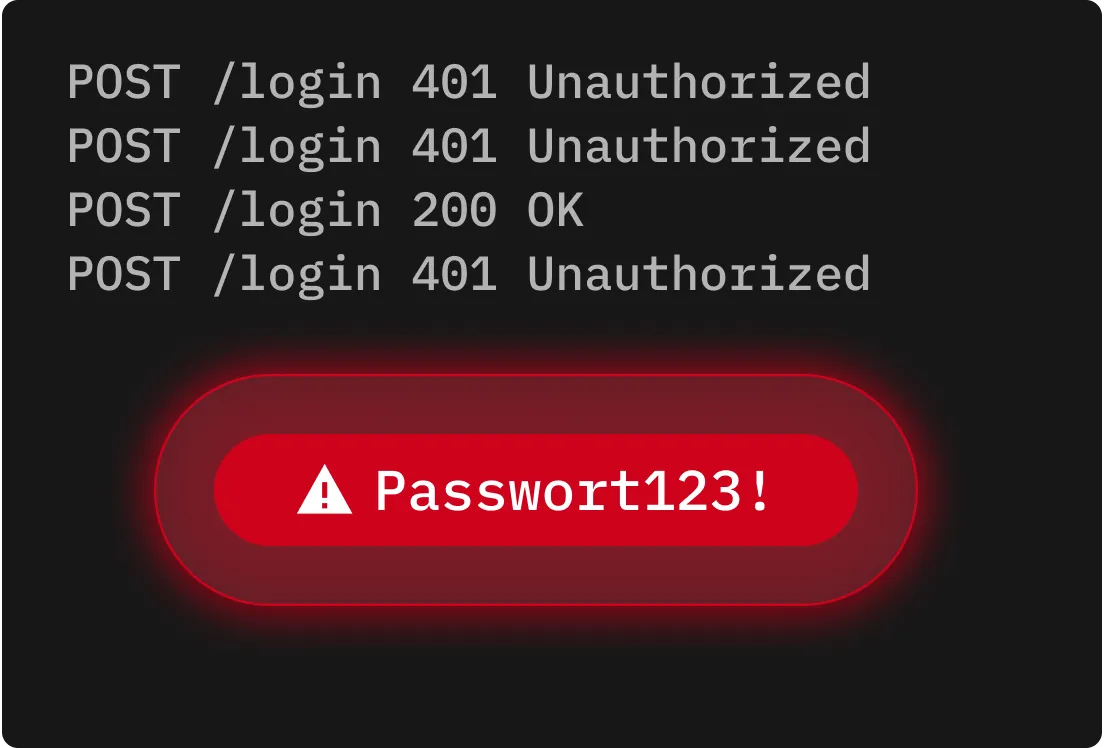
Beim Reverse-Brute-Force-Angriff geht man von einem einzigen gängigen Passwort aus, wie zum Beispiel „123456“, und versucht, dieses mit Tausenden von Benutzernamen abzugleichen. Hierbei wird die Verbreitung schwacher oder gängiger Passwörter ausgenutzt, um die Wahrscheinlichkeit eines erfolgreichen Logins zu erhöhen.
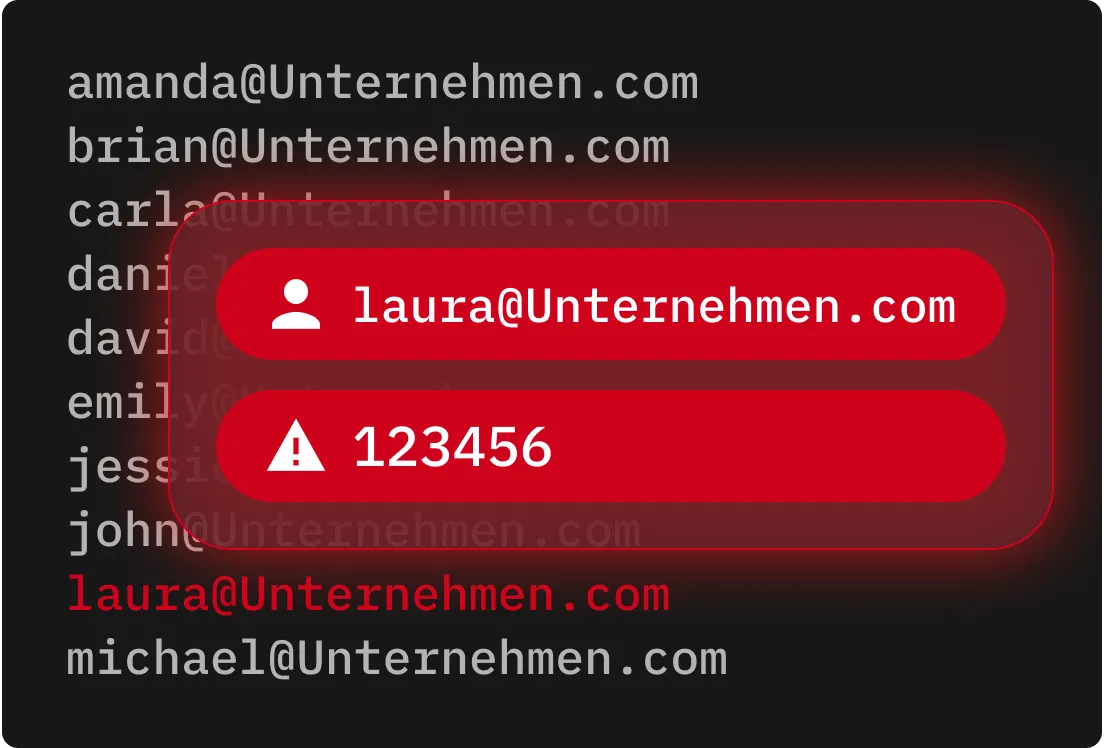
Beim Passwort-Spraying werden viele Konten mit einer kleinen Gruppe häufig verwendeter Passwörter angegriffen. Durch die Begrenzung der Anmeldeversuche pro Konto können Cyberkriminelle die Auslösung von Sperrrichtlinien und Sicherheitswarnungen vermeiden.
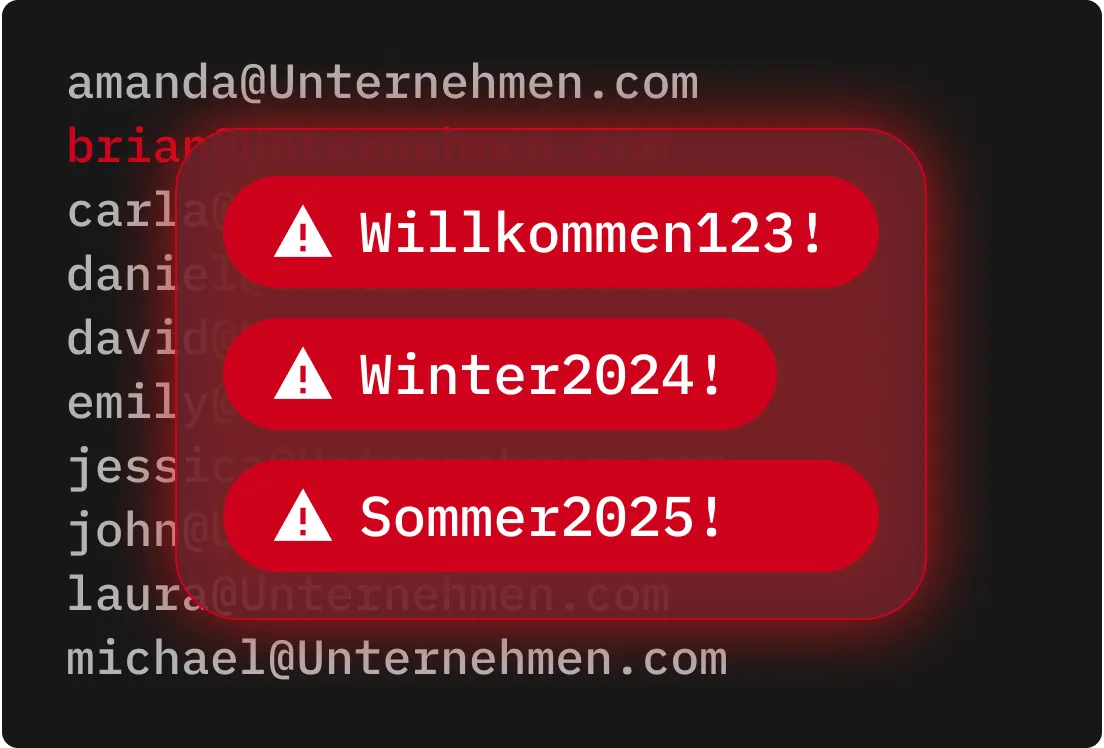
Brute-Force-Angriffe profitieren von schwachen, wiederverwendeten Passwörtern. Daher ist der Schutz Ihrer Konten mit langen, komplexen Passwörtern und Passwortphrasen unerlässlich.
MFA bietet eine zusätzliche Schutzebene, denn selbst wenn ein Passwort kompromittiert wird, kann ein Cyberkrimineller ohne den zweiten Faktor nicht auf Ihr Konto zugreifen.
Sicherheitslösungen können Verhaltensanomalien erkennen und bei verdächtigen Anmeldeaktivitäten Echtzeitwarnungen auslösen, wodurch Brute-Force-Angriffe gestoppt werden, bevor Konten kompromittiert werden.
Verwaiste oder vergessene Konten sind für Cyberkriminelle wertvoll, weshalb es unerlässlich ist, alle Konten zu überprüfen und inaktive zu entfernen. Setzen Sie den Zugriff mit geringsten Berechtigungen durch, um das Risiko zu verringern, dass Konten mit übermäßigen Berechtigungen ausgenutzt werden.
Speichern Sie Passwörter und Authentifizierungsdaten in verschlüsselten Formaten, sowohl während der Übertragung als auch im Ruhezustand, um Cyberkriminelle daran zu hindern, offengelegte Zugangsdaten auszunutzen. Selbst wenn Cyberkriminelle Zugriff auf gespeicherte Daten erlangen, macht die Verschlüsselung diese unbrauchbar und schützt sie.
Durch die Implementierung von Kontosperrungen werden wiederholte fehlgeschlagene Anmeldeversuche reduziert, wodurch Brute-Force-Angriffe schwieriger auszuführen und leichter zu erkennen sind.
Keeper verhindert Brute-Force-Angriffe, indem schwache und wiederverwendete Passwörter für jedes Konto durch starke, einzigartige Passwörter ersetzt werden. Mit MFA-Unterstützung und erweiterter Überwachung verhindert Keeper unberechtigten Zugriff und alarmiert IT-Administratoren in Echtzeit über verdächtige Aktivitäten. Durch die Kombination von Zero-Knowledge-Verschlüsselung mit Durchsetzungsrichtlinien hilft Keeper sowohl Einzelpersonen als auch Organisationen dabei, Brute-Force-Angriffe zu verhindern, bevor sie zu umfassenden Datenpannen führen.
Sie müssen Cookies aktivieren, um den Live-Chat zu nutzen.