The main difference between an attack vector and an attack surface is that an attack vector is the specific way a cybercriminal can take advantage of
The Internet of Things (IoT) refers to the network of physical objects – “things” – that connect and share data with the internet, other IoT devices and the cloud. IoT devices are often embedded with sensors, software and other technologies to exchange data with other devices and systems when connected to the internet. IoT devices include smart home devices like doorbell cameras and light bulbs.
Continue reading to learn more about IoT devices, how they work, their importance, examples of IoT devices and how you can secure your IoT devices from cyber threats.
How Does IoT Work?
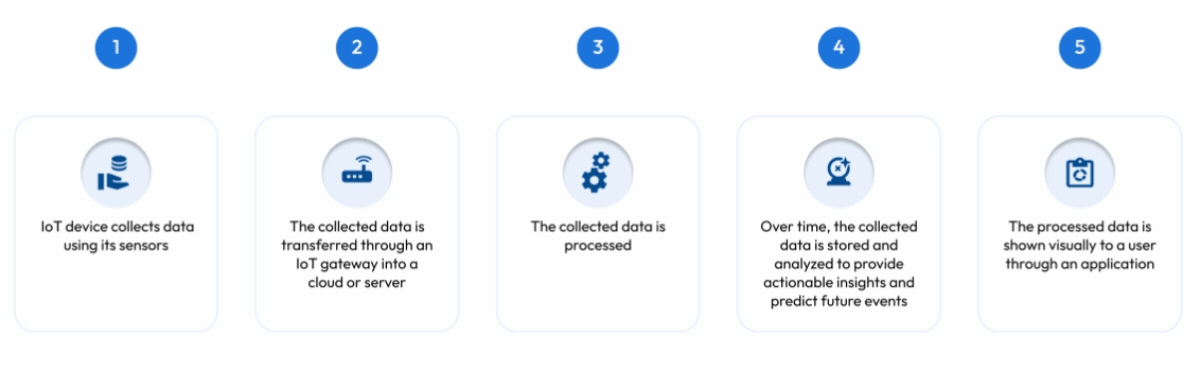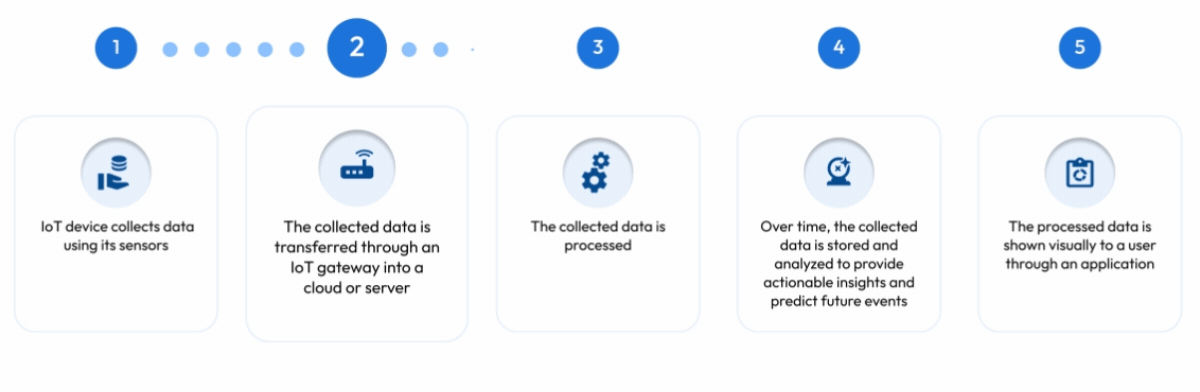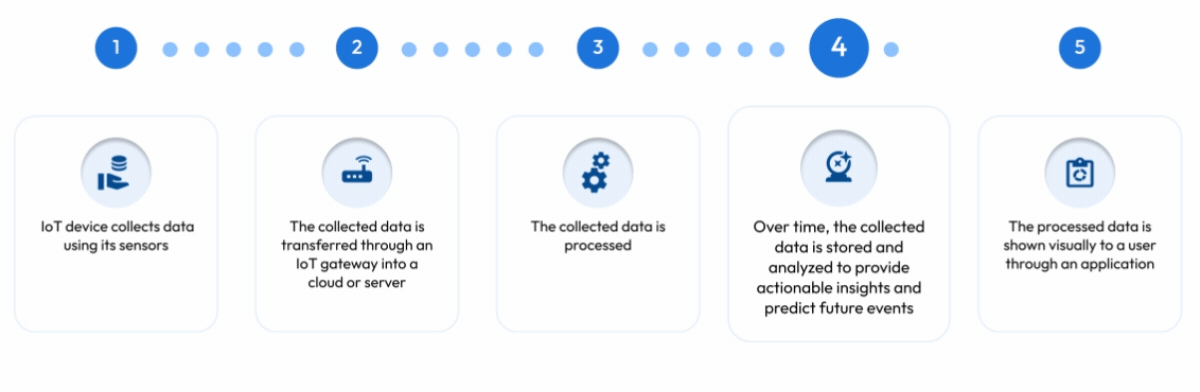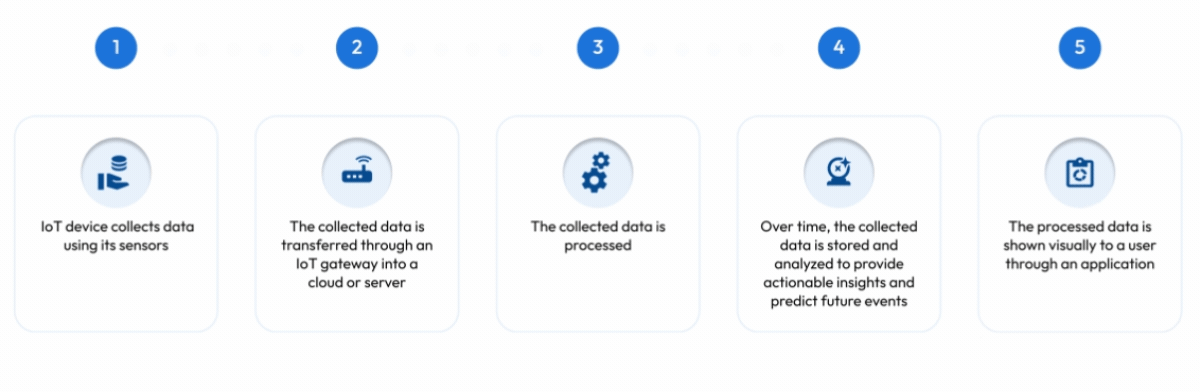
While different IoT devices have their own functionality, they typically work similarly to one another. Once an IoT device is set up and connected to the internet, it uses its sensors to collect data. For example, a smart thermostat may collect data about the current temperature of a room. When data has been collected, it is transferred through an IoT gateway so it can be analyzed. Continuing with the smart thermostat example, the IoT platform will process the data to check if the temperature is within an acceptable range of what it should be. Once the data has been processed, the data is stored in the cloud or a server and then sent to the user. The user will be able to see the processed data through an application that works with the IoT device.
As more data is collected and stored by the IoT device, it’s able to be used to provide actionable insights and predict future events that will make someone’s life easier. For example, a thermostat will be able to tell when the temperature in a room goes above or below the range it’s set at and take action by starting the heating or cooling early on so the temperature remains at an acceptable level.
The Importance of IoT
IoT devices are important for organizations and individuals because they can improve productivity and make our lives easier. Because IoT devices can communicate with one another, they work together to gather information that can be useful for future events.
For organizations of all industries, IoT devices can collect data and give them insight into what they should be doing to be more efficient, save costs and generate revenue. For example, farmers who use IoT can be given insights into the current or past weather patterns including humidity, temperature and soil conditions to determine what farming techniques they should be using to get the most out of their crops.
Examples of Internet of Things
Here are some examples of “things” that fall under the IoT, grouped by their application.
Smart home security
- Doorbell cameras
- Glass break and motion detectors
- Keypad door locks
- Biometric door locks
Smart home everyday life
- Smart thermostats
- Smart TVs
- Smart home appliances
- Smart refrigerators
- Smart ovens
- Smart coffee machines
- Smart washer and dryer
- Smart dishwasher
- Smart toilet
- Smart light bulbs
Wearables
- Smartwatches
- Monitors and trackers for healthcare
Smart driving
- Smart cars
- Navigation apps (Google Maps, Waze and Apple Maps)
Industrial
- RFID tags
- Barcode scanners
- Smart agriculture
- Warehouse automation devices
What Are Some of the Security Risks Associated With the IoT?
While IoT provides many great benefits, security risks associated with IoT need to be addressed, such as weak authentication, lack of encryption, out-of-date software, data privacy concerns and an increased attack surface.
Weak authentication
Login credentials are an IoT device’s first line of defense against hackers. If the passwords for your IoT devices and connected accounts aren’t strong, it means it’s at a greater risk of being hacked and misused for malicious purposes. While most IoT devices come with default passwords, some IoT devices don’t require authentication at all, which presents a major security risk to the data being processed and the network it’s connected to.
Lack of encryption
Encryption is when data is turned from a readable format to an unreadable format known as ciphertext. Ciphertext prevents anyone but an authorized person or system from being able to view, read or alter the encrypted data. When data is encrypted it remains encrypted until an authorized individual or system uses the encryption key (usually a password) to decrypt the data.
Encryption is what keeps sensitive data safe from unauthorized individuals. When IoT devices fail to encrypt the data they process and store, it places that data at risk of falling into the hands of cybercriminals.
Out-of-date software
Software should always be updated as soon as a new update is made available. Software updates are important because they patch security flaws and add new security features that keep your devices protected from cybercriminals. When software updates aren’t downloaded immediately, this opens up a backdoor for cybercriminals to inject malware into your device. If malware were to infect just one of your devices, it could also infect any other devices connected to the same network.
Data privacy concerns
IoT devices have raised privacy concerns because of the amount of data that is gathered by these devices and the potential for bad actors to be able to spy on people in their own homes. Baby cams, for example, have often been exploited by bad actors to spy into a victim’s home, which is a major privacy violation. In May 2023, Amazon faced a $5.8 million settlement because an Amazon Ring employee was able to view thousands of videos from at least 81 different female users. This was just one of many Amazon Ring employees who were extensively viewing customer footage without consent, according to the FTC.
Increased attack surface
Attack surface refers to all the possible entry points where cybercriminals can access and hack into a system to steal data. When an attack surface is small, it’s easier to manage and protect. The more IoT devices someone has, the greater their attack surface becomes, because of the increased number of access points and amount of information being shared between those devices. When an attack surface becomes large, the potential for a cybercriminal to steal sensitive information increases.
How To Secure Your IoT Devices From Cyber Threats
Here are a few tips that will help you secure your IoT devices from cyber threats.
Use strong credentials
Most IoT devices come with default passwords or you have to create accounts to start using them. Always change default passwords to ones that are strong and unique to prevent your device from being hacked. We recommend using a password generator when creating your passwords to ensure they always follow password best practices. The same goes for creating passwords for new accounts.
If you’re concerned about how you’re going to remember the passwords for each of your IoT device accounts, use a password manager to securely store them.
Enable MFA
Multi-Factor Authentication (MFA) is a security measure that you can enable on most accounts and applications. Instead of only having to enter your username and password, you would also have to provide another form of authentication when MFA is enabled. This prevents unauthorized individuals from being able to access your account since they won’t be able to authenticate your identity.
Disable features you don’t use
Oftentimes, IoT devices come with additional features and services that you may not find necessary. If this is the case, make sure to disable any features that you won’t be using to reduce your device’s attack surface.
Keep your device’s software up to date
Your IoT device’s software and firmware should always be kept up to date to prevent cybercriminals from being able to exploit known vulnerabilities. Most devices and applications let you enable automatic updates so you don’t have to worry about manually updating your device’s software. You can enable automatic updates by going to your device’s settings on its associated application.
Protect Your IoT Devices From Potential Cyber Threats
IoT devices are extremely useful and make the lives of everyone a whole lot easier. But just because they make life easy, doesn’t mean there aren’t security risks present. To keep yourself and your devices safe from potential cyber threats, make sure you take cybersecurity precautions to prevent them from being hacked.
Learn more about how you can keep your IoT devices safe from Internet of Things attacks.
 Cybersecurity
Cybersecurity 
