Multi-Factor Authentication (MFA) helps add an extra layer of security to accounts, but it’s important to understand that not all MFA methods are created equal in
Updated on July 3, 2023.
Supply chain attacks are a clear and present danger to organizations in all industries, but many companies underestimate this threat. To protect against supply chain attacks, organizations should establish vendor security requirements, use a zero-trust model, keep up with regular software updates and prepare an incident response plan.
Continue reading to learn more about supply chain attacks and how you can prevent your organization from being a victim of this type of cyber attack.
What Is a Supply Chain Attack?
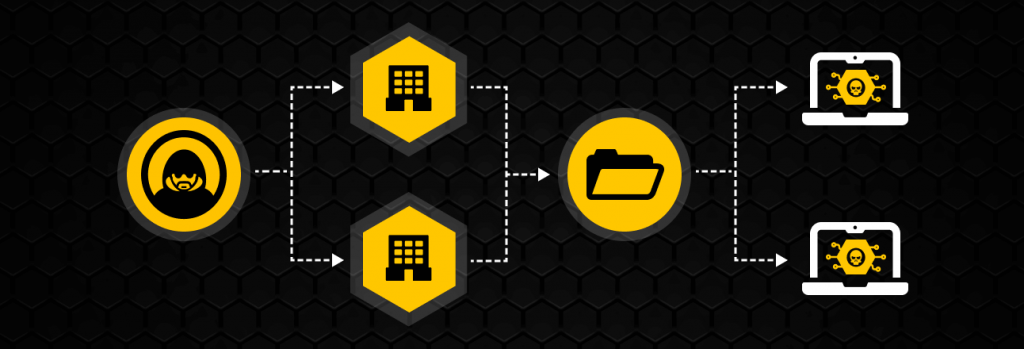
A supply chain attack is a type of cyber attack in which an organization is breached because of a vulnerability in its software or hardware supply chain. In most cases, this vulnerability is linked to vendors that have weak cybersecurity postures.
In a supply chain attack, the company that’s initially breached isn’t the ultimate target. The actual targets are the customers and business partners of that company, which is the main reason supply chain attacks often strike Managed Service Providers (MSPs), SaaS developers and other organizations that sell software and IT services. By breaching a single service provider’s network, cybercriminals gain entry into dozens, even hundreds or thousands of other organizations, including multinational firms and government agencies. The supplier, as well as the victim organizations, can suffer both financial and reputational damage that is difficult to recover from.
How To Prevent Supply Chain Attacks
While there is no way to prevent supply chain attacks altogether, there are a few steps organizations should take to mitigate the risk of supply chain attacks. Here are a few.
Establish vendor security requirements
Organizations should establish clear and comprehensive security requirements for their vendors and insist on proof that their security controls are sound. They should require that vendors hold a SOC 2 Type 2, ISO 27001 or similar security certification. These two certifications are strict security and compliance standards that demonstrate vendors can be trusted with sensitive data.
Use a zero-trust security model
Implement a zero-trust security architecture and comprehensive password security controls, including the use of strong, unique passwords for every account, enable Multi-Factor Authentication (MFA) on all accounts that support it and implement an Enterprise Password Management (EPM) system. Zero trust is a security framework that requires all users and devices be continuously authenticated before they can access systems and data.
Implement a Privileged Access Management (PAM) solution
PAM refers to how organizations manage and secure accounts that have access to highly sensitive systems and data. PAM is important for organizations to implement because employees should only have access to the systems and data they need to do their jobs and nothing more. When employees are given more access than they need, organizations are vulnerable to insider threats and breaches that leave sensitive data and systems exposed.
A PAM solution like KeeperPAM™ helps organizations prevent lateral movement within their network by properly segmenting it, and by controlling user, device and application access with Role-Based Access Control (RBAC) and least-privilege access.
Keep software up-to-date
Software, firmware and device updates are crucial to strengthening any organization’s infrastructure. These updates contain patches that fix known security vulnerabilities. When software is not updated in a timely manner, cybercriminals can exploit software vulnerabilities in order to launch cyber attacks.
Updates should be installed as soon as they are made available to prevent cybercriminals from exploiting known vulnerabilities.
Prepare an incident response plan
To be prepared for any potential supply chain attacks, organizations should have a response plan ready. An incident response plan outlines the procedures and responsibilities to follow in the event of a cyber attack or security breach at an organization.
Keep Your Organization Protected From Supply Chain Attacks
Don’t let your organization be the victim of a supply chain attack or any cyber attack. Be proactive and start taking the necessary measures needed to mitigate the risks so your organization does not have to deal with the aftermath.
Request a demo of KeeperPAM today to learn how Keeper can help your organization mitigate the risk of a supply chain attack.