The main difference between an attack vector and an attack surface is that an attack vector is the specific way a cybercriminal can take advantage of
A firewall is a type of network security system that helps protect your network from external threats by controlling incoming and outgoing network traffic. A firewall can be either software-based or hardware-based. A hardware firewall is typically a router, which is a physical device that blocks traffic from accessing the internal network. A software firewall works similarly, but is installed on your device. For instance, the Windows Firewall comes with operating systems Windows XP SP2 and later. Whether it’s software or hardware-based, a firewall is useful to enhance network security and mitigate external threats.
Continue reading to learn more about firewalls and why they’re important for mitigating external cyber threats.
How firewalls work and why they’re important
A firewall has a set of predefined rules that filter packets of data, which contains the IP address, protocols, source and ports of the users. The firewall uses the predefined rules and compares them to the packet information, deciding whether to allow or deny them into the network. Think of it as a security guard who monitors entry and exit points. A security guard makes a decision to admit or send a person home based on facility rules. In addition to this, firewalls will typically log the network information traffic so that administrators can identify any risks or threats, and monitor network activity.
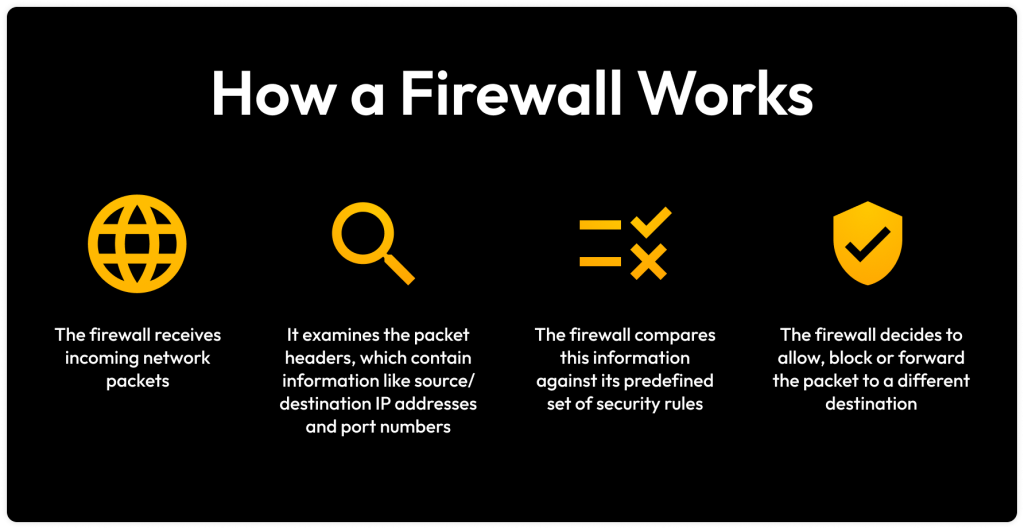
A firewall is a fundamental cybersecurity tool that implements access control policies, preventing unauthorized parties from accessing protected networks and reducing the overall risk of security breaches. By meticulously monitoring incoming and outgoing packets, the firewall protects sensitive data and information from cyber attacks.
Types of firewalls
Multiple types of firewalls provide different functionalities. Choosing one that best matches your needs will play an important role for you and your organization. Here are four of the most common types of firewalls.
Packet-filtering firewall
A packet-filtering firewall is the most traditional and basic type of firewall. Packet-filtering firewalls work at the network layer and their job is to filter individual incoming and outgoing packets by carefully examining IP addresses, protocols and port numbers of the packets. Based on the predefined rules and filtering process, the firewall will either permit or deny the packet’s entry.
Proxy firewall
A proxy firewall is a specific type of firewall that operates at the application layer, instead of operating at the network layer. The proxy firewall acts like an intermediary that deeply inspects application protocols. Its function is to establish a separate connection between the client and the internet, rather than forwarding the connection request like a traditional firewall does.
Next-generation firewall
A next-generation firewall is an advanced firewall that focuses on providing stronger capabilities to block dangerous traffic, in addition to providing traditional firewall functionalities. They go beyond inspecting the packet’s ports or protocols and instead inspect deeper into the packet’s data. Next-generation firewalls also have an application awareness feature, meaning that they can filter and control traffic over specific applications based on the data packet’s content.
Stateful-inspection firewall
A stateful-inspection firewall is a type of firewall that monitors active network connections while still controlling the incoming and outgoing traffic. It specializes in comparing the incoming data packets with previous data packets that have already entered through the firewall. The added function of keeping track of active connections ensures tighter security and enables more accurate filtering decisions.
Firewall vulnerabilities to look out for
Like any other security device, firewalls have vulnerabilities. It’s important to look out for these weaknesses and take actions to fully mitigate cybersecurity risks.
Denial-of-service attacks
Firewalls can be quite vulnerable to Denial of Service (DoS) attacks. Denial-of-service is a cyber attack with the purpose of shutting down a machine or network to disrupt its normal operations. This happens when an attacker overwhelms the firewall with a large volume of traffic, causing the firewall to either slow down or not work properly.
Insider attacks
An insider attack is a type of cyber attack originating from a user within the organization or a user who already has access to the networks and systems. An insider threat can launch an insider attack by stealing data or compromising accounts for malicious purposes. Firewalls only focus on protecting against external threats entering the network. Therefore, a firewall solution is not sufficient to prevent or detect any activities from malicious insiders who already have access to the network.
Misconfigurations
Misconfigurations are common when dealing with firewalls since they’re the result of human error. When you have an improper or poor setup of firewall rules, attackers can use this advantage to enter a network and launch attacks. Another common issue is the failure to activate all mitigation controls. If these controls are not activated, the firewall will not be used to its full potential which can pose a risk to external threats.
Secure your network with a firewall and privileged access management
With cyber threats becoming more pervasive, investing in a firewall is a proactive step for your network safety. Implementing a firewall solution will give you peace of mind and a sense of security, allowing you to navigate online without constantly worrying about threats.
However, firewalls alone will not mitigate all types of cyber threats and cyber attacks so it is imperative to implement a multi-layered security system. Investing in a solution like Privileged Access Management (PAM) can provide an extra layer of security. KeeperPAM™ enables organizations to achieve complete visibility, security, control and reporting across every user on every device to mitigate the risks of insider attacks.
Request a demo of KeeperPAM to enhance your network security.
 Cybersecurity
Cybersecurity 
