Keeper Security is pleased to announce significant improvements to the Security Audit tab of the Admin Console for business users, as well as the Browser Extension
BreachWatch is a powerful new secure add-on feature that monitors the internet and dark web for breached accounts matching records stored within your Keeper Vault.
BreachWatch delivers the most in-depth monitoring available to the public with a database of over a billion records while upholding Keepers state-of-the-art, zero-knowledge security architecture.
Overview
BreachWatch alerts you so that you can take immediate action to protect yourself against hackers. Once activated, BreachWatch continuously monitors for compromised credentials. Tracking over a billion known passwords, we are continuously adding new information as breaches are discovered on the dark web.
Signing Up
Signing up is easy. From your mobile device, navigate to the BreachWatch screen and follow the on-screen prompts. You can also purchase BreachWatch directly from the Keeper Security website.
After signup, BreachWatch performs a local scan of passwords that are currently stored in your Keeper vault. Customers get notified if any of their account information matches credentials known to be at risk.
Purchase a Keeper Plus bundle and get BreachWatch included.
BreachWatch Features
1. Customers are automatically notified if any password in your vault matches a breached password.
2. Remediation of the breached password is performed within the app by rotating the password on the site or service affected.
3. Keeper tracks the resolution history of every breached password for historical auditing.
Demo Video
Here’s a video of BreachWatch in action on iOS:
BreachWatch is also available on the Keeper Web Vault and Desktop App:
BreachWatch Security Architecture
Security Overview
BreachWatch is a Zero Knowledge architecture that uses a number of layered techniques to protect our customer’s information. In summary:
1. A secure, keyed, cryptographic hash function and anonymization (described below) are used to perform a comparison of passwords against a database of breached account information.
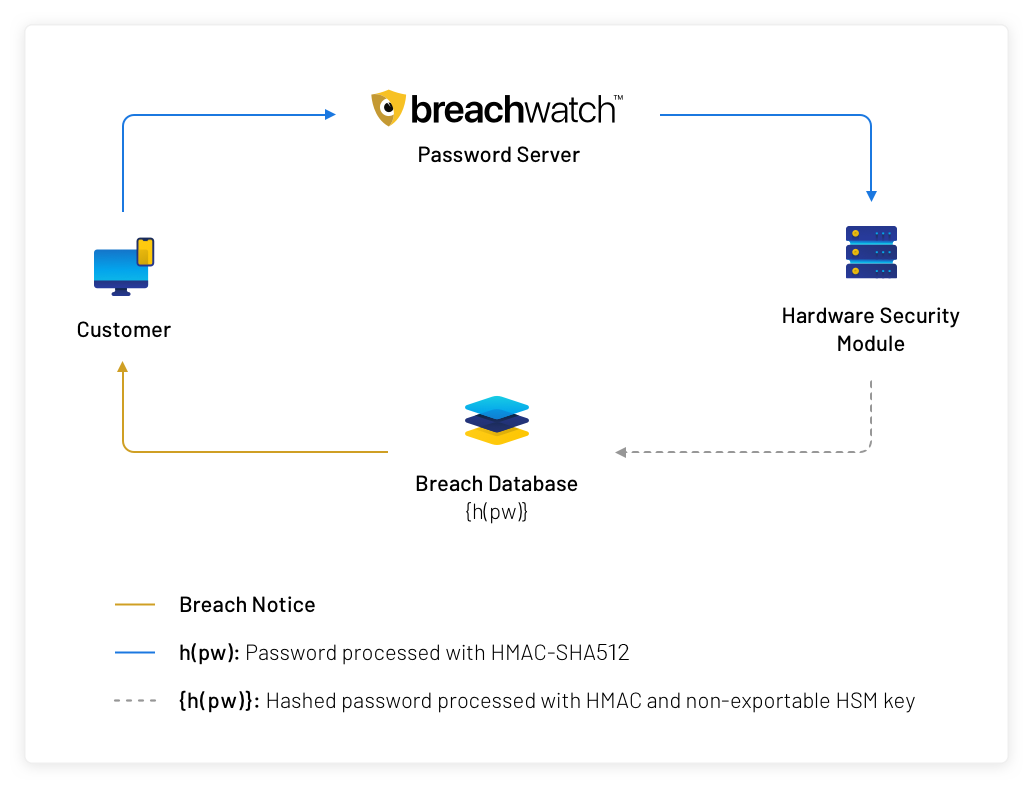
2. Customer passwords are processed with a hardware security module (HSM) and a non-exportable secret key before being checked against breached passwords or stored on BreachWatch servers.
3. Keeper customers interact with BreachWatch using anonymized BreachWatch IDs that are unlinked from other Keeper customer identifiers.
4. BreachWatch separates usernames and passwords into separate services with distinct, anonymized IDs to unlink usernames and domains from passwords.
5. BreachWatch customers never upload domain information; only downloading domains (the most secure way to perform private information retrieval).
Securely Identifying Breached Accounts
Privately comparing customer credentials against a large database of breached information is technically challenging. The solution needs to be both secure and efficiently computable given current resources including computation and bandwidth. In general, this is a concrete instance of a private set intersection or a private information retrieval problem. Keeper customers have a local database of domain names, usernames, and passwords. BreachWatch has a large database of the same items. A critical requirement of our solution is a security model that can determine which passwords are vulnerable without exposing this information to the BreachWatch service.
The simplest solution to the private information retrieval problem is for the client application to download the dataset and perform the comparison locally. This is feasible for domain comparisons (the set is small), but the set of breached usernames and passwords are over a billion data points. It would not be practical or possible to transfer this much information directly to the customer’s devices.
Techniques like encrypted Bloom filters [1] can help reduce the size of the downloads and still keep processing on the client-side in order to preserve the highest levels of data security. However, a Bloom filter created over datasets of this magnitude is still too large for most client devices. In addition, the Bloom filter would need to be refreshed each week as the breach database is updated.
Some systems use k-anonymity [2] though truncated, unsalted password hashes, but this technique is not secure. In short, instead of uploading passwords (or password hashes) to the server to perform checking, clients upload a truncated hash of each password (say, the first 20 bits) to the server. This truncated hash will match a slightly larger set of passwords which are downloaded and checked at the client device. The problem with this approach is that the size of the downloaded set matches the ambiguity of the server (or the attacker). So if a client is expected to download 100 passwords against every truncated hash uploaded, then if a client’s truncated hash is exposed (or stolen from a server), then the attacker only has 100 distinct passwords that need to be checked. If an attacker can test 5 passwords a day without locking an account, then they could gain access to an account in 20 days.
The BreachWatch Solution
To build a secure service, Keeper split BreachWatch into three services; one each for checking domains, usernames, and passwords. Keeper client applications contact each of these backend services using an encrypted REST API.
Domain Checking
Domain verification is the most straightforward solution of the three checks we perform. BreachWatch customers download a list of domains that have been breached and perform the checking locally. This is the simplest (and most secure) solution to the private information retrieval problem. And periodically, clients download updated lists of new domains as they are added to our BreachWatch service.
Username and Password
The username and password checking services are more complex because these datasets are very large. We need to test usernames and passwords offline so that customers can be alerted if a new breach has compromised an account. For these services, client devices connect to BreachWatch and upload a list of hashed usernames (or passwords) along with a client-selected, random identifier (separate identifiers for the username- and password-checking services). These password hashes are processed on upload with HMAC [3] using a hardware security module (HSM) and a secret key stored in the HSM marked as non-exportable (meaning the HSM will only process the HMAC locally and the key cannot be extracted). These HMAC’d inputs (usernames or passwords) are compared against the breach datasets which have been processed with the same HMAC and key. Any matches are reported to the client device. Any values that don’t match are stored alongside the client’s anonymized ID.
As new breached usernames and passwords are added to the system, they are processed with HMAC on the HSM, added to the BreachWatch dataset, and compared against the stored client values. Any matches queue a message for that client ID.
Clients check-in periodically to BreachWatch and present their BreachWatch IDs. Any queued messages are downloaded and clients upload any new or changed usernames and passwords which are processed the same way.
Security of the BreachWatch services is trust-on-first-use (TOFU). That is, clients must assume that the BreachWatch server is not malicious (that is, not actively compromised by an attacker) when the client uploads their hashed values. Once these values are processed with an HSM they are secured against offline cracking attempts. In other words, if an attacker steals the dataset of stored client values, she cannot crack those values offline without the HMAC key stored in the HSM.
The Industry’s Most Secure Solution
Keeper BreachWatch enables customers to identify and be alerted about accounts that are at risk due to password breaches. Performing this check in a zero-knowledge environment is extremely difficult to build, but Keeper’s engineering team prioritizes customer security over everything else.
BreachWatch is more secure than systems that store plain hashes (or truncations) or require clients to re-upload all credentials each time a new breach is discovered. BreachWatch provides both secure breach identification and strong security.
Frequently Asked Questions
What is BreachWatch?
BreachWatch is a monitoring tool that scans the dark web for stolen account credentials. BreachWatch notifies you if a password in your vault matches a password that has been identified in previous breaches.
What does it mean when a password is flagged as “High-Risk” ?
High-risk passwords have been identified in previous breaches. Hackers create “dictionaries” of these passwords and use them in their attacks. Using these passwords puts you at risk.
I thought Keeper was zero-knowledge. Do you now have access to my information?
BreachWatch is zero-knowledge and completely secure. Keeper’s employees and backend systems do not have access to decrypt or knowledge of your passwords. Please see the technical architecture section of this blog post for detailed security disclosures.
Where can I get BreachWatch?
BreachWatch is available for consumers to purchase directly through the Keeper Security website and is available for purchase on iOS and Android. On your mobile device, BreachWatch can be purchased as an add-on to your current subscription, or free users can upgrade to a bundled package of Keeper Unlimited + BreachWatch, or Keeper Family Plan + BreachWatch.
Is BreachWatch available for businesses/enterprises?
Yes – BreachWatch is available for all personal, family and Business/Enterprise customers.
Is BreachWatch free?
No. To take advantage of the continuous, unlimited scans on unlimited devices you can purchase BreachWatch as an add-on to any Keeper subscription.
How many accounts can BreachWatch monitor?
Once purchased, BreachWatch will monitor all the credentials stored in your Keeper Vault.
How do you use BreachWatch?
Once activated and purchased, BreachWatch is always scanning your account information against the database of known stolen records and will alert you within the application whenever there is a match.
How does BreachWatch differ from similar services?
BreachWatch is a zero-knowledge service that is deeply integrated with your private Keeper Vault. BreachWatch constantly scans your Keeper records against public data breaches and alerts you within your vault in real-time so you can take immediate action to protect yourself. No other service available in the market (free or paid) offers the convenience, alert speed, security and protection of BreachWatch. For more information, please read our blog post on the BreachWatch advantage.
Contact
If you have any questions regarding the Keeper BreachWatch service or security infrastructure please contact our security team at security@keepersecurity.com. Keeper Security maintains a public vulnerability disclosure program with Bugcrowd which can be accessed at https://bugcrowd.com/keepersecurity.
References
[1] Privacy-Enhanced Searches Using Encrypted Bloom Filters. https://mice.cs.columbia.edu/getTechreport.php?techreportID=483
[2] https://blog.cloudflare.com/validating-leaked-passwords-with-k-anonymity/
 Product Announcements
Product Announcements